Elevating Ongoing AML Supervision
How to leverage blockchain intelligence in processing VASP reporting and alerts

Key takeaways
- Blockchain intelligence empowers regulators to assess VASP risk in real time, validate reporting accuracy, and take action on both routine and event-driven alerts.
- TRM’s tools like TRM Know-Your-Entity, TRM Forensics, and TRM Real-Time Supervision enable supervisors to monitor high-risk activity, trace fund flows, and identify compliance gaps across the VASP lifecycle.
- Supervisors can cross-verify AML alerts, SAR/STR reports, and digital asset address disclosures to pressure test a VASP’s controls and uncover unreported risk exposure.
- Scenarios like sanctions evasion, parasite exchanges, or liquidity runs can be investigated by analyzing wallet architecture, transaction volumes, and customer movement across platforms.
- Event-driven inquiries — like leaks or law enforcement tips — can be matched with on-chain data to detect illicit finance patterns and strengthen jurisdiction-wide AML/CTF enforcement.
{{premium-content_chapter-divider}}
Introduction
Interpreting transaction data and financial crime monitoring alerts from virtual asset service providers (VASPs) is a key element of ongoing, risk-based supervision. Whether for routine reporting or in response to an event-driven risk, supervisory bodies need to be able to interrogate what is reported, its accuracy, and the steps taken to limit any risks identified. Blockchain intelligence tools are essential in these tasks.
In this guide, we’ll outline key considerations for using blockchain intelligence in analyzing routine reporting. We’ll also cover how you can use blockchain intelligence in various event-driven scenarios—when, as a supervisor, you might need to request more information from a VASP—and explore what can be learned in the process.
The basics: Using blockchain intelligence across the entire regulatory lifecycle
Blockchain intelligence combines raw blockchain transaction data with real-world threat intelligence to identify links between entities and indicators of illicit activity. Armed with these insights, regulators can gain a more comprehensive view of a VASP’s risk exposure and make data-driven decisions throughout the supervisory lifecycle, pictured below.

{{elevating-ongoing-aml-supervision-call-out-1}}
TRM offers a suite of tools for regulators who need to perform ongoing supervision. Throughout this guide, we’ll refer to the following tools (which can be found in your TRM interface if you’re a TRM customer):
- Know-Your-Entity: Assess the holistic risk of VASPs and other crypto businesses
- Transaction Monitoring: Automate risk-based monitoring of virtual asset transactions
- Forensics: Leverage transactional data and threat intelligence to understand the flow of funds of an entity or wallet
Even if you’re not currently a TRM user, this guide is an invaluable source for regulators looking to learn best practices for supervision. Let’s dig in.
{{premium-content_chapter-divider}}
Part 1: Reviewing VASP reporting
Authorized or fully licensed VASPs may need to periodically report information to their regulator. Depending on the risk of the entity in question, the frequency and detail of these reports may differ. But they are likely to include some of the following points:
- Documentation review: An up-to-date anti-money laundering (AML) risk assessment and documentation on any changes to the VASP’s controls framework.
- Digital asset address information: An up-to-date list of all virtual asset addresses controlled by the VASP
- Alert sample: A subset of the VASP’s AML alerts from a prescribed time period; Financial Intelligence Unit (FIU) supervisors will also have access to Suspicious Activity Reports / Suspicious Transaction Reports (SARs/STRs)
Below are three examples of information different supervisors currently request from the VASPs they supervise or guidance on record keeping by VASPs.*
UAE - VARA
Virtual Assets Regulatory Authority (VARA) requests reports from their VASPs on a monthly, quarterly, and yearly basis.
Requested information includes:
- Balance sheet and all off-balance sheet items
- Addresses of virtual asset wallets
- A full list of entities within their group and any related virtual asset transactions
- Risk exposure report prepared by the board
UK - JMLSG
The UK’s Joint Money Laundering Steering Group publishes guidance for VASPs, which includes guidance on record keeping.
The guidance on record keeping includes:
- The public keys (or equivalent identifiers) of relevant parties
- The addresses or accounts involved (or equivalent identifiers)
- The nature (e.g. deposit, transfer, exchange) and date of transactions
- The amounts transferred
Singapore MAS
Licensed digital payment token service providers (DPTSPs) are required to submit regular returns on:
- DPTs bought, sold, and exchanged with their platform, as well as with other regulated and unregulated VASPs, and unhosted wallets
- Number of customer accounts maintained, and information on account balances and transactions
- Top five DPTs transacted and held
- DPTs in both direct and indirect transactions with high-risk jurisdictions, and wallet addresses associated with anonymity-enhancing technologies
- High-risk customers’ (e.g. politically exposed persons) accounts and transactions
* Note: This information is accurate as of March 2024
Of course, jurisdictions will vary in the exact information they require entities to report. But they can all use blockchain intelligence to corroborate information provided by a VASP, or otherwise identify additional illicit activity a VASP may be exposed to.
