US Treasury Sanctions North Korean Cyber Facilitator Linked to IT Worker Scheme

On July 8, 2025, the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) designated Song Kum Hyok, a DPRK-based cyber actor affiliated with the North Korean hacking unit Andariel. Song played a central role in orchestrating an IT worker scheme, recruiting North Korean nationals to obtain remote employment at unsuspecting companies using falsified identities and U.S. personal information. These workers operated from countries including China and Russia, providing illicit revenue streams to the Kim regime. OFAC also designated one individual and four entities linked to a Russia-based DPRK IT worker network.
“Today’s action underscores the importance of vigilance on the DPRK’s continued efforts to clandestinely fund its WMD and ballistic missile programs,” said Deputy Secretary of the Treasury Michael Faulkender. “Treasury remains committed to using all available tools to disrupt the Kim regime’s efforts to circumvent sanctions through its digital asset theft, attempted impersonation of Americans, and malicious cyber-attacks.”
The action highlights the role of the DPRK’s Reconnaissance General Bureau (RGB) in supporting weapons development through cyber-enabled operations and reinforces prior sanctions on groups including Lazarus, Bluenoroff, and the Technical Reconnaissance Bureau. In announcing the designations, Treasury officials emphasized the threat posed by North Korea’s continued digital asset theft and the exploitation of US systems to evade sanctions.
North Korea’s global IT worker threat
The designation highlights a growing method of revenue generation for North Korea: the deployment of thousands of skilled IT workers embedded in tech and crypto companies worldwide. These individuals mask their origins using stolen documents, proxies, and aliases to apply for remote jobs — often in Web3, software development, or blockchain infrastructure. Payments made to these workers, typically in USDC or USDT, are laundered through complex wallet structures, privacy tools, and conversion channels, ultimately benefiting DPRK-controlled entities.
Song’s role in this scheme involved creating false personas using US citizens’ personal data to secure job placements for DPRK operatives. The broader network includes companies based in Russia that contracted directly with North Korean trading firms to deploy workers under long-term agreements, further entrenching the regime’s access to foreign income.
