Understanding Address Poisoning on the TRON Blockchain

What is address poisoning?
Address poisoning — sometimes referred to as a “dusting attack” — has emerged as a persistent and increasingly sophisticated scam tactic. In these schemes, malicious actors send tiny amounts of cryptocurrency (e.g. TRX, often worth less than USD 0.01) to a large number of wallet addresses.
On the TRON blockchain, these micro-transactions are frequently labeled “TRX dust.” While seemingly innocuous, these transfers are often used to exploit TRON’s low-cost, high-throughput infrastructure — deceiving users into interacting with spoofed or malicious addresses that resemble their own.
Dusting attacks and how they differ from other scam tactics
Dusting attacks differ from other forms of unsolicited AirDrops in both intent and execution. These schemes typically involve:
- Address poisoning: Sending a dust transaction from an address that closely mimics a legitimate counterparty previously interacted with by the target
- Spam and transaction obfuscation: Flooding wallets with unsolicited tokens to clutter transaction histories — increasing the likelihood of user error or engagement with malicious contracts and phishing links
- De-anonymization attempts: Tracing how recipients move funds or interact with exchanges in an effort to cluster wallet ownership and reduce pseudonymity
While dusting occurs across multiple blockchains, TRON’s architecture — particularly its free bandwidth for basic TRX transfers — makes it especially susceptible to high-frequency dusting activity.
Common objectives of dusting attacks
Dusting attacks — particularly as part of address poisoning schemes — serve multiple purposes, most of which are malicious in nature. Common objectives include:
- Phishing and theft: Dusting is often used to execute address poisoning scams. By sending funds from a spoofed address that resembles a legitimate counterparty, scammers trick users into copying and pasting the wrong recipient — resulting in the inadvertent transfer of funds to a scam address.
- Behavioral analysis: Scammers may attempt to monitor how users manage or consolidate dust transactions. This behavior can offer insight into wallet ownership patterns or help identify addresses with higher balances — potentially exposing new attack surfaces.
- Scam promotion and lures: In some cases, dust is used to promote fraudulent schemes — such as AirDropping tokens embedded with phishing links in their token names or metadata, designed to entice users to engage with malicious contracts or websites.
While not all dust transactions are inherently malicious, TRM Labs recommends treating unsolicited micro deposits on TRON as suspicious by default — and avoiding any interaction with unknown tokens or addresses until their legitimacy can be verified.
Automation and scale
The sheer volume of TRX dust observed suggests coordinated and automated activity. Attackers likely:
- Run bots that monitor on-chain activity in real time to identify active wallets and opportunistically target them
- Use vanity address generation tools to create spoofed wallet addresses that visually resemble legitimate counterparties
- Deploy dust transactions immediately after user activity in an attempt to manipulate transaction histories and increase the likelihood of address poisoning
Target selection criteria
Target selection in TRX dusting campaigns is likely informed by several observable on-chain and behavioral indicators:
- Recent wallet activity: Attackers may prioritize wallets that have recently transacted, increasing the likelihood that users are engaged and susceptible to deception
- High-value balances: Wallets holding larger amounts — especially in USDT, a frequent target in phishing-related variants — may be viewed as more lucrative
- First-time counterparties: Initial transactions with unfamiliar addresses provide attackers a timely opportunity to introduce spoofed addresses that mimic legitimate senders
- Non-custodial wallets: Personal wallets are often more vulnerable to interaction-based exploits, whereas custodial platforms may filter out or suppress dust transactions entirely
What are the investigative signals of TRX dusting?