Let’s look at the types of information you might expect to receive from a VASP, how to interpret it, and how to test and validate it with blockchain intelligence.
Reviewing documents: AML/CFT risk assessment
Most jurisdictions require VASPs to submit their Anti-Money Laundering and Combating the Financing of Terrorism (AML/CFT) risk assessment on a periodic basis, whenever new products and services are launched, or when significant changes at an entity occur.
VASP risk exposure is dynamic—so supervisors need to use blockchain intelligence tools to ensure that a VASP is correctly monitoring their exposure to risk and recording it accurately in their risk assessment. With a platform like TRM, supervisors can assess the on-chain exposure of a VASP’s transactions to different risk categories and take action where appropriate.
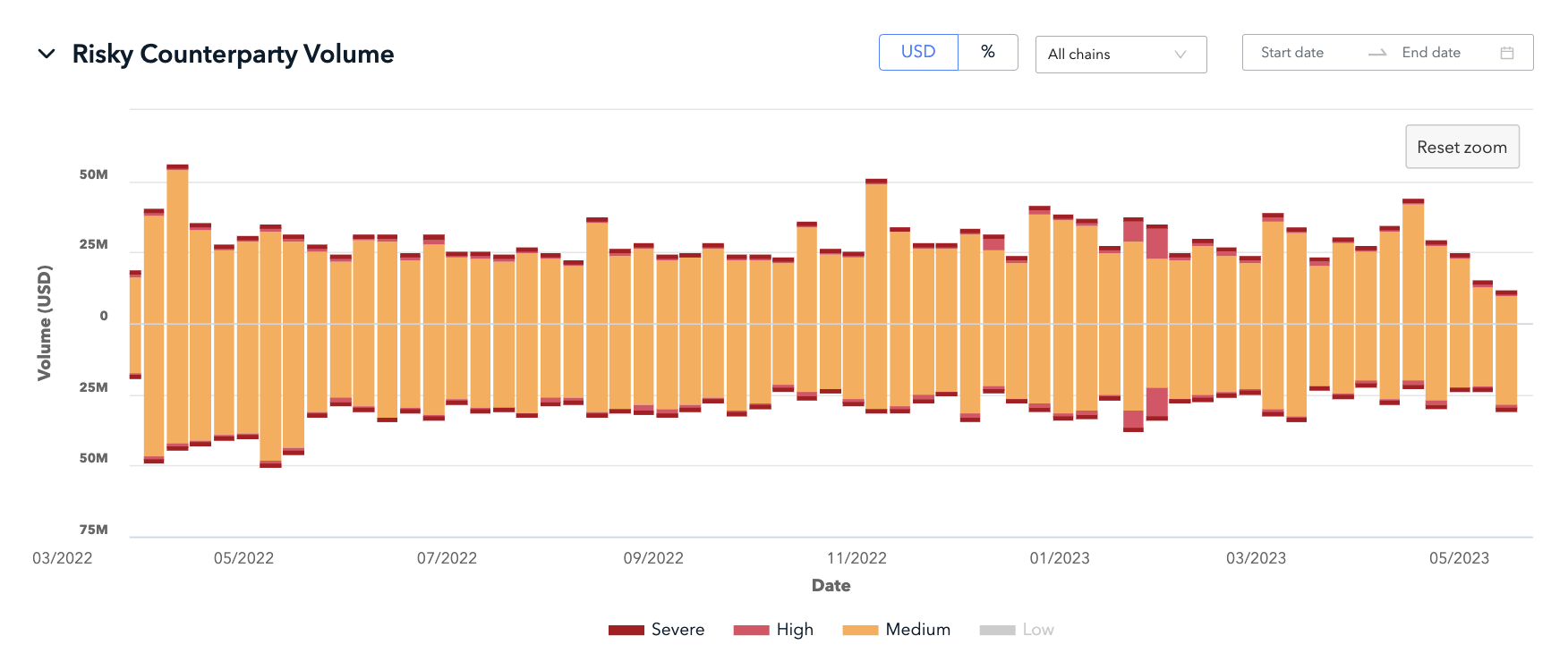
Case study: Evaluating a VASP’s risk exposure
In the image , we see the total risky counterparty volume of a VASP over approximately a one-year period. During this time, the VASP’s overall medium, high, and severe risk exposure has reduced slightly. While overall risk has reduced, a supervisor may still be concerned with high and severe risk activities, and will want to understand whether they’ve been flagged by the VASP in their risk assessment.
