Detecting Five Common Sanctions Evasion Techniques: A guide for crypto compliance teams
Common sanctions evasion techniques and how blockchain intelligence helps prevent sanctioned activity
Key takeaways
- Sanctioned actors are evolving fast — using address changes, rebrands, and layered transaction patterns to evade controls.
- Static sanctions screening alone is no longer sufficient; compliance teams need dynamic, risk-based frameworks.
- Obfuscation tactics now span VPNs, cross-chain swaps, and use of third-party facilitators — often with indirect exposure risks.
- Regulators are increasing wallet and entity designations, while enforcement penalties are becoming more severe.
- Blockchain intelligence tools like those provided by TRM enable proactive detection of hidden risk — with behavioral analytics, attribution expansion, and indirect exposure monitoring built in.
{{premium-content_chapter-divider}}
Sanctions and crypto assets have wrestled with each other since their inception. Sanctioned entities have long exploited crypto assets to circumvent financial controls, even though blockchains offer unparalleled visibility into how bad actors use them. At the center of this tussle are the businesses trying to safely operate in this space and stay ahead of rapidly evolving circumvention techniques.
In this guide, we’ll assess the trends shaping the sanctions policy landscape and what they mean for the requirements on firms; take a closer look at five common sanctions evasion techniques used by illicit actors; and highlight critical features in compliance programs and blockchain intelligence solutions in order to identify, trace, and block sanctioned activity.
<span class="premium-content_chapter">PART ONE</span>
Where are we now?
The crypto asset sanctions landscape
Efforts to limit the exploitation of the crypto ecosystem by sanctioned actors have evolved dramatically since OFAC’s first designation of a crypto wallet address back in March 2018. And in turn, so have the expectations of sanction-issuing countries on the crypto businesses they oversee. It’s unlikely that this evolution — and the need to take a dynamic approach to implementing sanctions — will slow down.
There are three key trends driving this evolution:
- We live in an increasingly complex and fragmented world
- More countries are designating wallet addresses and crypto-related entities, with an increasing number of designations
- Enforcement capabilities are becoming more sophisticated
1. We live in an increasingly complex and fragmented world
More conflict means more sanctions. And more sanctions create more sanctions evasion (and more ways to evade sanctions) than ever before.
Whether this is utilizing a new national payment system or integrating stablecoins into oil trades, value transfer is diversifying — and with it, so are the imaginative ways to cross real and virtual borders, slip under limits, and falsify information. To combat this trend, compliance teams need to be multi-disciplinary and more skilled to map the actors, networks, and strategies at play.

2. More countries are designating wallet addresses and crypto-related entities, with an increasing number of designations
In mid-2023, Japan designated its first crypto asset wallet address. This marked a turning point for the country and followed the US and UK, who have designated wallet addresses in addition to entities and legal persons for several years.
To date, the UK has over 100 designated wallet addresses, while the US has over 500. The designation of wallets is significant, as this makes it easier for entities to screen addresses and build a basic sanctions regime.
In addition to more countries designating wallet addresses and infrastructure, we’ve also seen an increase in how rapidly designations are occurring.
2023 was one of the most active years for US wallet designations yet. According to TRM, sanctions designations events rose three-fold, from 11 designation events in 2022 to 33 in 2023. Among the targets were twelve ransomware groups, six high risk exchanges, and a cryptocurrency mixing service. 2024 shows no sign of designations slowing down — and neither is enforcement of these controls.
3. Enforcement capabilities are becoming more sophisticated
Along with increased designations, the number of enforcement actions against businesses failing to implement sanctions has also been on the rise. These actions are growing more costly — running into the billions of dollars. And these numbers are expected to continue to increase.
Sanctions enforcement agencies increasingly have access to more sophisticated tools to investigate circumventions, and have said they plan to do so. For example, in the UK and EU, senior policymakers have committed to do more sanctions enforcement, especially on Russia, this year.
{{14-detecting-five-common-sanctions-evasion-techniques-callout-1}}
{{premium-content_chapter-divider}}
<span class="premium-content_chapter">PART TWO</span>
The what, where, and who
Sanctions requirements for crypto assets
Navigating sanctions requirements can feel like a daunting prospect for crypto asset businesses. There are several jurisdictions that issue sanctions and touch crypto assets in different ways — designating the assets of nationals, wallets, or all transactions to certain jurisdictions. Selecting the right sanctions screening approach can help address these complexities.
Sanctions are also a zero-sum rule. You have to follow designations to the letter and have tools in place to identify possible sanction evasion activity, which drastically expands the scope of any sanctions compliance program.
For crypto businesses, determining the scope of requirements that must be followed is further complicated by the inherently global nature of the sector. This means that even though a company might be registered in one jurisdiction, they could have teams in many others, rely on payment rails in further jurisdictions, and serve customers in literally any country in the world.
{{14-detecting-five-common-sanctions-evasion-techniques-callout-2}}
Remember, when determining which sanctions you have to comply with, a nexus to a sanction-issuing entity can come from:
- Entity registrations
- Location of employees
- Location of customers
- Location of payment rail/banking providers
- Currencies used
- Location of physical infrastructure e.g. mining rigs, servers hosting nodes
Always seek legal review if you need clarity about determining exposure, and update this advice on a regular basis.
