US DOJ Announces Largest Ever Seizure of Funds Related to Crypto Scams

Today (June 18, 2025) the US Attorney’s Office for the District of Columbia filed a civil forfeiture complaint seeking the seizure of approximately USD 225,364,961 in USDT (Tether). The funds are alleged to be the proceeds of cryptocurrency investment fraud and part of a broader money laundering scheme operating across multiple blockchain networks and exchanges. The complaint identifies specific addresses, wallets, and patterns of movement used to conceal the origins and ultimate destination of the funds.
The case involves a coordinated response from the US Secret Service (USSS) and Federal Bureau of Investigation (FBI). Tether and OKX assisted in freezing the targeted assets, which were held across seven high-value wallets, referred to as “USDT Token Groups A through G.”
TRM Labs is proud to have supported law enforcement in this investigation.
Investment fraud schemes
According to the complaint, victims were recruited through a variety of cryptocurrency scams. These schemes included fake investment platforms that mimicked legitimate trading environments, enabling victims to deposit funds, view false profit growth, and attempt withdrawals. When larger withdrawal requests were initiated, the platforms blocked access or imposed fake tax or fee requirements.
The schemes are part of what is commonly referred to as "pig butchering" — frauds in which scammers use social engineering to build trust over time before directing victims to fraudulent investment portals. Over 430 suspected victims have been identified globally, including at least 60 confirmed victims in the United States.
Movement of fraud proceeds
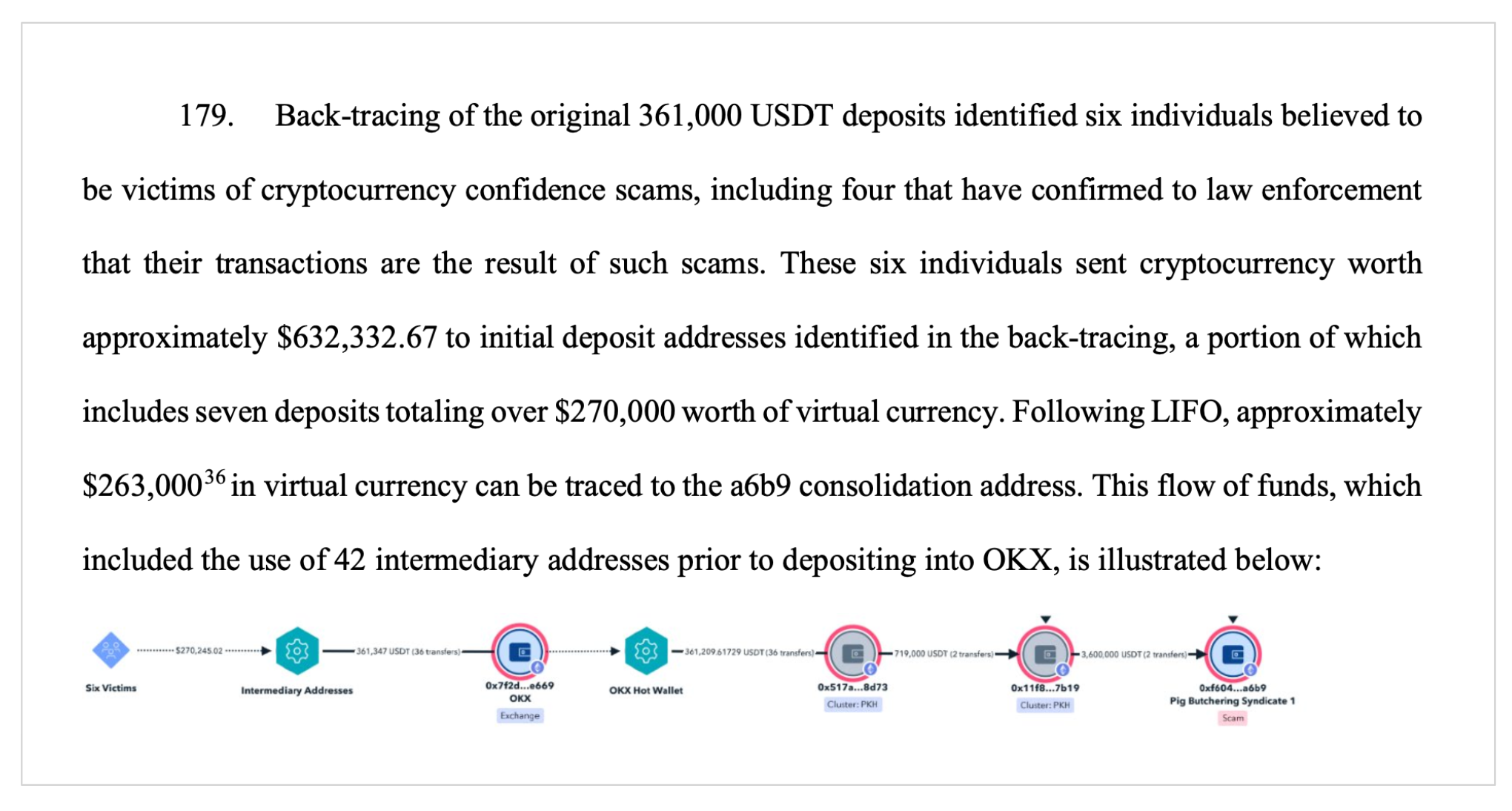
Victim funds were initially deposited into 93 known scam deposit addresses. From there, the funds were routed through multiple layers of intermediary wallets and laundering structures. These included repeated use of peel chains, structured hops, and cross-chain swaps designed to complicate tracing. The funds moved across Ethereum, Bitcoin, and TRON networks before consolidation into USDT.
