Inside the Nobitex Hack: How the Iran-Israel Conflict Exposed Tehran's Grip on Its Crypto Services

This week, Iran confirmed that President Masoud Pezeshkian sustained minor injuries during last month’s 12-day conflict with Israel, shedding light on the ongoing, far-reaching impacts of the war, including on the crypto ecosystem. TRM Labs’ analysis reveals that the escalation in hostilities triggered a significant spike in capital flight from Iranian crypto exchanges, with outflows from Nobitex, the country’s largest platform, increasing by more than 150% compared to the previous week.
Amid the conflict, on June 18, 2025, Nobitex was targeted in a USD 90 million hack by Israel-linked group Predatory Sparrow, which exposed the infrastructure underpinning Iran’s crypto economy.
Together, these incidents offer a rare window into Iran’s crypto economy — revealing how geopolitical shocks, economic constraints, and regime control intersect in shaping digital asset activity.
Key takeaways
- Nobitex users moved funds out of the exchange ahead of Israel’s missile strikes, likely anticipating the conflict. The rise of over 150% in outflows suggests users were seeking to reduce exposure to domestic platforms amid rising geopolitical risk. Furthermore, following the hack, incoming transaction volumes to Nobitex dropped by 70% year-over-year, which coincided with users expressing distrust in the platform and Iranian exchanges more broadly.
- Leaked source code from the breach revealed the regime’s dual priorities, with Nobitex enabling warrantless state surveillance while protecting the privacy of VIP users. The hack also saw Iran impose overnight trading restrictions, likely aiming to tighten control over crypto flows. This change disrupted markets and contributed to price swings in USDT.
- Post-hack, dormant bitcoin mining-linked wallets began moving funds, ultimately consolidating into Nobitex’s new hot wallet. Bitcoin mining remains a key tool for Iran to generate revenue and evade sanctions.
- We assess that politically motivated cyberattacks on crypto exchanges will likely continue, particularly during periods of heightened geopolitical tensions. Unlike financially driven campaigns such as those by North Korea’s Lazarus Group, these operations will likely focus on disrupting infrastructure, collecting intelligence, or exposing adversaries’ activities.