Fitting sanctions into other financial crime obligations
Managing sanctions risk is one element of a firm's anti-financial crime (AFC) control framework, which should also include anti-money laundering (AML) and countering terrorist financing (CTF) controls.
However, another element which is sometimes overlooked or folded into a sanctions program is countering proliferation financing (CPF). CPF is an important AFC discipline, and differs from sanctions.
Proliferation financing
What is proliferation financing?
Proliferation financing refers to the act of providing funds or financial services that are used to support the development, production, acquisition, or proliferation of weapons of mass destruction (WMD) and their delivery systems.
This financing includes not only direct funding, but also indirect financial support through various means such as trade, investments, and other financial transactions that facilitate the spread of nuclear, chemical, or biological weapons and their associated technology and materials.
Why should I care about proliferation financing?
FATF recommendations mandate that all countries and the businesses they host implement rules on combating proliferation finance (See Recommendation 7 and Immediate Outcome 11).
Over the next six or so years, countries will have to, for the first time, conduct national proliferation financing risk assessments — meaning they will need to take a closer look at what their firms are doing. This will likely impact medium and large firms most, who will also be required to conduct a proliferation risk assessment, separate from sanction exposure assessments.
Unfortunately, the main proliferating states — North Korea and Iran — are well-versed in exploiting crypto assets to finance their activities. According to TRM, in 2023, North Korea stole approximately USD 700 million in cryptocurrency. The risk in this sector is elevated, and we all need to play our part in curtailing it.
Is proliferation financing the same as sanctions?
Not quite, although there are similarities. Key proliferating states like North Korea and Iran are sanctioned by the UN, comprehensively by the US, and to different extents by other countries. But the key difference is that unlike sanctions, which are zero-sum, proliferation financing can be treated with a risk-based approach. This is because proliferation activity is broader than sanctioned activity, and so requires a more flexible approach to robust map activity.
What should I do?
Having an awareness of proliferation financing risk starts with educating yourself on what this looks like. FATF has produced a guide on determining proliferation financing risks and conducting a proliferation financing risk assessment. Once you’ve completed a risk assessment, blockchain intelligence tools can be used to investigate that exposure, allowing you to put appropriate controls in place.
{{premium-content_chapter-divider}}
<span class="premium-content_chapter">PART THREE</span>
Optimizing your response
Five common sanction evasion tactics and how to combat them
At TRM, we monitor and trace across a wide range of sanctioned actors — from services based in comprehensively sanctioned jurisdictions, to specific cyber criminal groups that engage in complex laundering techniques.
Notably, sanctioned actors engage in a range of circumvention and evasion methods, with each group leveraging different tactics depending on their home jurisdiction, off-ramp strategy, likelihood of enforcement, and level of sophistication with crypto assets.
Using these insights, we’ve listed five common characteristics of sanctions evasion tactics that compliance officers should be aware of and build controls around to bolster their sanctions programs.
{{14-detecting-five-common-sanctions-evasion-techniques-callout-3}}
1. Changing and creating new addresses
The speed of blockchain technology is not just about the rapid transfer of funds from one wallet address to another with instantaneous settlement. It also relates to the speed in which new wallet addresses can be created.
This may be done for benign, operational reasons within Virtual Asset Service Providers (VASPs) — for example, where they may enable users to create a large number of wallet addresses with the same seed phrase to manage accounts efficiently. Or it may be done for illegitimate reasons by sanctioned entities to generate fresh, un-designated addresses. Those “untainted” addresses can then be leveraged to facilitate a limited set of transfers before being discarded, and new addresses created again in a continuous cycle — with the aim of making it harder to track transactions and pinpoint sanctions exposure.
Compliance insight: Screening names and addresses frequently
The on-chain footprint of sanctioned actors is consistently evolving. If sanctions screening practices are limited to only screening against a stagnant list of addresses explicitly designated by sanctions authorities, these screening procedures are likely to be ineffective.
To combat this, screening processes should not only include listed addresses and designated names, but should also happen on a more frequent basis than customer onboarding and infrequent periodic reviews alone. While sanctions authorities like OFAC don’t prescribe the exact cadence an institution should screen on, they do advise a risk-based approach; choosing appropriate sanctions screening tools can support this. And of course, the more likely your business is to be exposed to new addresses (e.g. via withdrawals, deposits, linking wallets, etc.), the more frequent your screening processes should be.
Given the revolving door of wallet addresses that sanctioned actors may use, the ability for your blockchain intelligence tool to have robust and automated attribution expansion capabilities becomes paramount when choosing a provider. Tools that only generate sanctions labels for a limited set of explicitly designated addresses or basic clustering methods are unlikely to capture the larger and more accurate sanctioned footprint.
The example below shows an Iranian entity (red nodes) that created a mass amount of new addresses in order to facilitate deposits at a single exchange (green nodes). The entity inside Iran also created multiple deposit addresses at the exchange to spread out the deposit activity.
