US Treasury Sanctions Russian National and Entities Supporting North Korean IT Worker Scheme

On August 27, 2025, the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced sanctions against a network of individuals and entities supporting North Korean overseas IT worker operations. Russian national Vitaliy Sergeyevich Andreyev was designated for facilitating payments to Chinyong Information Technology Cooperation Company, an organization previously sanctioned by the US and linked to the DPRK Defence Ministry, which employs IT workers in Russia and Laos. According to the Treasury Department, Andreyev has worked closely with Kim Ung Sun to convert over USD 600,000 in cryptocurrency into US dollars since at least December 2024.
The designation also included two companies that helped facilitate financial flows for the Chinyong network:
- Shenyang Geumpungri Network Technology Co., Ltd. — a front company in China supporting Chinyong’s operations
- Korea Sinjin Trading Corporation, a DPRK entity subordinate to the Ministry of People’s Armed Forces General Political Bureau
How does North Korea leverage IT workers?
North Korea continues to rely on overseas IT workers to generate revenue in support of its prohibited weapons programs — in direct violation of US and United Nations sanctions. These operatives often assume false identities, use fraudulent documentation, and exploit legitimate employment opportunities at companies around the world, including in the US. Wages earned by these workers — amounting to hundreds of millions of dollars — are largely seized by the DPRK regime to fund its sanctioned activities. In some cases, DPRK-affiliated workers have also deployed malware to steal sensitive intellectual property from company networks.
On-chain activity and continued monitoring
OFAC identified one cryptocurrency address associated with Andreyev as part of this designation. TRM Labs is currently investigating on-chain activity tied to the address and will continue to monitor for any behavioral overlap with previously known DPRK-linked networks.
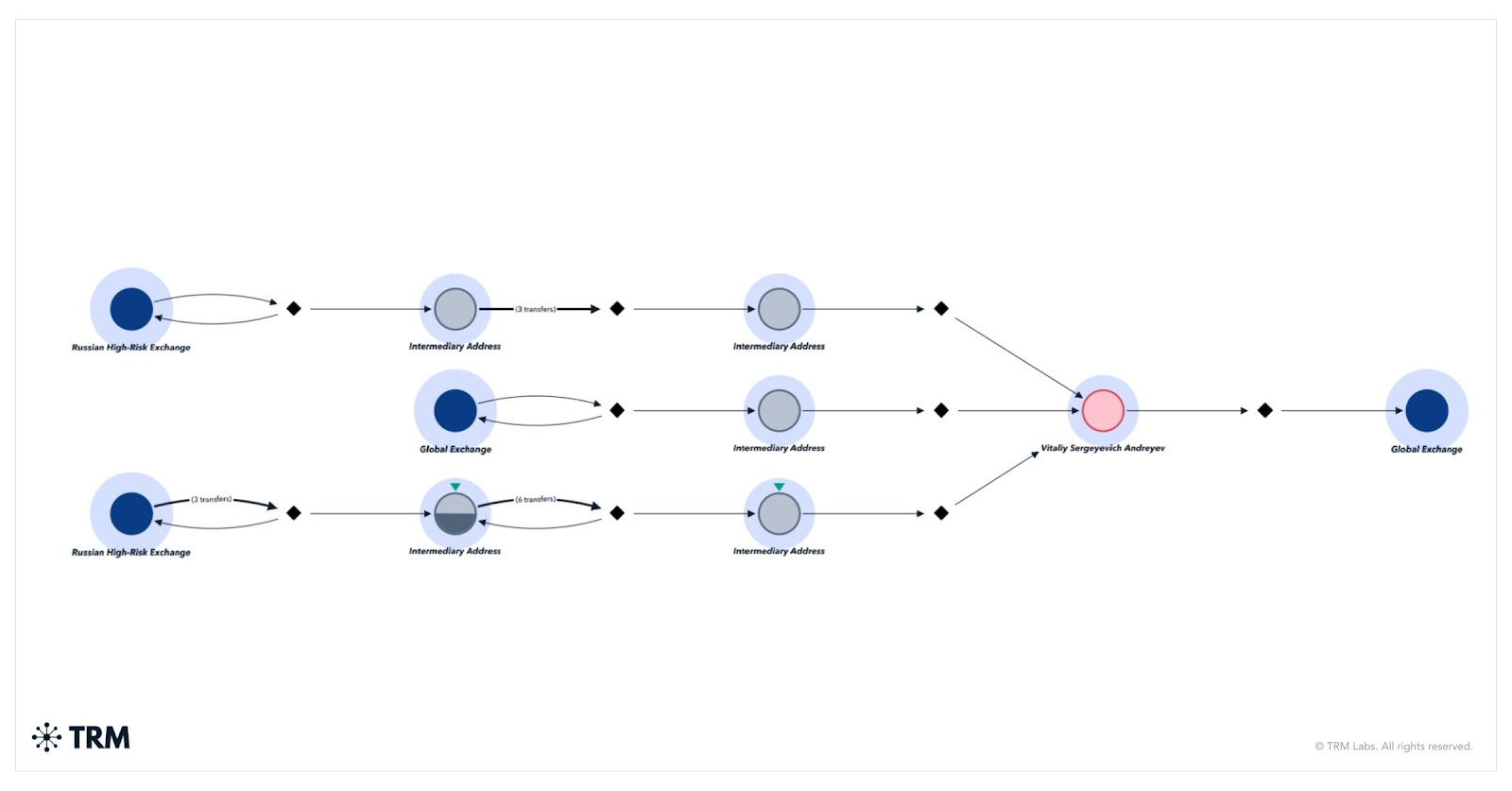
Today’s designation builds on previous US law enforcement actions targeting DPRK-linked enablers operating across Russia, China, and South East Asia. Such actions include OFAC’s July 8, 2025 designation of a North Korean cyber facilitator linked to the IT worker scheme, who is alleged to have laundered millions in stolen crypto through front companies and over-the-counter (OTC) brokers.
Crypto remains a critical tool in the DPRK’s sanctions evasion strategy, particularly when combined with front companies and cross-border facilitators. Today’s action provides further visibility into that ecosystem — and highlights the importance of screening for indirect exposure to entities involved in North Korea’s overseas IT operations.
{{horizontal-line}}
Frequently asked questions (FAQs)
What are the latest US sanctions related to North Korea’s IT worker scheme?