How the Iran-Israel conflict triggered capital flight from crypto exchanges
Due to sanctions, economic volatility, and deep mistrust in traditional financial institutions, Iranians have increasingly turned to cryptocurrency to preserve value, access global financial infrastructure, and move assets beyond the reach of state-controlled channels.
Highlighting how geopolitical instability and the threat of kinetic warfare can drive on-chain movement, TRM identified an uptick in outbound activity from Iranian cryptocurrency services in the days preceding Israel’s missile strikes on June 13, 2025. This pre-conflict movement reflects that Iranians were likely anticipating a direct attack, in light of intensifying rhetoric between Iran and Israel, elevated regional tensions, and a broader sense of uncertainty around cross-border escalation. As such, they likely sought to move capital out of Iranian cryptocurrency services to mitigate custodial risk, access liquidity outside of Iran, or preserve asset mobility.
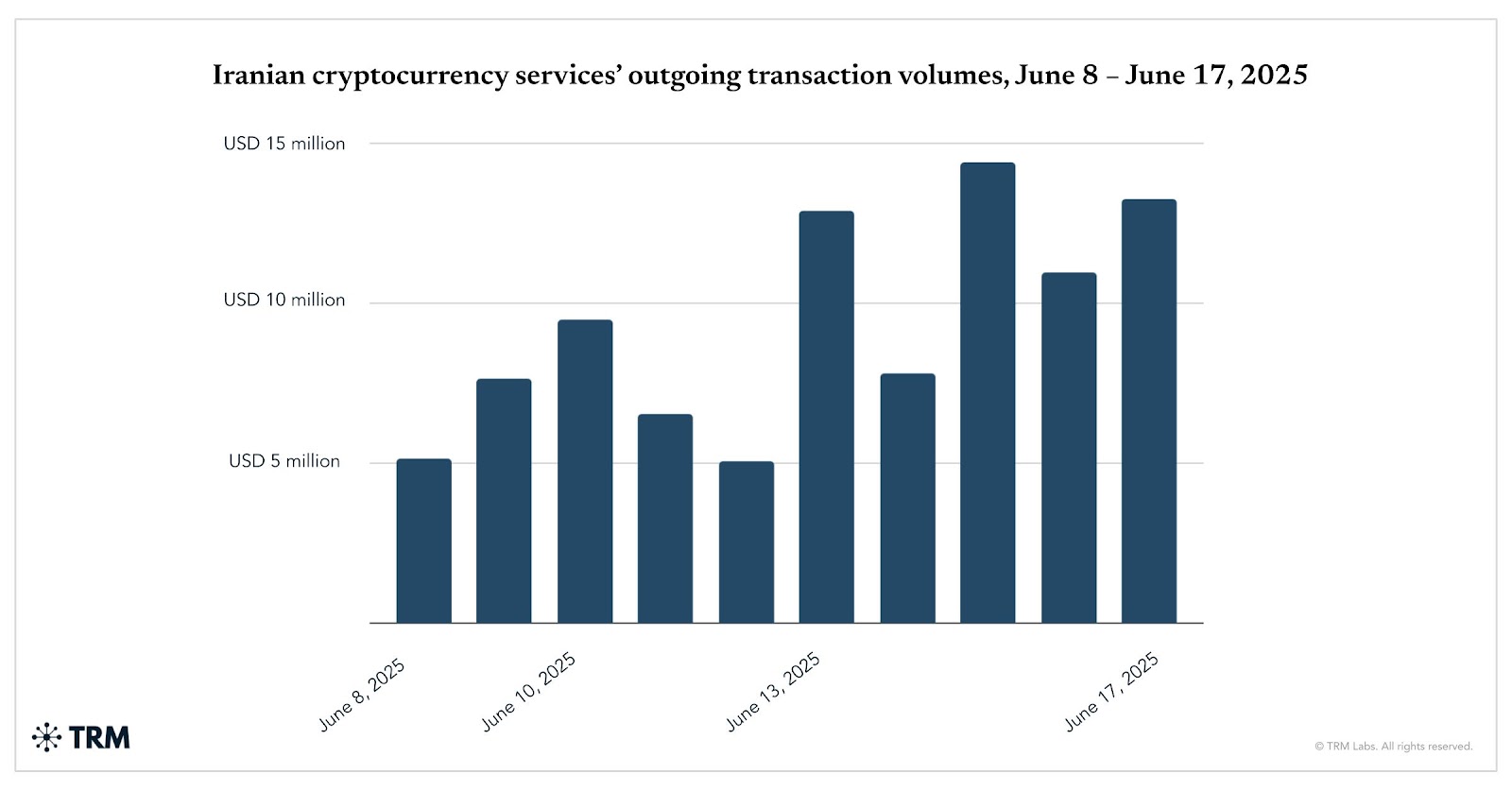
Following the June 13 missile strikes, Nobitex users sent funds either directly or through intermediary wallets to a variety of global services as seen below.

Nobitex’s role in sanctions evasion and illicit activity
Nobitex is a critical piece of Iran’s crypto infrastructure — used by both ordinary citizens navigating inflation and economic isolation, and illicit actors circumventing the traditional financial system in order to evade sanctions. While the platform facilitates billions in crypto transactions, including those routed through services with lax Know Your Customer (KYC) controls, it has also employed techniques to reduce operational costs and obscure fund flows.
Highlighting Nobitex’s role in facilitating regime-aligned operations, TRM identified on-chain activity involving Islamic Revolutionary Guard Corps (IRGC)-linked actor Amir Hossein Nikaeen Ravari and Gaza Now, a pro-Hamas media outlet sanctioned after the October 7, 2023 attack on Israel.