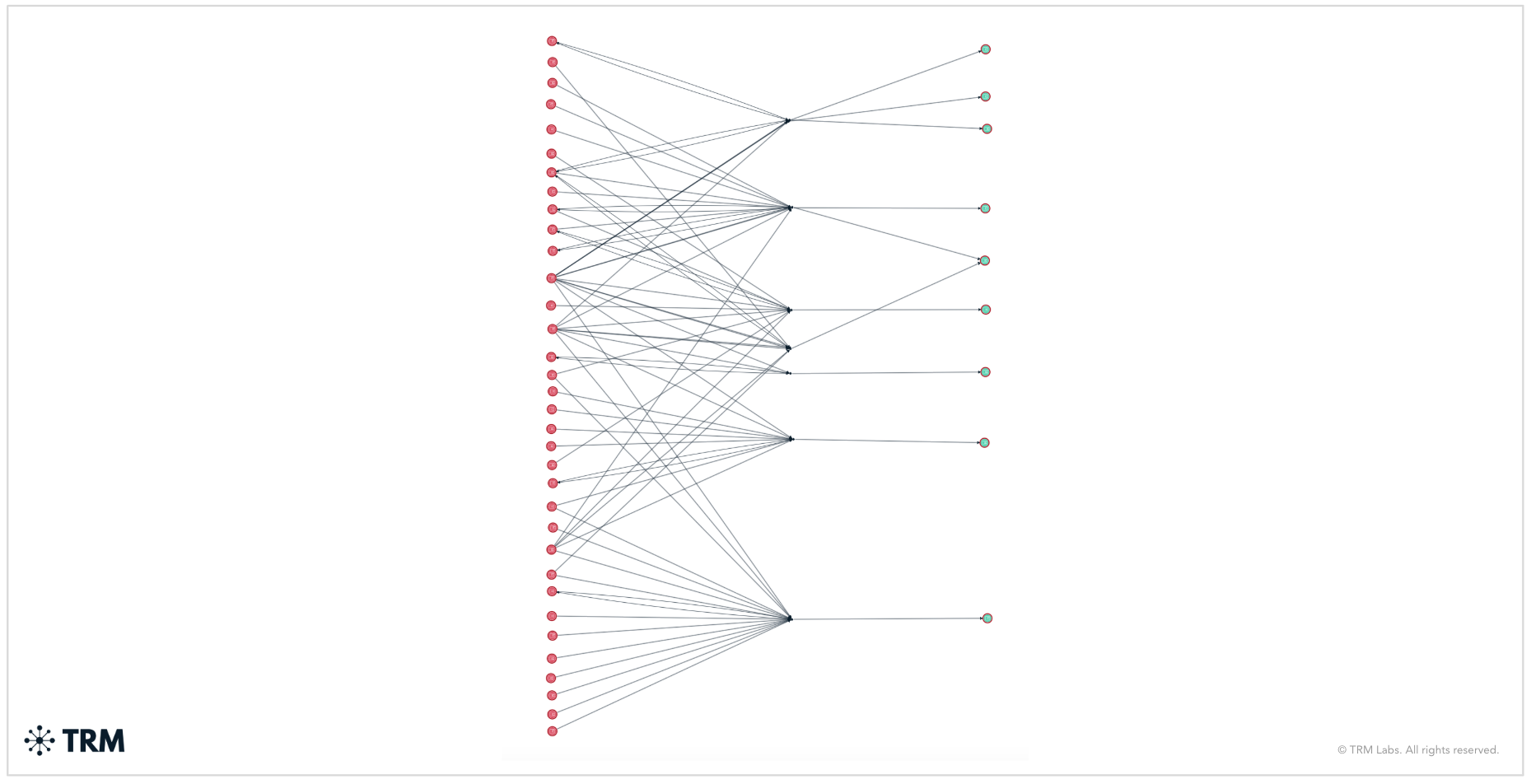
The ease at which wallets can be created and used to layer the flow of funds by sanctioned entities can also create instances where sanctions exposure may be indirect to your institution. Generally, regulatory bodies have not issued specific guidance on screening for indirect sanctions risk, and compliance officers are likely to grapple with questions like, “How many hops equals actionable sanctions exposure?”.
Screening for all instances of indirect sanctions risk may also result in processes that are challenging to scale, or a large number of gray area cases where it isn’t clear whether the institution has a blocking and reporting obligation.
Compliance insight: Risk-based approach to indirect risk
As in many gray areas in crypto compliance, working from first principles can be instructive.
For instance, a risk-based approach to indirect risk may lead an institution to focus on forms of enhanced screening for higher risk clients. Other enhanced procedures may include periodic assessments of potential indirect sanctions risk to ascertain the validity of that risk at your institution. Additionally, blockchain intelligence firms like TRM have the ability to conduct sandbox risk assessments, where institutions are able to see their exposure to indirect risk at a macro level. This helps them determine whether additional controls are needed to screen and/or block indirect sanctions risk across certain customer groups.
For more details, check out TRM’s guide to investigating indirect risk here.
