Chinese National Sentenced to 20 Years for Laundering USD 74 Million in Crypto Scam Proceeds — Fled Before Sentencing

Key takeaways
- A US federal court this week sentenced Daren Li, a 41-year-old dual citizen of China and St. Kitts and Nevis, to 20 years in prison after he pleaded guilty on November 12, 2024 to conspiring to launder roughly USD 74 million in cryptocurrency scam proceeds.
- Pig butchering scams operate at an industrial scale. The laundering of roughly USD 74 million reflects the revenue-generating nature of organized scam centers, not isolated fraud attempts.
- Shell companies remain central to laundering pipelines.Nearly USD 60 million allegedly flowed through US shell entities before conversion into cryptocurrency.
- Flight risk is a critical factor in transnational cases. Defendants with dual citizenship, overseas infrastructure, and access to substantial illicit proceeds present materially different enforcement risks.
- Cross-border architecture complicates accountability. The same global networks that enable large-scale scams can also enable evasion once a defendant flees across jurisdictions.
{{horizontal-line}}
Sentenced — but not present
This week, the US Department of Justice announced that a federal court sentenced Daren Li to 20 years in prison for orchestrating and laundering roughly USD 74 million in cryptocurrency scam proceeds. Li, a 41-year-old dual citizen of China and St. Kitts and Nevis, pleaded guilty on November 12, 2024 to conspiracy to commit money laundering.
But he was not present for sentencing.
After pleading guilty, Li removed his electronic monitoring device in December 2024 and fled. The court imposed the 20-year sentence in absentia and ordered three years of supervised release. Li remains a fugitive.
The case highlights the industrial scale of modern pig butchering scams, the structured laundering pipelines that move illicit proceeds across borders, and the heightened flight risk posed by transnational defendants with overseas infrastructure and access to substantial illicit funds.
How the pig butchering scheme operated
According to court filings and DOJ statements, Li admitted to orchestrating an elaborate international laundering network that processed at least USD 73.6 million in proceeds from cryptocurrency investment scams targeting victims in the United States and abroad.