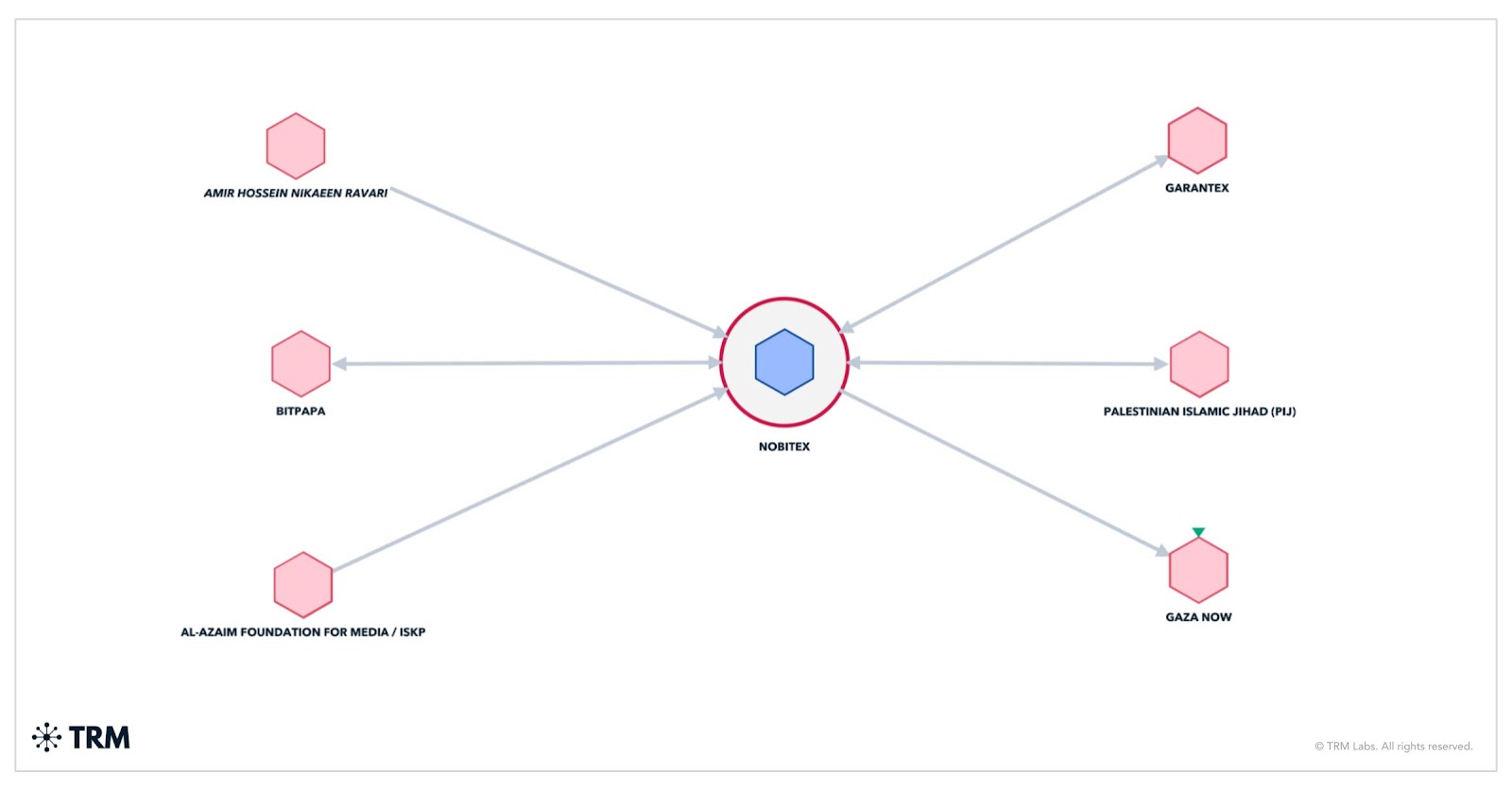
How Nobitex enables state surveillance while protecting VIPs
As documented in our blog post Inside the Nobitex Breach: What the Leaked Source Code Reveals About Iran’s Crypto Infrastructure, leaked source code from the Nobitex breach showed that the exchange’s internal infrastructure was designed to evade detection by the US Department of the Treasury’s Financial Crimes Enforcement Unit (FinCEN) and US-based blockchain intelligence firms. This included modules for generating stealth addresses, obfuscating transactions, and evading surveillance.
The code provides a rare look into how Iran’s largest exchange balances state oversight and discretion. It includes hardcoded permissions and application programming interfaces (APIs) that grant unrestricted access to state-aligned entities, effectively enabling warrantless monitoring. It also features a parallel infrastructure for high-value, politically exposed users — routed through separate logic to bypass fraud checks and reporting requirements.
This infrastructure, combined with obfuscation features like stealth addresses, transaction batching, delayed mixers, and dynamic endpoint switching, reflects a deliberate strategy to shield regime-linked and sanctioned actors while satisfying domestic monitoring demands.
Nobitex breach primarily politically motivated
We continue to assess that the Nobitex breach was primarily politically motivated, targeting a critical node in Iran’s sanctioned financial infrastructure while also offering opportunities for intelligence collection.
Predatory Sparrow moving the stolen funds to vanity addresses explicitly referencing the IRGC underscores the political nature of the cyberattack. Doing so also ensured the stolen funds would likely remain unmoved and unusable. This is because the TRON addresses were generated by brute-forcing random private keys until the desired slogans appeared — not by deriving them from known keys. Without a valid private key, no one can authorize outgoing transactions, effectively locking the funds in a wallet that’s visible to everyone but accessible to nobody.