Despite its malicious use, TRX dusting can also generate investigative signals that support blockchain intelligence efforts:
- Infrastructure mapping: Tracing the origin and flow of dust transactions can help identify clusters of attacker-controlled addresses or wallets
- Victim identification: Analysts can detect users who engaged with spoofed addresses — often evidenced by outbound transfers to lookalike destinations following a dusting event
- Cross-campaign linkage: Overlapping indicators — such as reused infrastructure, behavioral patterns, or vanity address characteristics — can connect seemingly distinct phishing or scam operations
Using TRM’s blockchain analytics to trace TRX dusting on-chain
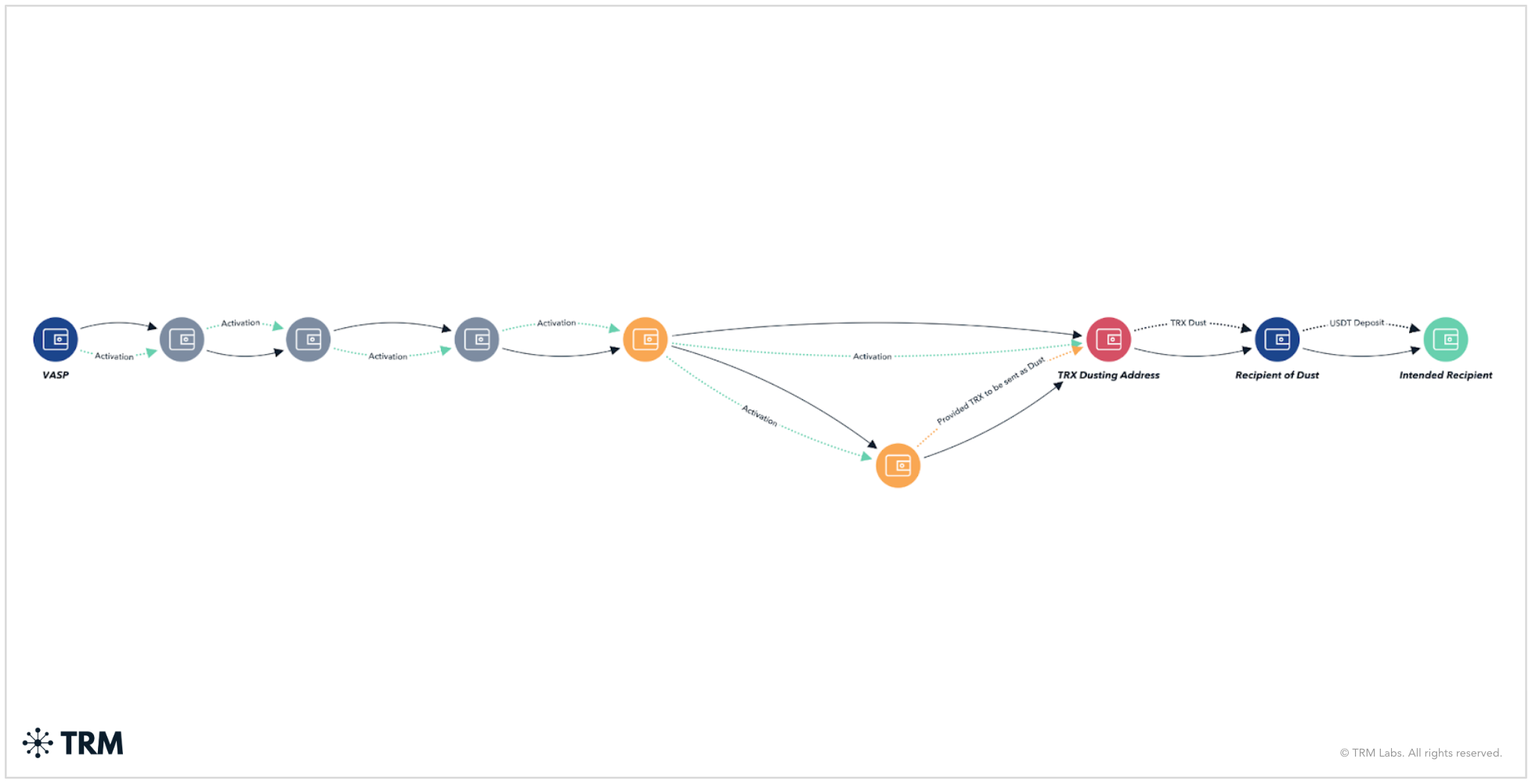
As shown in the image below, the address labeled “Recipient of Dust” deposited USDT to the address labeled “Intended Recipient.” Approximately 18 seconds later, the same address received TRX dust from “TRX Dusting Address.” Notably, the first and last two characters of this address matched those of the “Intended Recipient” — the dust-sending address was crafted to resemble the legitimate recipient.

Tracing backwards
Blockchain analysis shows that “TRX Dusting Address” was activated in mid-July 2025, and has since conducted approximately 920 outgoing transactions, totaling around 120 TRX (roughly USD 40 as of today).
To further investigate this address, TRM Labs identified two connected entities (highlighted as orange nodes in the image below):
- The first entity appears to have funded “TRX Dusting Address” with TRX used in subsequent dusting activity
- The second likely created or activated “TRX Dusting Address,” and may also be the source of its initial TRX
Tracing this infrastructure back several hops reveals a link to a Virtual Asset Service Provider (VASP). If “TRX Dusting Address” is later confirmed to be involved in a legitimate scam campaign, this VASP may represent a potential pathway to Know Your Customer (KYC) information, depending on applicable jurisdictional access and data-sharing agreements.