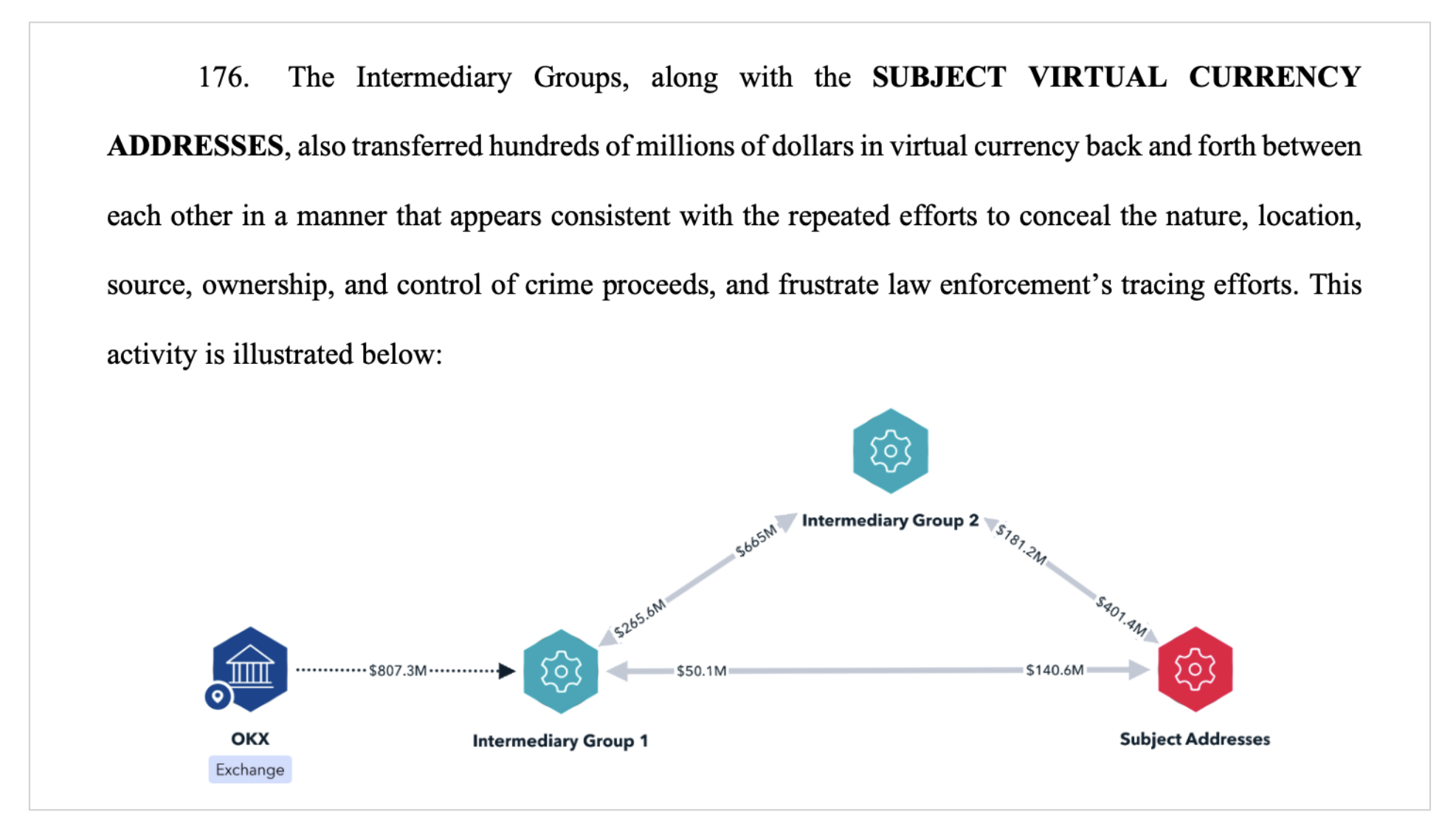
According to the seventy-five page complaint, investigators applied the “Last-In-First-Out” (LIFO) tracing method to track victim funds from initial entry points through intermediary addresses and into identified laundering hubs. Funds were ultimately consolidated into 35 intermediary wallets, and from there, moved into seven USDT wallet groups labeled A through G. These seven groups held a combined total of over USD 225 million in USDT.