The fraud followed a classic pig butchering playbook. Victims were approached through messaging platforms such as WhatsApp and Telegram, where fraudsters posed as legitimate cryptocurrency investors. Over weeks or months, scammers cultivated trust and rapport before directing victims to fraudulent trading platforms, including spoofed websites designed to mimic legitimate exchanges such as “CoinZoom.”
Victims were shown fabricated dashboards reflecting significant gains. Convinced their investments were growing, many transferred increasing sums. One victim alone, identified in court documents as “Victim 1,” transferred approximately USD 1.5 million between May and August 2022 under the belief they were building legitimate crypto investments. When that victim attempted to withdraw funds, the platform demanded additional payments for supposed taxes and fees. Only then did the victim realize the funds had been stolen.
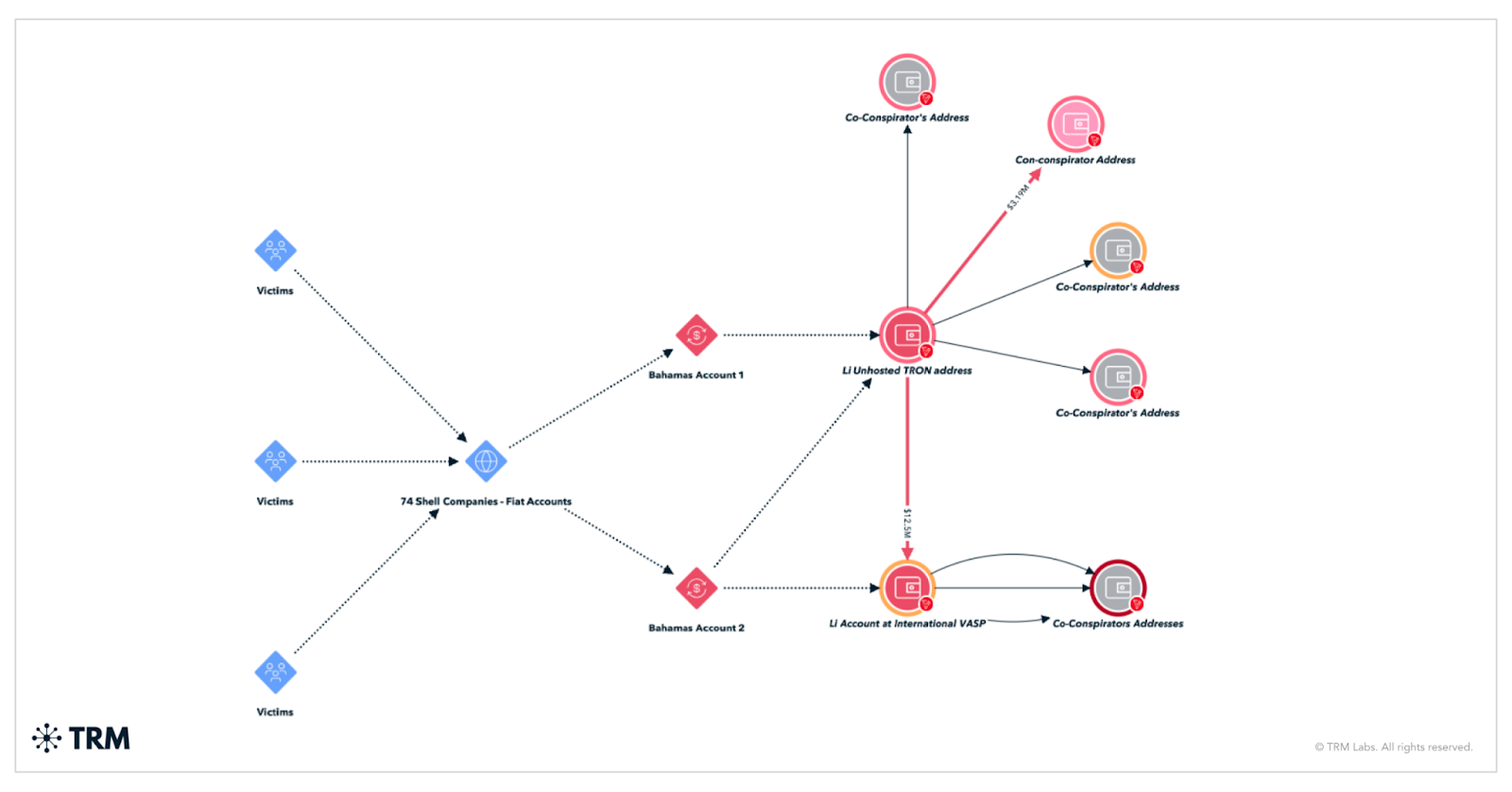
A structured laundering enterprise
Li and his co-conspirators did not rely on informal cash-outs. They built a structured, cross-border laundering pipeline. Investigators identified 74 shell companies registered in the United States with no legitimate business activity. Entities such as CMD Export and Import and Crestview Services, Inc. were used solely to receive and transfer stolen funds.
Nearly USD 60 million of the total fraud proceeds allegedly flowed through US shell companies before being converted into cryptocurrency.
More than USD 35 million moved into a Bahamas-based account identified in filings as Bahamas Account #2. That account was opened by a Los Angeles-based co-conspirator with financial backing from Li. Funds deposited there were converted into USDT, a US dollar-pegged stablecoin commonly used in cross-border crypto transactions.
Li’s own cryptocurrency account received approximately USD 4.5 million in fraud proceeds. He then transferred those funds onward to additional accounts controlled by the syndicate.
Throughout the operation, Li coordinated financial activity using encrypted messaging services, including Telegram, under aliases such as “KG71777” and “KK.” Telegram chats recovered from an iPhone seized from a co-conspirator detailed Li’s leadership role in directing shell company operations, managing transaction flows, and overseeing the broader laundering network.
Blockchain intelligence and attribution
Blockchain intelligence was central to the investigation. Agents traced victim funds from initial transfers into shell company accounts and then into cryptocurrency wallets controlled by Li and his associates.