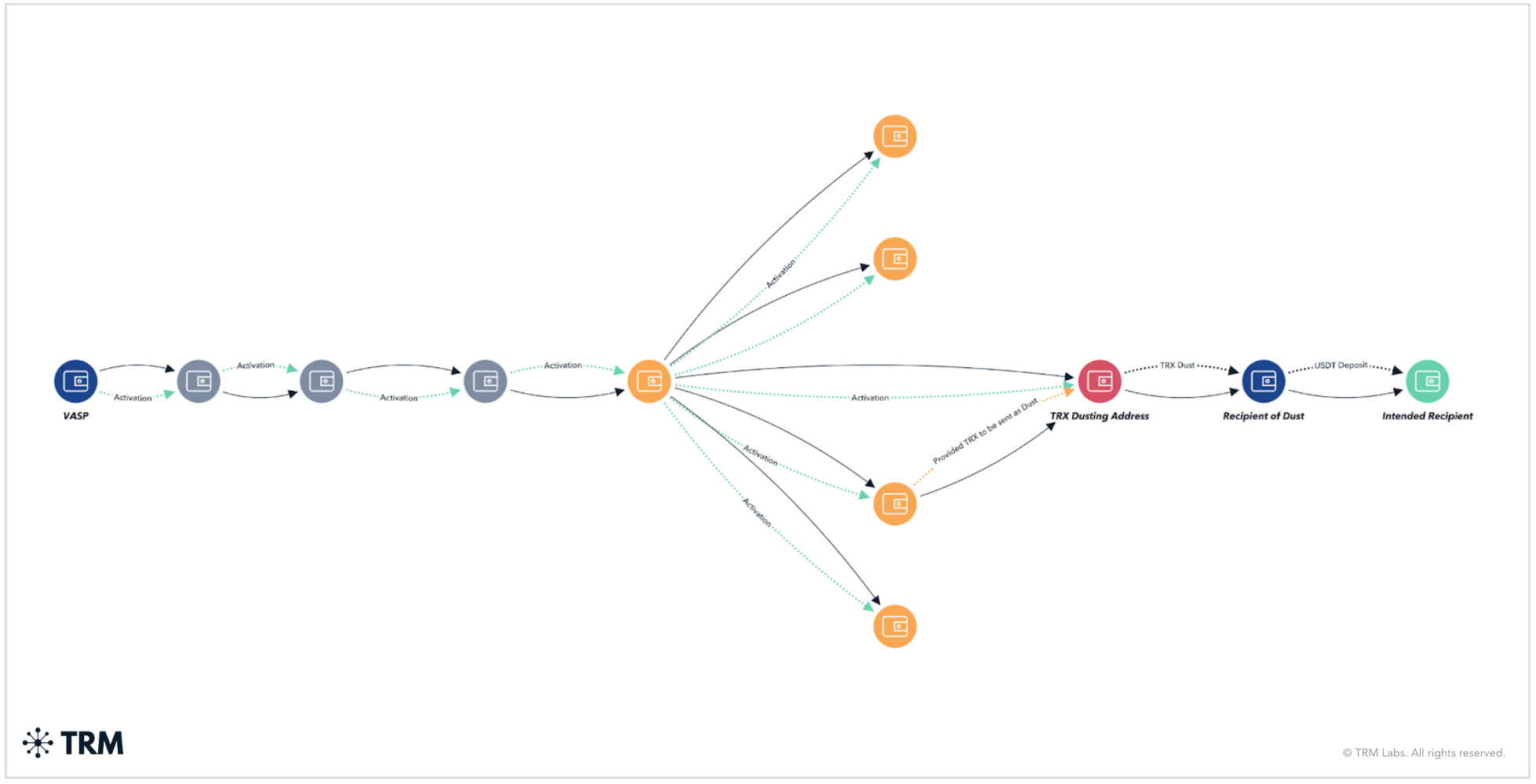
Identifying additional dusting addresses
By analyzing the outgoing transactions from the address that activated “TRX Dusting Address,” TRM Labs identified three additional nodes, each of which received matching TRX deposits from separate sources and subsequently initiated dusting activity. These nodes are visualized in the graph below.
Blockchain analysis indicates that the activating address executed approximately 4,800 AccountCreateContract transactions, suggesting the creation of up to 4,800 new addresses, likely for the purpose of deploying dusting attacks at scale.
While this highlights the scalability and automation of dusting operations on TRON, it also reinforces that these behaviors produce traceable signals — enabling investigators to map infrastructure, surface relationships, and pursue attribution over time.
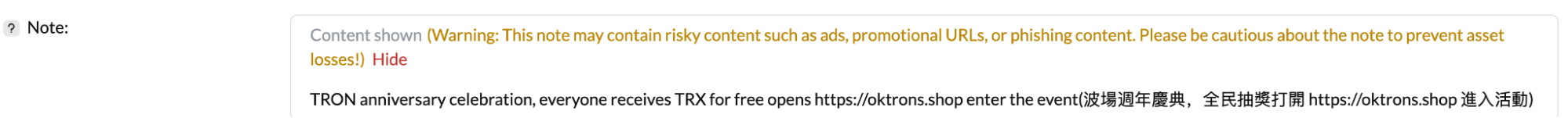
How malicious actors can take advantage of the memo field
On the TRON blockchain, users can attach memo fields to transactions — often used to communicate additional context or instructions. However, this feature can also be abused by malicious actors to promote scams or embed phishing links directly into on-chain metadata.