Laundering infrastructure
The complaint identifies 144 accounts at the virtual currency exchange OKX that were used as part of the laundering operation. These accounts exhibited patterns of coordinated activity, including the use of Vietnamese KYC documents, overlapping IP addresses geolocated in the Philippines, and KYC photographs taken in the same physical setting.
According to the complaint, the accounts shared similar email naming conventions and often accessed the OKX platform from the same devices. The laundering network structured transactions to incur unnecessary gas fees — between USD 25,000 and USD 125,000 in total — suggesting deliberate efforts to disrupt transaction pattern recognition and tracing.
After movement through OKX, funds were routed into seven final consolidation wallets. Each of these USDT Token Groups held large sums of illicit funds:
- Group A held approximately USD 135 million
- Group B: USD 71 million
- Group C: USD 102 million
- Group D: USD 3 million
- Group E: USD 77 million
- Group F: USD 65 million
- Group G: USD 59 million
Tracing from victims to final wallets
The complaint includes several case studies illustrating full tracing from victim wallets to the USDT Token Groups. In one example, a victim transferred funds to a known scam address which, after 11 hops through the blockchain, arrived in an OKX account. The funds then moved through additional layers before reaching a final consolidation wallet.
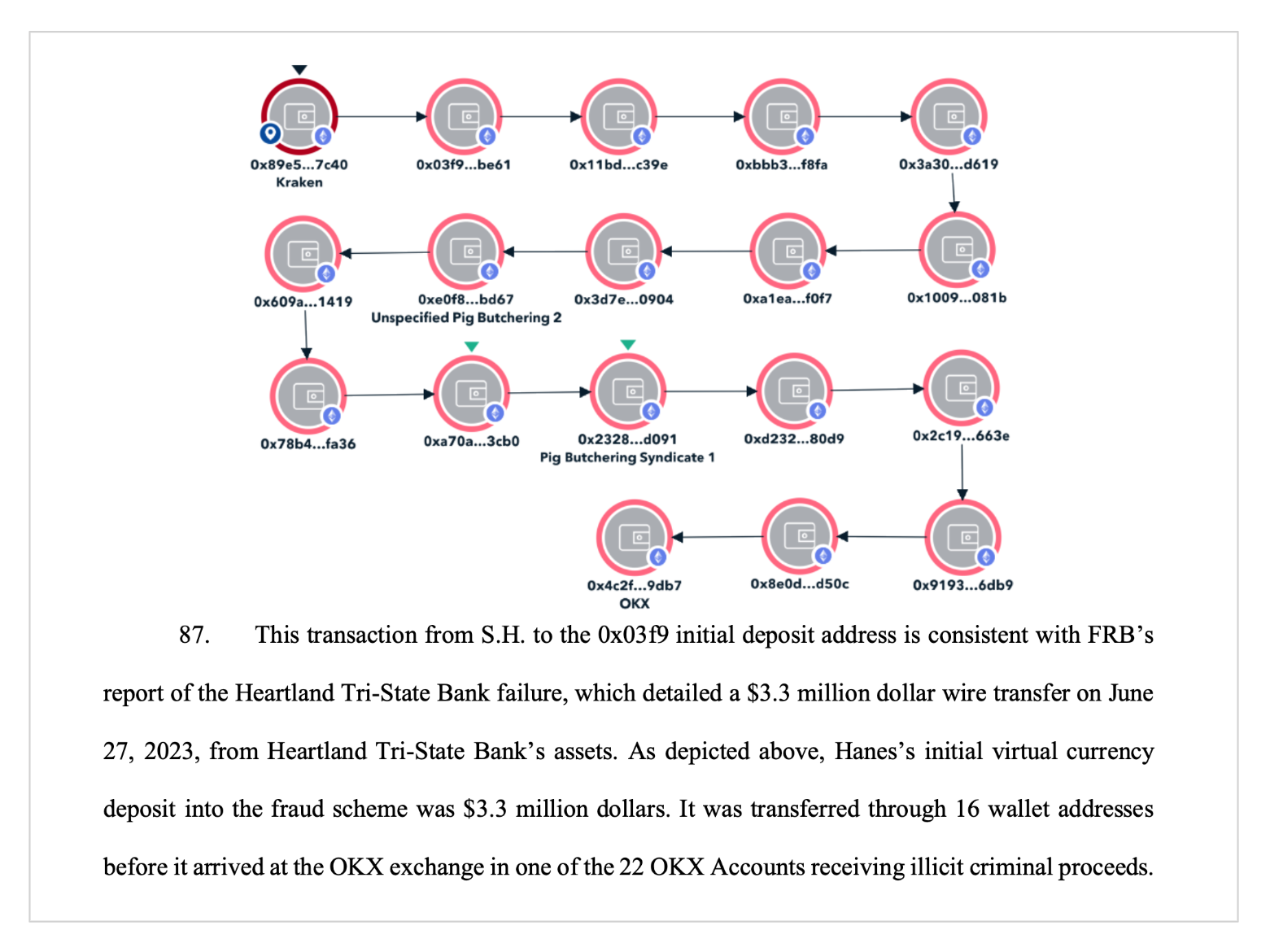
In another case, S.H., the former CEO of Heartland Tri-State Bank in Elkhart, Kansas, embezzled approximately USD 47.1 million from the bank’s assets to invest in what he believed were legitimate cryptocurrency opportunities. In reality, the platforms were part of a broader cryptocurrency confidence scam. According to the Federal Reserve Board, S.H. wired nearly USD 50 million as part of the fraudulent investment scheme.
Investigators used blockchain intelligence to follow the flow of funds from S.H.’s account, which sent 3,116,350 USDT on June 28, 2023, to an initial fraud-linked deposit address. This transaction aligns with a USD 3.3 million wire transfer described in the Federal Reserve’s report on the bank’s collapse. The funds moved through 16 intermediate wallet addresses before reaching one of 22 illicitly controlled OKX accounts. The target OKX address, beginning with 0x4c2f, received the laundered proceeds through 17 transactions and ultimately funneled virtual currency to intermediary wallets and two subject addresses at the core of the government’s forfeiture case. The laundering process used classic peel chain methods — incrementally transferring smaller amounts with each hop to obscure the origin — reducing the final amount by the time it reached its destination.
Legal basis for forfeiture