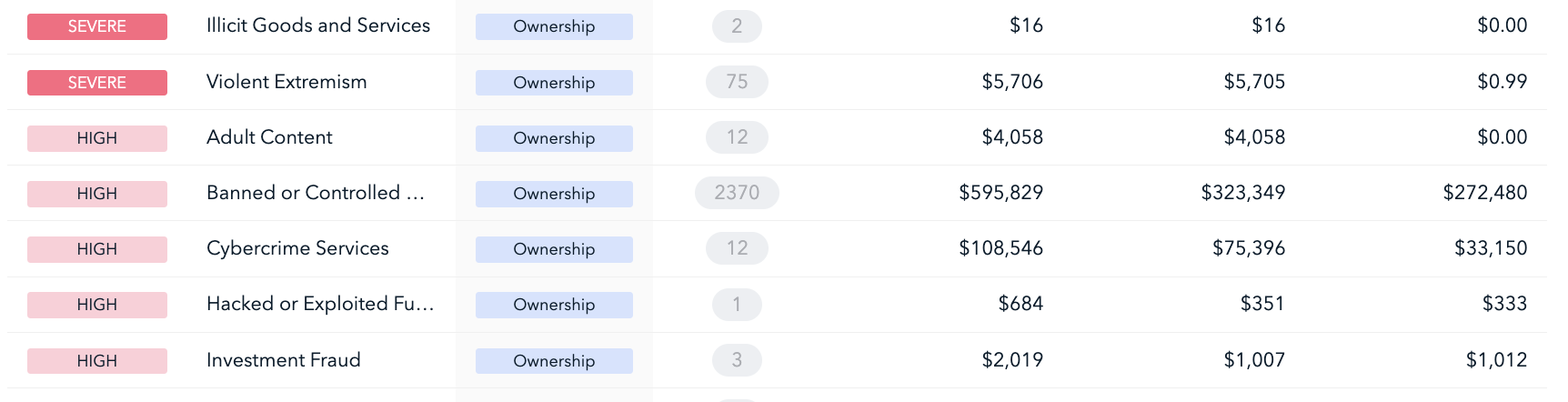
Using TRM, supervisors can analyze a VASP’s direct exposure to different risks. For example, in the screenshot, we see a severe ownership risk warning for “Violent Extremism” associated with transactions of nearly $6,000. The supervisor can review the Terrorist Financing section in the VASP’s risk assessment to see whether it also considers risks from “Violent Extremism.” In this example, let’s say it does not. Using this information — and additional context that the VASP borders an unstable nation-state — the supervisor will need to ask the VASP what this exposure to violent extremism could mean for their broader exposure to terrorist financing risk.
{{elevating-ongoing-aml-supervision-call-out-4}}
Reviewing digital asset addresses
Understanding the ecosystem of significant addresses associated with an entity is also an important data point for supervisors.
At the point of licensing, most jurisdictions will require VASPs to disclose all of the addresses they own. This is important for establishing how a VASP manages its accounts and the custody of its customers’ assets—as well as how it aligns with the International Organization of Securities Commissions’ (IOSCO’s) standards for centralized services.
Like many things in the world of virtual assets, the wallet infrastructure of a VASP is likely to change over time. Supervisors may request, on an ongoing basis, the most up-to-date list of addresses controlled and used by the entity. Using a blockchain intelligence tool, supervisors can review the addresses listed by an entity and investigate whether there are any undeclared addresses that could be associated with it.
For example, a supervisor may identify a counterparty address that is receiving considerable volume from a disclosed VASP address with few ongoing transactions. One feasible explanation for this could be that the VASP is using the address for storage. If the address is not reported as owned by the VASP, the regulator will want to know why, and question the VASP further on what the function of the address is and whether its use is in line with regulatory requirements.
Verifying alert samples
Another important step in ongoing supervision is pressure testing whether a VASP’s anti-financial crime control framework works in practice.
Many supervisors require their VASPs to report a subset of the alerts they generate in response to illicit finance, and compare these with what the supervisor can see on-chain using their own blockchain intelligence tool.

A supervisor will use reported alerts in various ways to better understand the effectiveness of the anti-financial crime team at an entity. For example, they might:
- Request access to the status of the alerts. Supervisors will want to know what next steps the entity’s compliance team took once the alert was generated. This helps the regulator assess how the compliance team is operating (e.g. whether they’re on top of their alerts, or whether they have significant backlogs).