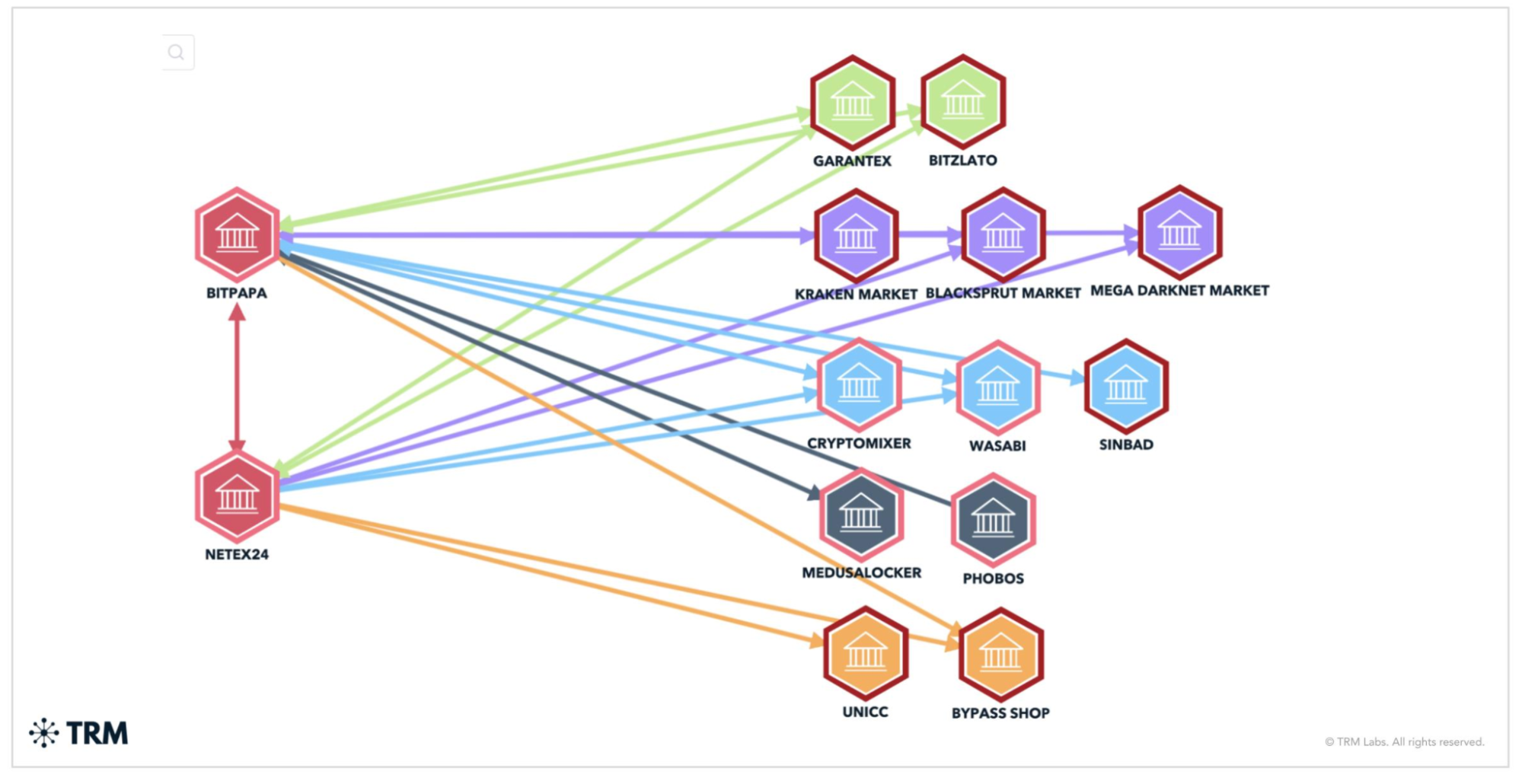
2. Changing names
Another evasion tactic — and one not limited to crypto — is the practice of changing the legal name of an entity or service after it has been sanctioned. This evasion technique is used to circumvent name-list-based screening procedures, and has long been used outside of the crypto context by sanctioned entities.
TRM’s threat intelligence group has now identified similar tactics with crypto entities.
{{14-detecting-five-common-sanctions-evasion-techniques-case-study-1}}
Compliance insight: Sanctions intelligence and retroactive reviews
Identifying sanctioned entities who have changed their names and continue to use your crypto business can be exceptionally challenging to detect with a screening-only sanctions program. Blockchain intelligence tools with a proactive threat intelligence collection apparatus that can identify these types of tactics are critical, as traditional screening controls alone may be insufficient.
Additionally, retrospective screening and sanctions-focused investigations may be a helpful supplement to your sanctions framework. OFAC’s Sanctions Compliance Guidance for the Virtual Currency Industry indicates these two potential measures can bolster the strength of your program and help you avoid more serious sanctions penalties. This guidance includes a reference to “risk-based rescreening,” where an institution can conduct historical lookbacks to account for updates to customer information or behavior that has changed, but may still present exposure risks.
Additionally, OFAC suggests that investigative software, such as blockchain intelligence tools, may help to “continually review historical information for such addresses or other identifying information to better understand their exposure to sanctions risks and identify sanctions compliance program deficiencies.”