The US Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced new sanctions targeting individuals and entities supporting North Korea’s overseas IT worker operations. Russian national Vitaliy Sergeyevich Andreyev was designated for converting over USD 600,000 in cryptocurrency into US dollars on behalf of Chinyong Information Technology Cooperation Company — a previously sanctioned DPRK entity linked to the country’s defense ministry. Additional designations include a Chinese front company and a DPRK state trading corporation that facilitated financial flows tied to this network.
How is cryptocurrency used to support North Korean threat finance?
Cryptocurrency remains a core enabler of North Korea’s sanctions evasion strategy. In this case, Andreyev allegedly worked with a DPRK consular official in Russia to convert digital assets into fiat currency, supporting a network tied to North Korean IT workers abroad. These techniques help DPRK-linked actors obscure the origin of funds, move value across borders, and sustain operations that ultimately finance the country’s weapons programs — often without immediate detection by traditional financial systems.
What role do front companies play in North Korea’s IT worker scheme?
Front companies are essential to the DPRK’s ability to conceal and operationalize its IT worker scheme. Shenyang Geumpungri Network Technology Co., Ltd., based in China, was identified as a cover for DPRK IT worker delegations that generate revenue for Chinyong and other sanctioned entities. These companies often appear legitimate to employers or financial institutions, allowing them to mask the true origin of funds and the involvement of DPRK state actors behind the scenes.
Why should organizations be concerned about indirect exposure to DPRK-linked networks?
Organizations may unknowingly contract with IT workers operating on behalf of the DPRK, especially when those workers use stolen identities or are hired through third-party platforms or shell companies. This indirect exposure carries legal, financial, and reputational risk — particularly if funds or services flow to sanctioned entities. Today’s OFAC designations underscore the importance of enhanced due diligence and blockchain intelligence to identify behavioral patterns that may indicate hidden links to North Korean operations.
How is TRM Labs supporting investigations into DPRK crypto activity?
TRM Labs is actively monitoring the cryptocurrency address identified by OFAC in this latest action and is assessing whether it exhibits behavioral overlap with other wallets tied to known DPRK-linked campaigns. Through on-chain analysis and partner collaboration, TRM supports efforts to detect and disrupt illicit finance associated with sanctioned actors. This includes surfacing red flags linked to front companies, facilitators, and cyber activity that may otherwise go undetected by traditional monitoring tools.






