- Use blockchain intelligence to correlate the alerts with the SARs/STRs reported by the entity (e.g. whether there were alerts that should have triggered the submission of a report, but did not)—particularly if the supervisor is a FIU.
- Review the activity against whatever caused them to request alerts in the first place, such as looking for the entity’s sanctions exposure.
- Review alerts for the collection of their own intelligence to understand whether the entities “see” the same financial crime risk as the supervisor, and more broadly to improve the holistic virtual asset risks and threats impacting their jurisdiction. This may be particularly useful if the supervisor is not a FIU.
These points can also be used to inform regulatory strategy, or factor into the national AML/CTF risk assessment picture.
If a regulator’s blockchain intelligence tool flags a high-risk transaction—as in the previous example we explored involving violent extremism—they can check the alerts provided within regulatory returns to validate whether an alert was generated in this instance. The supervisor may also wish to check what affirmative action occurred on receipt of the alert (e.g. on-chain investigation, off-boarding, or reporting of a SAR). If an alert was not generated, the answer might not be as simple as ineffective controls.
{{elevating-ongoing-aml-supervision-call-out-5}}
{{premium-content_chapter-divider}}
Part 2: Event-driven reporting
On any given day, new headlines might break, whistleblowers might submit leads, or suspicions about a particular token or platform could arise—all leading to supervisors needing to request ad hoc data from a VASP.
Let’s take a look at five such possible scenarios, and how blockchain intelligence can be used to help supervisors understand relevant risks based on these events.
Scenario 1: Comparing local vs. group activity
A global VASP identifies a substantial shortfall in customer deposits against available assets, bringing its future into question. This VASP has a subsidiary in your jurisdiction, and you want to find out if trouble at the group level is likely to impact your entity and the consumers they serve.
In this scenario, a supervisor will want to understand the wallet architecture of the local supervised entity and uncover whether there have been significant transfers to the group level that might make the local entity illiquid.
If there is a “run” on the entity, the supervisor will want to know if it has sufficient funds in its digital asset addresses to cover withdrawals. And more broadly, a supervisor will want to assess the contagion risk of the entity collapsing. If customers do leave the VASP, which other services are they likely to use? And will they have sufficient controls in place to safely absorb those customers?
{{elevating-ongoing-aml-supervision-call-out-6}}
Scenario 2: Sanctions
A conflict has been ongoing for one year, in which sanctions have been put in place to try and change the aggressor’s behavior. Your jurisdiction is near, with a vibrant manufacturing and tech sector that has been exploited for circumvention. To combat the use of virtual assets in this circumvention, your jurisdiction issues new guidance on the implementation of the related sanctions regime by VASPs.
As a supervisor, you want to ensure that the controls of the VASPs you supervise are having their desired effect. Three months after the guidance is published, you request a sample of sanctions alerts from the VASPs you supervise.
Once a supervisor has requested reports from the entities they oversee, they can use blockchain intelligence to analyze them. With TRM, supervisors can:
- Investigate alerted transactions and identify sanctioned flows between different entities using TRM Forensics
- Within Forensics, unplotted flows identify where there might be unknown connections between wallets
- TRM’s unique heuristics also identify behavioral patterns—known as SignaturesTM—within alerted transactions, which could surface additional suspicious activity
- Review sanctions exposures across entities using TRM’s Real-Time Supervision. This helps supervisors understand what “normal” exposure looks like in their jurisdictions so they can compare this against the reported period.

- Ensure sanctioned currencies are no longer supported by VASPs. Regulators can review (and request a refresh) of the currency support of any entities they supervise to ensure they don’t support payments in a currency linked to a high-risk or sanctioned jurisdiction.
With all of this information in hand, a supervisor can share feedback with the relevant authority on whether further guidance is needed to support the sector.
Scenario 3: Law enforcement reports
A regulator receives a report from law enforcement that a VASP might unwittingly be supporting a parasite exchange utilized by a darknet marketplace (DNM). The regulator must examine if this is the case.
“Parasite exchanges” make use of the architecture of a larger exchange to provide digital assets trading services to users—usually without the knowledge or consent of the host exchange. Because they often have connections to high-risk jurisdictions like Russia or Iran, it is vital that regulators investigate these exchanges as soon as they become aware of them.
First, the regulator will analyze the on-chain volume flowing into the VASP to determine whether there are any significant counterparties that can’t logically be explained. They should then use a tool like TRM Forensics to look at the beneficiaries of that significant counterparty.
{{elevating-ongoing-aml-supervision-call-out-7}}

Using this analysis, supervisors can then ask their supervised entity a range of questions to improve their understanding of the parasite entity. They should do this with a view towards testing the entity’s controls, whilst potentially indirectly disrupting the darknet marketplace activity.