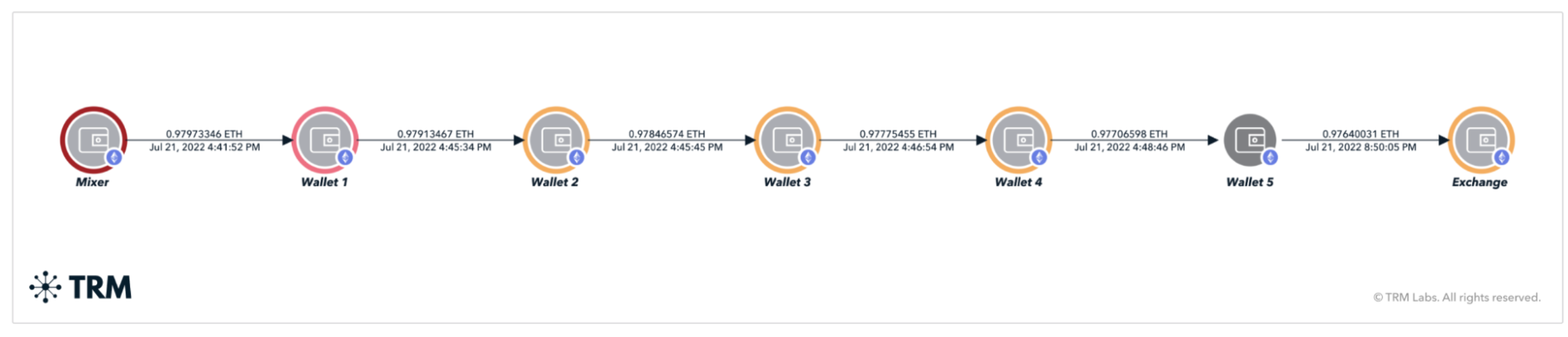
3. Evasive transaction patterns
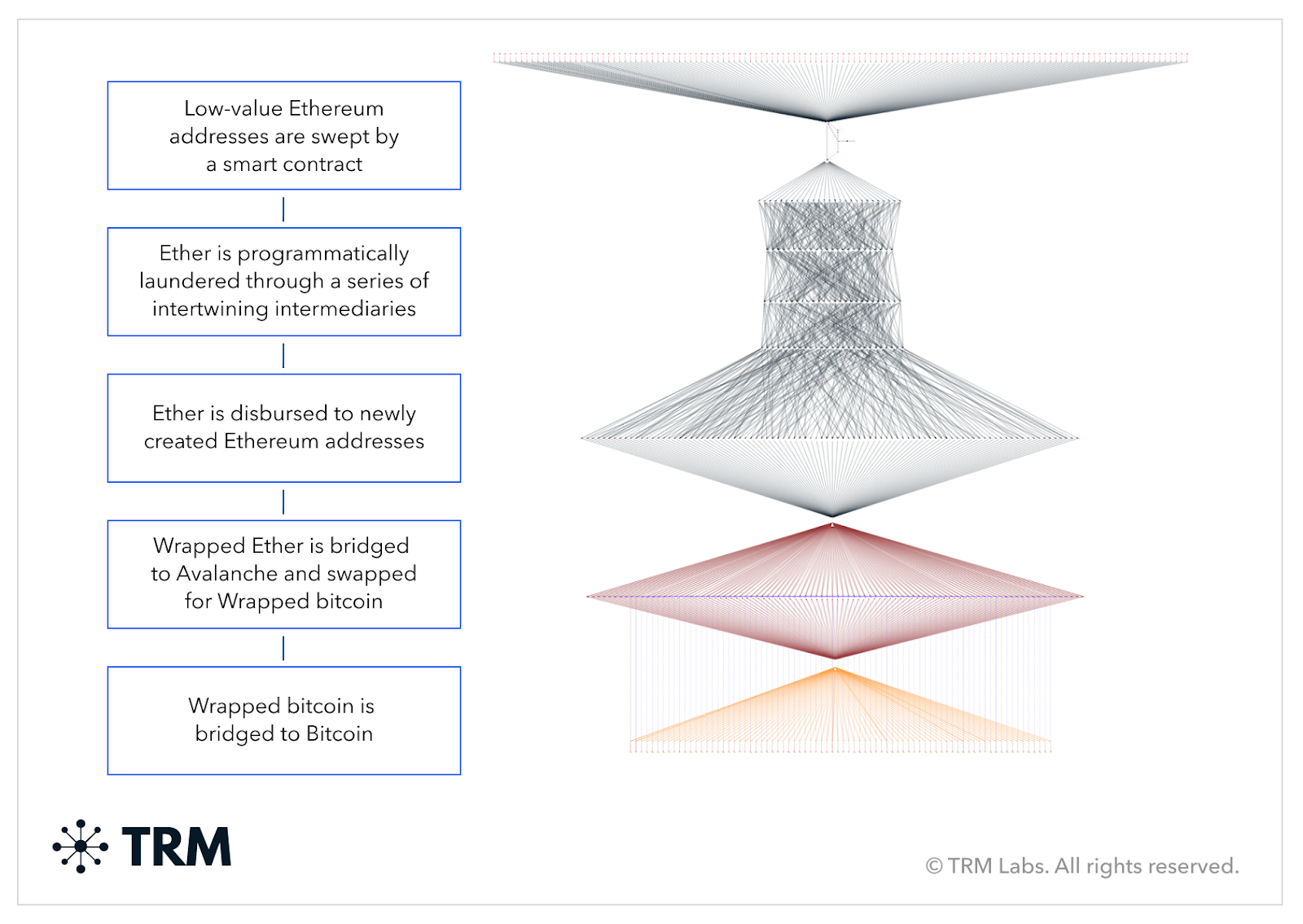
As sanctioned entities conduct their on-chain transactions, they will naturally engage in transactional obfuscation techniques to avoid detection. This extends from Iranian exchanges and crypto traders (who use western exchanges for better trading liquidity or arbitrage opportunities) to North Korean cybercriminal groups (who hack and steal funds from protocols and engage in complex patterns of layering transactions to obfuscate their trail — for example, through cross-chain swaps or the use of mixers — while searching for an off-ramp).