The United States seeks civil forfeiture under two statutes
- 18 U.S.C. § 981(a)(1)(A) — which allows forfeiture of property involved in money laundering
- 18 U.S.C. § 981(a)(1)(C) — which permits forfeiture of proceeds traceable to wire fraud
Each wallet targeted in the forfeiture action is alleged to contain directly traceable fraud proceeds or funds commingled and laundered with the intent to disguise their origin. The complaint includes evidence of coordinated account control, fund aggregation, and behavioral indicators consistent with money laundering networks.
Asset freeze and seizure
According to the complaint, following identification and confirmation of the fraud flows, the seven wallets holding the illicit USDT were frozen with the assistance of Tether and OKX. Tether subsequently burned the frozen tokens and reissued the equivalent value to the US government, enabling recovery of the funds under civil forfeiture provisions.
The complaint is accompanied by a request to forfeit these funds to the United States, where they will be held pending adjudication and may be used for victim restitution.
Investigation
The civil action was announced by US Attorney Jeanine Pirro who stated, “The US Attorney’s office for the District of Columbia is taking a leading role in the fight against crypto-confidence scams, partnering with law enforcement throughout the country to seize and forfeit stolen funds and rip them from the hands of foreign criminals, all with the eye toward making victims whole.”
“This seizure of USD 225.3 million in funds linked to cryptocurrency investment scams marks the largest cryptocurrency seizure in US Secret Service history,” said Special Agent in Charge Shawn Bradstreet of the US Secret Service’s San Francisco Field Office. “These scams prey on trust, often resulting in extreme financial hardship for the victims. The US Secret Service, FBI, and our private partners worked diligently to trace these illicit transactions, identify victims and seize these funds so that they can eventually be returned to their rightful owners.”
This case is being investigated by Assistant US Attorneys Kevin Rosenberg and Rick Blaylock, Jr., of the U.S. Attorney’s Office for the District of Columbia, and Trial Attorneys Stefanie Schwartz and Ethan Cantor of the Justice Department’s Computer Crime & Intellectual Property Section (CCIPS).
If you believe you are a victim of cryptocurrency investment fraud, you can report the incident to Chainabuse, a free and public platform for reporting crypto scams. You should also file a report with the FBI’s Internet Crime Complaint Center at www.ic3.gov.
Access our coverage of TRON, Solana and 23 other blockchains
Fill out the form to speak with our team about investigative professional services.






