This campaign also likely had a disruptive objective, limiting access to digital financial services for millions of ordinary Iranians who rely on Nobitex and affiliated banking rails. We assess that future disruptive activity from state-linked or state-aligned groups targeting adversaries’ infrastructure is likely.
Nobitex responds to the hack with phased recovery
In early July, Nobitex announced that all core functions, including trading on all supported cryptocurrencies, rial (IRR) deposits and withdrawals, and most crypto deposit/withdrawal services, were active again on both its web and Android platforms. Nobitex is reportedly gradually reconciling users’ credit and loan information. Furthermore, the exchange said it would waive penalties on unpaid loan installments given the “special circumstances.”
The exchange was likely able to recover relatively quickly due to its practice of converting commission fees into bitcoin and holding reserves. These BTC-denominated funds enabled the exchange to refund customers and resume operations faster than expected.
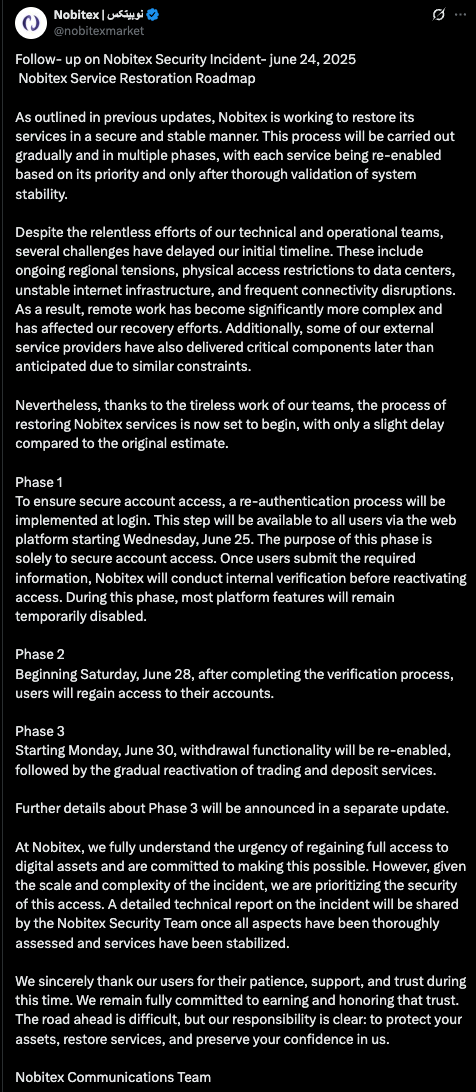
Following initial containment, Nobitex completely overhauled its infrastructure. The exchange repeatedly warned users that legacy deposit addresses were no longer valid and that funds sent to them would be lost, underscoring the severity of the breach and that the compromised system was almost certainly irreparable. TRM’s on-chain and off-chain analysis indicates that services resumed in stages beginning June 25, 2025, with full trading functionality restored by July 9 — a timeline consistent with Nobitex’s public statements.
Dormant bitcoin mining wallets moving funds post-hack
TRM's analysis also found that Nobitex-attributed wallets, which had received rewards from two crypto mining pools since at least 2021, started moving funds for the first time following the Nobitex hack. These funds were ultimately consolidated into one of Nobitex’s newly created hot wallets. Alongside other inflows, these assets were critical in helping the exchange resume operations. We continue to assess that Iran uses bitcoin mining as a key tactic to generate revenue and evade Western sanctions.

Significant decline in Nobitex’s incoming volumes reflects customers’ shaken trust
According to TRM's on-chain analysis, incoming transaction volumes to Nobitex in early July, 2025 — following the hack — dropped by more than 70% compared to the same period in 2024, while outgoing volumes increased by 31%. Although this difference is at least partially due to the exchange restarting user services, a decrease in user confidence may also be a factor.
Declining user confidence in Nobitex, and Iranian crypto services more broadly, has become increasingly apparent in the wake of the breach. The breach exposed Nobitex’s insufficient user safeguards and weak cybersecurity practices, and highlighted the regime’s influence on virtual asset service providers (VASPs). These factors may contribute to a sustained decrease in trading activity on Nobitex.
Users who lost assets or remain unable to access their accounts have been particularly vocal. Some report being locked out of their accounts entirely, while others have expressed frustration over delays in the platform restoring services.