There are myriad ways to engage in on-chain obfuscation patterns, from mixing services to the use of more regulated services such as OTC desks, exchanges, and payment processors.
{{14-detecting-five-common-sanctions-evasion-techniques-case-study-2}}
Compliance insight: Identifying obfuscation tactics
As sanctions compliance programs scale alongside their business’ risk exposure, basic screening procedures will never catch a sanctioned actor engaging in these more sophisticated patterns. To effectively detect and prevent these illicit flows to your institution, the sophistication of your controls has to match the sophistication of the sanctioned actors.
To counter this threat, blockchain intelligence tools like TRM have developed capabilities to detect behavioral patterns used by bad actors. This includes the use of cross-chain swaps (as referenced in the Atomic Wallet Hack scenario above), but also extends to additional behavioral obfuscation patterns. The automatic detection and flagging of these behavioral anomalies allows compliance officers and investigators to efficiently identify not only that an obfuscation pattern is being used, but trace the source and destination of those flows to help ultimately decipher any nexus to sanctioned actors and/or links to suspicious activity.
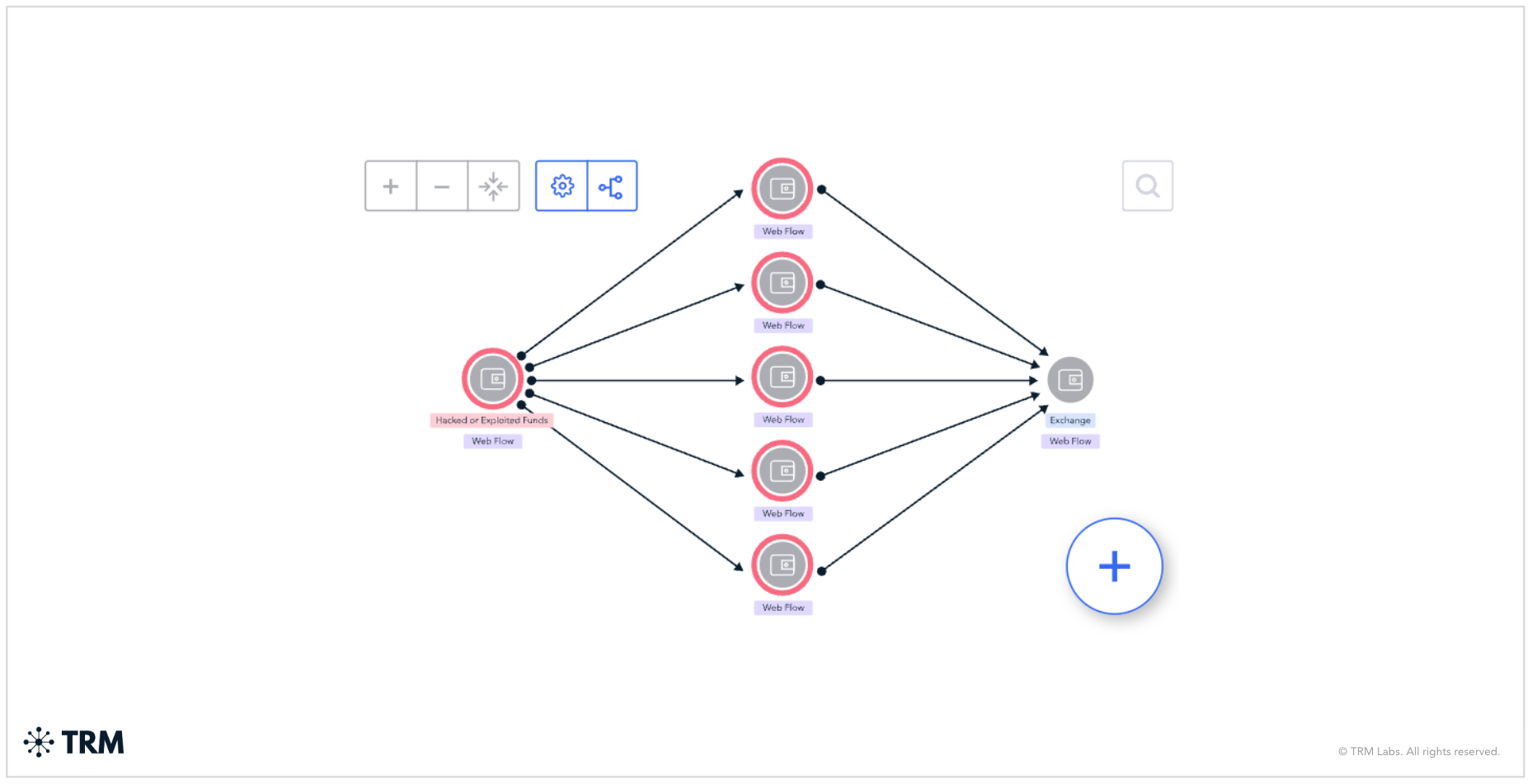
4. Use of third party facilitators or intermediary countries and institutions
Sanctioned entities have long leveraged third-party facilitators to evade sanctions controls. Those facilitators range from financial institutions based in neighboring countries with lax enforcement frameworks, to non-compliant cryptocurrency exchanges, to individuals working on behalf of a sanctioned regime. These facilitators ostensibly provide a clean set of names, accounts, and gateways for converting cryptocurrency into fiat currency or other assets without stringent checks — aiding in the evasion of sanctions.