Here are some of the questions supervisors should ask:
- Were any alerts generated for the relevant addresses or a specific transaction?
- If these alerts were adverse, what steps have you taken to limit your risk?
- Who is this customer?
- Where are they based?
- How does this customer fit within your risk parameters?
- Please provide KYC documentation for this customer.
Scenario 4: Unknown unknowns
A data leak is published across the major newspapers in your jurisdiction. A whistleblower has leaked the details of clients of a high profile law firm, implying their involvement in a massive corruption and tax evasion scheme.
As a regulator, you may need to understand if any of the individuals named in the scandal have links to your jurisdiction’s domestic crypto asset market, and whether crypto assets were used as part of the scheme.
Beginning with a request to supervised VASPs, the regulator will ask its entities if anyone named in the leak has wallets with their service. If so, these wallets can be bulk uploaded into TRM Forensics. Once the wallets have been loaded into a graph, the regulator can then analyze any connections between them, and determine whether any transfers could be indicative of tax evasion or corrupt payments.
Any VASPs identified with significant exposure may have been targeted by the clients for an unknown reason. This information can improve your understanding of illicit actor preferences, which can be useful for further analysis. In addition, supervisors may wish to explore why this is the case with the supervised entity.
Scenario 5: Unregistered VASPs
Media, law enforcement, or other sources might also make regulators aware of unlicensed entities operating in their jurisdiction that may warrant inspection—or even being shut down—if they are negatively impacting consumers.
TRM can help proactively identify or investigate unregistered VASPs when they come to the attention of regulators. To find out how, check out this guide:
{{elevating-ongoing-aml-supervision-guide-call-out}}
{{premium-content_chapter-divider}}
Conclusion
When taking a risk-based approach to supervising VASPs, it’s crucial that any insights gained during ongoing supervision are reliable—helping supervisors gain confidence that their regulatory resources are being deployed appropriately. Both regular reporting and ad hoc, event-driven reporting offer opportunities to leverage blockchain intelligence and really put a firm’s data collection and anti-financial crime controls to the test.
{{premium-content_chapter-divider}}
Frequently asked questions (FAQs)
1. What is the purpose of ongoing AML supervision for VASPs?
Ongoing AML supervision ensures virtual asset service providers (VASPs) operate with appropriate controls. It allows regulators to detect risks in near real time and confirm that VASPs are adhering to AML/CFT requirements.
2. How can blockchain intelligence support AML supervision?
Blockchain intelligence enables supervisors to verify reported data, trace on-chain transactions, identify illicit exposures, and monitor risk categories across VASP operations.
3. What tools does TRM offer to assist regulators?
TRM provides Know-Your-Entity for entity-level risk assessments, Forensics for transaction tracing, and Real-Time Supervision for jurisdiction-wide risk exposure monitoring.
4. What is ownership vs. counterparty risk in blockchain supervision?
Ownership risk involves VASP-controlled wallets with direct exposure to threats. Counterparty risk relates to transactions with risky third-party addresses. Both are critical for evaluating AML risk.
5. Why do regulators review VASP wallet addresses?
Reviewing wallet addresses helps regulators verify ownership claims, detect undeclared addresses, and assess if the infrastructure aligns with custody and licensing expectations.
6. What’s the role of alert sample reviews in AML supervision?
Alert samples help assess the effectiveness of a VASP’s compliance program — verifying if alerts match risk levels, led to proper action, or triggered SAR/STR filings.
7. How can blockchain data validate sanctions compliance?
Supervisors can use blockchain intelligence to trace sanctioned flows, review alerts, and assess if VASPs have ceased support for restricted jurisdictions or currencies.
8. What are parasite exchanges, and how are they detected?
Parasite exchanges exploit a host exchange’s infrastructure without consent. TRM tools can detect repeated deposit/withdrawal patterns and address reuse indicative of these entities.
{{premium-content_chapter-divider}}
About TRM Labs
TRM Labs provides blockchain analytics solutions to help law enforcement and national security agencies, financial institutions, and cryptocurrency businesses detect, investigate, and disrupt crypto-related fraud and financial crime. TRM’s blockchain intelligence platform includes solutions to trace the source and destination of funds, identify illicit activity, build cases, and construct an operating picture of threats. TRM is trusted by leading agencies and businesses worldwide who rely on TRM to enable a safer, more secure crypto ecosystem.
TRM is based in San Francisco, CA, and is hiring across engineering, product, sales, and data science. To learn more, visit www.trmlabs.com.








.svg)

.png)