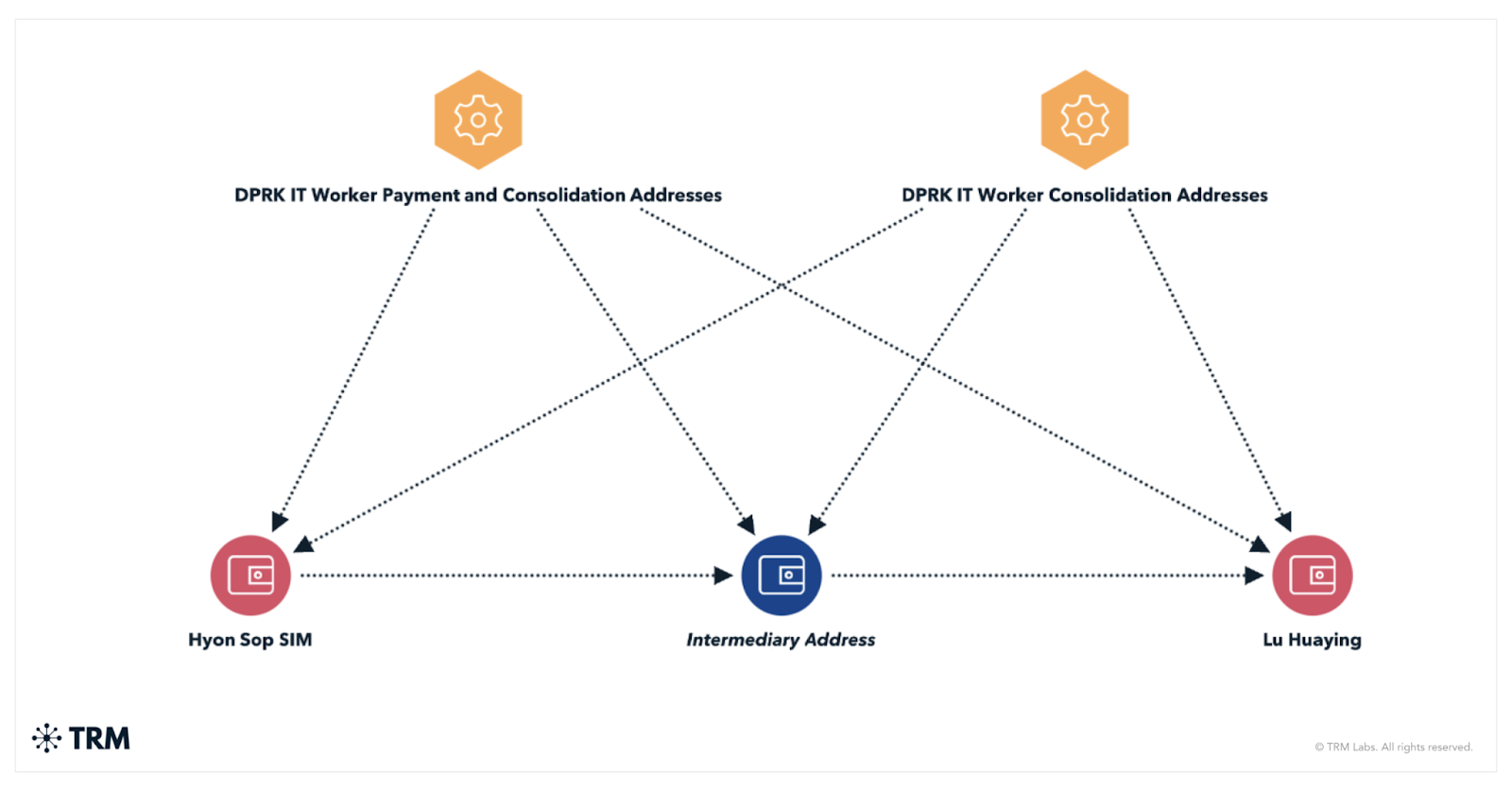
Coordinated US government action: OFAC, DOJ, and FBI
Today’s OFAC action follows a series of moves by the U.S. government targeting the same ecosystem with a focus on building out networks of facilitators like Song. On June 5, 2025, the Department of Justice filed a civil forfeiture complaint in the District of Columbia seeking over USD 7.7 million in cryptocurrency, NFTs, and digital assets tied to a laundering network operated by North Korean IT workers. These workers were embedded in crypto companies and tech startups, using fraudulent identities like “Joshua Palmer” and “Alex Hong” to collect stablecoin payments from US employers.
According to DOJ, the proceeds — often routed through centralized exchanges and self-hosted wallets — were consolidated and transferred to senior DPRK operatives, including Kim Sang Man and Sim Hyon Sop, both previously sanctioned. Investigators uncovered extensive use of Russian and UAE-based infrastructure, IP addresses, and fake documentation, underscoring the international scale of the scheme.
The FBI and other law enforcement partners successfully seized digital assets linked to these laundering operations, including USDC, ETH, and high-value NFTs. Wallet activity showed a systematic effort to fragment and obfuscate funds before conversion to fiat through OTC brokers, including one sanctioned by OFAC in late 2024.
Surge in North Korea-linked crypto hacks in H1 2025
The first half of 2025 has seen a dramatic increase in crypto-related thefts. According to TRM, threat actors stole over USD 2.1 billion stolen across 75 hacks and exploits. North Korea is responsible for approximately USD 1.6 billion of those losses — nearly 70% — driven by the USD 1.5 billion Bybit hack. While exchange breaches remain significant, DPRK-linked operations are increasingly shifting toward deception-based revenue generation, including IT worker infiltration.
TRM Labs continues to track these evolving threats, supporting global law enforcement and national security agencies in investigating hacks, tracing laundering flows, and helping freeze and recover illicit assets. From network analysis to tracking illicit IT worker payments, TRM's intelligence tools remain central to countering North Korea’s misuse of the crypto ecosystem.
Access our coverage of TRON, Solana and 23 other blockchains
Fill out the form to speak with our team about investigative professional services.






