{{14-detecting-five-common-sanctions-evasion-techniques-case-study-3}}
Compliance insight: Identifying evasion facilitators
The B-Crypto example demonstrates that even if an entity isn’t sanctioned, it might still be facilitating sanctions evasion. To have full awareness of these high-risk entities, blockchain intelligence vendors should surface both sanctioned and high-risk entities (such as exchanges) that facilitate flows to sanctioned entities.
Third parties might also be hiding in less obvious places. At TRM, we closely monitor the phenomenon of “parasite VASPs.” These make use of the architecture of a larger exchange to provide digital assets trading services to users — usually without the knowledge or consent of the host exchange. To identify parasite VASPs, you will need to analyze the on-chain volume flowing into the VASP and determine whether there are any significant counterparties that can’t logically be explained.
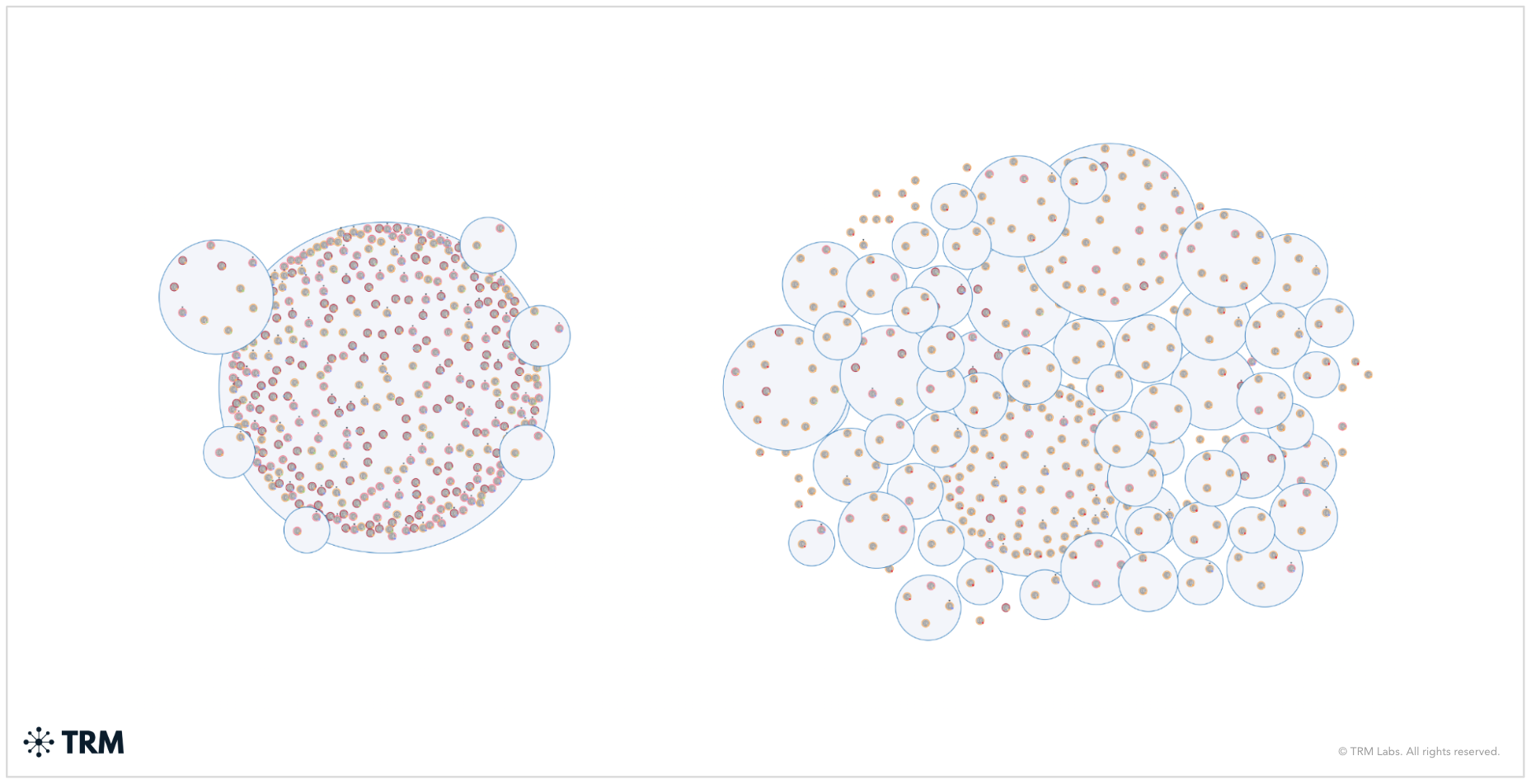
Parasite VASPs are not the only illicit facilitator to keep in mind when mapping sanctions exposure. Sanctioned actors exploit the criminal crypto underworld in creative ways to hide and realize their assets. For example, we have observed darknet marketplaces (DNMs) being used to obfuscate transactions in a similar way to mixers, which can be especially useful when mixers are under closer regulatory scrutiny.