Tehran tightens grip on crypto exchanges following the hack
The Nobitex hack triggered a regulatory clampdown from the Iranian state, with the Central Bank of Iran reportedly prohibiting domestic cryptocurrency exchanges from trading between 8:00pm and 10:00am local time. Though framed as a security measure, this move was almost certainly the regime’s attempt to tighten control over a sector it views as a threat to its authority, even as it relies on crypto to evade sanctions and access global liquidity.
This intervention significantly disrupted markets, leading to significant price swings for Tether (USDT), a key stablecoin in Iran. Although prices are hard to verify in state-controlled markets, sources suggest USDT surged to over 12,000 Toman as users reacted to the hack and subsequent restrictions.
Conclusion
Cryptocurrency remains both a financial outlet and a strategic liability for the Iranian regime. Capital flight from exchanges like Nobitex surged during the recent conflict with Israel, as Iranian citizens sought to move assets beyond the reach of state control. Meanwhile, Iran’s conflicting relationship with crypto reveals a regime wrestling between control and connectivity — a tension playing out beyond its borders.
The Nobitex breach exposed the depth of state control over domestic virtual asset platforms. The Central Bank’s trading curfew and Nobitex giving warrantless access to law enforcement underscore how tightly regulated the sector is in Iran. The hack has also fundamentally shaken Iranians’ confidence in Nobitex’s ability to safeguard user data and assets, and the incident may drive Iranians to offshore platforms or peer-to-peer alternatives. Furthermore, the dormant mining wallets moving funds following the hack reflect Iran's continued use of bitcoin mining to generate income and bypass international sanctions.
As the volatile threat landscape in the Middle East shows no signs of abating, we assess that politically motivated cyberattacks on crypto exchanges will likely continue. Blockchain intelligence tools, such as those offered by TRM, remain essential to uncovering illicit financial activity — including sanctions evasion — and identifying behavioral patterns that persist even after systems are rebuilt.
{{horizontal-line}}
FAQs
What happened during the Nobitex hack and who was behind it?
On June 18, 2025, Nobitex — the largest cryptocurrency exchange in Iran — was targeted in a politically motivated cyberattack attributed to Israel-linked group Predatory Sparrow. The attackers moved USD 90 million in crypto to vanity addresses with IRGC slogans, ensuring the funds were unmoveable. TRM assesses the hack was designed to disrupt Iran’s crypto infrastructure, expose regime-linked surveillance practices, and limit financial services for ordinary users.
Why did users withdraw funds from Iranian crypto exchanges in the lead up to and during the recent Iran-Israel conflict?
Ahead of Israel’s missile strikes on June 13, 2025, users of Iranian exchanges — particularly Nobitex — rapidly moved capital abroad, anticipating increased geopolitical risk. TRM identified a more than 150% spike in outflows from Nobitex during this period, suggesting users were attempting to reduce custodial risk, preserve asset mobility, and maintain access to global markets amid rising uncertainty.
How did the Nobitex hack impact trust in Iranian crypto platforms?
The breach had a significant impact on user sentiment. Incoming transaction volume to Nobitex dropped over 70% year-over-year in early July 2025, with many users expressing concerns over inadequate safeguards and state surveillance. Some users were locked out of their accounts entirely, while others sought offshore exchanges or privacy-preserving tools to avoid future risk.
What role does Nobitex play in Iran’s crypto ecosystem and sanctions evasion?
Nobitex is central to Iran’s domestic crypto economy and is used by both everyday citizens and state-linked actors. The exchange facilitates large transaction volumes and has reportedly implemented obfuscation tools to enable surveillance while protecting VIP users. TRM analysis revealed that entities linked to the IRGC and sanctioned pro-Hamas media outlets have transacted through Nobitex, underscoring its dual-use role in financial repression and sanctions evasion.
Is Iran still using crypto, like bitcoin, to evade sanctions post-hack?
Yes, TRM’s analysis shows that Iran continues to use bitcoin mining as a revenue source and sanctions workaround. Following the Nobitex hack, dormant crypto mining wallets began moving assets, ultimately consolidating into Nobitex’s new hot wallet. These funds likely helped the platform resume operations and reflect Tehran’s ongoing strategy to generate income outside the traditional financial system.
Access our coverage of TRON, Solana and 23 other blockchains
Fill out the form to speak with our team about investigative professional services.






