Investigators also identified frequent logins from Cambodia to Li’s account at a global virtual asset service provider, consistent with evidence that scam centers operated there. These login records, combined with transaction tracing and connections to spoofed trading platforms, strengthened attribution.
Li was arrested on April 12, 2024 at Hartsfield-Jackson Atlanta International Airport following an investigation led by the US Secret Service, Homeland Security Investigations, and international partners in Cambodia and the Dominican Republic. Acting Assistant Director Michael Ball of the US Secret Service described the case as a demonstration of international cooperation in combating transnational crime.
Sentencing in absentia and the flight risk calculus
Li’s sentencing in absentia underscores a critical enforcement challenge in transnational financial crime cases. After pleading guilty, he cut off his electronic monitoring device and fled before sentencing.
When defendants possess dual citizenship, overseas infrastructure, and access to substantial illicit proceeds, the flight risk calculus changes materially. Once an individual crosses international borders into jurisdictions with complex or protracted extradition pathways, accountability becomes significantly more difficult. Asset recovery efforts slow. Diplomatic and legal processes may take years.
In cases involving large-scale cross-border fraud and structured laundering networks, detention and monitoring decisions can be pivotal. Once a defendant absconds internationally, the probability of swift accountability declines sharply.
Industrial-scale scam centers
The laundering of roughly USD 74 million in this case reflects more than isolated fraud attempts. It reflects organized, revenue-generating enterprises.
TRM Labs’ 2026 Crypto Crime Report found that illicit crypto volume reached USD 158 billion in 2025. Scam activity alone accounted for approximately USD 30 billion in reported volume, with underreporting suggesting higher real-world harm.
Scam centers increasingly operate as vertically integrated organizations with defined recruitment pipelines, scripted relationship-building teams, technical staff managing spoofed platforms, and structured laundering pathways that rely on shell companies, offshore accounts, and stablecoin conversion layers.
The same cross-border architecture that enables billions in illicit flows also enables evasion once actors flee across jurisdictions.
Transparency and enforcement
Blockchain technology provides transparent, permanent transaction records that support investigative tracing. In this case, on-chain analysis was critical in identifying the flow of victim funds and linking accounts controlled by Li to broader laundering infrastructure.
But tracing funds is only one component of enforcement. Effective accountability depends on coordinated international action, timely asset freezing, and the ability to apprehend responsible actors.
If you or someone you know has fallen victim to a cryptocurrency scam, report it to the FBI’s Internet Crime Complaint Center at IC3.gov and to Chainabuse.com to support ongoing investigations.
The Li case demonstrates both the power of blockchain-enabled investigations and the enforcement challenges posed by transnational actors operating across jurisdictions. It is a reminder that modern financial crime is global, structured, and increasingly industrialized — and that accountability depends as much on custody as it does on tracing.
{{horizontal-line}}
Frequently asked questions (FAQs)
1. What is a pig butchering scam?
A pig butchering scam is a long-term social engineering scheme in which fraudsters build trust with victims — often through social media or dating platforms — before convincing them to invest in fraudulent cryptocurrency platforms.
2. How much money was involved?
Court filings indicate that at least USD 74 million in victim funds flowed through accounts linked to the network. Nearly USD 60 million was routed through US shell companies before conversion into cryptocurrency.
3. What does sentencing in absentia mean?
Sentencing in absentia occurs when a court imposes a sentence even though the defendant is not physically present, typically because they have fled or failed to appear.
4. Why are transnational crypto crime cases harder to enforce?
These cases often involve multiple jurisdictions, cross-border financial flows, shell companies, and defendants with dual citizenship. Extradition processes can be complex and time-consuming..
5. Does blockchain transparency help investigations?
Blockchain transactions are recorded on public ledgers, which can support investigative tracing. However, effective enforcement also depends on cross-border cooperation, timely asset freezing, and the ability to apprehend responsible actors.






