5. Obscuring location
Sanctioned actors are increasingly using sophisticated methods to obfuscate their geographic locations to avoid detection by sanctions compliance programs. The inability for compliance programs to identify some of these tactics has led to a number of OFAC’s latest enforcement actions in the crypto space.
The use of Virtual Private Networks (VPNs) and proxy services is particularly prevalent, enabling these actors to mask their IP addresses and create the appearance of operating from jurisdictions outside their actual locations. This tactic complicates efforts to enforce sanctions, as it undermines the ability of compliance teams to accurately assess the risk associated with specific transactions or customers who may reside in sanctioned jurisdictions.
{{14-detecting-five-common-sanctions-evasion-techniques-case-study-4}}
Compliance insight: Enhance IP and location screening
To counteract the use of VPNs and proxies by sanctioned actors, it’s crucial for compliance programs to enhance their IP and location screening processes.
Traditional geographic-based controls must be supplemented with advanced tools capable of detecting anomalous IP addresses and suspicious login patterns. Implementing geolocation verification techniques and monitoring for IP address changes that suggest VPN or proxy usage can help identify and mitigate risks associated with location obfuscation.
However, enabling controls using IP intelligence is only half the battle. How institutions choose to operationalize these controls will require additional strategic decisions. Institutions should clearly outline in their policies and procedures how these controls will be implemented, monitored, and what scenarios will trigger specific actions with customers and/or regulators.
Compliance insight: Leverage advanced IP analytics
Sanctioned actors often exhibit specific behavioral patterns when using VPNs and proxies to evade detection.
By leveraging advanced behavioral analytics, compliance teams can identify irregularities in transaction and customer behaviors that may indicate the use of location-obfuscation tactics. For example, monitoring for transactions conducted from multiple IP addresses within short time frames or from locations known for high VPN usage can provide critical insights into potential evasion attempts.
{{premium-content_chapter-divider}}
<span class="premium-content_chapter">PART FOUR</span>
What’s next?
Future-proofing your sanctions program with blockchain intelligence
In recent years, the global sanctions landscape has evolved rapidly. To avoid being caught unprepared, crypto businesses must establish robust frameworks to quickly expand their sanctions coverage and manage exposure. Proliferation financing has also become increasingly important for policymakers worldwide, necessitating a tailored yet complementary approach to any sanctions program for crypto asset businesses.
For crypto businesses, an effective sanctions program should:
- Get the fundamentals right: Start with a trusted data and screening provider, ensuring their solution is properly integrated into your systems. Regularly determine and review your sanctions exposure and seek advice if you’re not confident in your findings.
- Expand awareness and capabilities: Enhance sanctions evasion awareness with a proactive vendor that has dedicated expertise in the field. Continuously evaluate how you can improve your program, learn from designations and enforcement actions, and refine your rules based on known risks.
- Future-proof your program: Conduct "what if" exercises, educate your board on the latest enforcement actions, stay updated on evolving evasion trends, and invest in the latest technology to identify evasion.
By following these steps, crypto businesses can better navigate the complexities of sanctions compliance and remain prepared for potential challenges.
To learn more about how TRM can seamlessly plug into your sanctions program, click here.
{{premium-content_chapter-divider}}
Frequently asked questions (FAQs)
1. What are some of the most common sanctions evasion techniques using crypto?
Common techniques include changing wallet addresses, rebranding entities, using evasive transaction patterns, leveraging third-party facilitators, and obscuring geographic location.
2. How do sanctioned actors use new crypto wallet addresses to avoid detection?
Sanctioned entities rapidly create new, unlisted addresses to move funds and avoid static screening lists. These addresses are often discarded after limited use.
3. Can sanctioned entities evade detection by changing their names?
Yes. Some actors rebrand without changing ownership or infrastructure. TRM identified this tactic in the Netex24 case, where the entity rebranded as SafelyChange after being sanctioned.
4. What are cross-chain swaps and how are they used in sanctions evasion?
Cross-chain swaps allow illicit actors to move funds across blockchains to obscure transaction trails. These patterns often involve mixers, smart contracts, and automated tools.
5. How are VPNs and proxies used to bypass crypto sanctions controls?
VPNs and proxies mask users’ IP addresses, making it appear as though transactions originate from jurisdictions outside of sanctioned regions.
6. What compliance measures help detect evasive crypto transactions?
Effective programs include frequent screening, behavioral analytics, historical lookbacks, IP screening, and vendor tools that expand attribution beyond listed addresses.
7. What is indirect sanctions exposure in crypto, and why does it matter?
Indirect exposure refers to funds passing through multiple wallets before reaching your platform. Compliance teams must evaluate how many “hops” trigger a reporting obligation.
{{premium-content_chapter-divider}}
About TRM Labs
TRM Labs provides blockchain intelligence solutions to help public agencies, financial institutions, and cryptocurrency businesses prevent, detect, and investigate crypto-related fraud and financial crime. To learn more, visit www.trmlabs.com.








.svg)

.png)