An example of a memo field is visible on Tronscan in the image below, illustrating how these fields may be used to lure users to off-chain websites or services.
TRM encourages individuals to exercise caution when visiting these websites.
Tips for mitigating the risk of dust attacks on TRON
TRM Labs advises users to:
- Double-check recipient addresses prior to sending a transaction
- Be cautious of incoming dust-level transactions involving receipt of micro amounts of TRX
- Avoid clicking on links found in memo fields unless the source is verified and trusted
This blog post is intended for informational purposes only. Please contact TRM for additional information or investigative requests.
{{horizontal-line}}
Frequently asked questions (FAQs)
1. What is address poisoning?
Address poisoning is a scam tactic in which a malicious actor sends a small amount of cryptocurrency — often worth less than USD 0.01 — to a user’s wallet. These spoofed transactions are designed to mimic legitimate addresses in a user's transaction history, increasing the risk of the user accidentally copying and reusing a scam address.
2. Why is it called “dusting”?
“Dust” refers to the tiny amounts of crypto (e.g. TRX) sent to a user’s wallet — often too small to trade or withdraw. Dusting is used to obscure transaction histories, promote scam tokens, or deceive users into unsafe interactions.
3. How does address poisoning work on TRON?
On TRON, attackers often send dust-level TRX from addresses that visually resemble a user’s previous counterparties. This exploits TRON’s low-cost infrastructure, where micro transactions are virtually free, making large-scale address poisoning campaigns feasible.
4. What’s the difference between dusting and AirDrops?
While both involve unsolicited token transfers, AirDrops are typically promotional and transparent. Dusting attacks, by contrast, aim to confuse, mislead, or monitor users — often for phishing, de-anonymization, or scam promotion.
5. What do scammers hope to achieve with dusting?
Common objectives include:
- Phishing: Tricking users into sending funds to lookalike addresses
- Behavioral tracking: Observing how users handle small balances to link wallets or identify high-value targets
- Scam promotion: Embedding phishing links or fake token metadata to lure user interaction
6. How can I tell if my wallet has been dusted?
If you receive a TRX transfer worth a fraction of a cent from an unknown or suspicious-looking address — especially one that visually resembles a known contact — it may be part of a dusting attempt. TRON users often refer to these as “TRX dust” transactions.
7. Can these attacks be automated?
Yes. Many dusting campaigns are run by bots that:
- Monitor blockchain activity for newly active or high-value wallets
- Generate spoofed addresses using vanity tools
- Trigger dusting transactions within seconds of user activity
8. Who is most likely to be targeted by dusting?
Attackers tend to focus on:
- Wallets with recent or high-value activity
- First-time interactions between wallets (to insert lookalike senders)
- Non-custodial wallets, which offer fewer transaction filters
9. Is dusting always malicious?
Not necessarily — but it is often suspicious by default. While a few use cases may be benign, dusting on TRON is overwhelmingly associated with scam infrastructure and deception tactics. Users are advised not to engage with unsolicited tokens.
10. Can TRX dusting be traced?
Yes. Blockchain intelligence tools can:
- Identify and cluster attacker infrastructure
- Flag users who interacted with spoofed addresses
- Connect dusting wallets across scam campaigns
This provides investigative signals that support attribution and remediation efforts.
11. What’s the role of memo fields in TRON scams?
Scammers may use memo fields to embed phishing links or fraudulent messages in transactions. These fields are visible in tools like Tronscan and can redirect users to unsafe websites if clicked.
12. What should I do if I receive TRX dust?
TRM Labs recommends:
- Avoid engaging with unknown tokens or addresses
- Verify addresses before copying and pasting
- Ignore links in memo fields unless the source is confirmed
When in doubt, treat unsolicited micro-deposits as suspicious and do not interact.
{{horizontal-line}}
About TRM Labs
TRM Labs provides blockchain analytics solutions to help law enforcement and national security agencies, financial institutions, and cryptocurrency businesses detect, investigate, and disrupt crypto-related fraud and financial crime. TRM’s blockchain intelligence platform includes solutions to trace the source and destination of funds, identify illicit activity, build cases, and construct an operating picture of threats. TRM is trusted by leading agencies and businesses worldwide who rely on TRM to enable a safer, more secure crypto ecosystem. TRM is based in San Francisco, CA, and is hiring across engineering, product, sales, and data science. To learn more, visit www.trmlabs.com.






















