Investigator Insights: How to Analyze Gnosis Safes in Blockchain Investigations

Key takeaways
- Gnosis Safes (now often called Safe Smart Accounts) are multisig smart contract wallets that require multiple approvals to execute transactions — improving treasury security but complicating investigations.
- Illicit actors increasingly exploit Gnosis Safes to store, route, or obscure stolen crypto — often configuring them to mimic legitimate setups or layering them to hide control.
- Investigators can identify Safes on-chain via indicators like the GnosisSafeProxy contract name, use of the Safe Proxy Factory, and unique transaction patterns requiring no token transfer.
- Signer-level analysis reveals attribution opportunities, especially when Safe owners also use linked wallets on centralized exchanges or participate in other known activity.
- Advanced Safe features like modules and nesting increase obfuscation risk, requiring investigators to trace control structures, signer behavior, and transaction automation logic.
{{horizontal-line}}
Gnosis Safes, which are now often referred to as Safe Smart Accounts, are multi-signature smart contract wallets that offer enhanced security for digital assets.
While they’re commonly used by Decentralized Autonomous Organizations (DAOs), protocols, and crypto-native businesses, investigators are increasingly encountering them in high-profile hacks, fraud schemes, and sanctions evasion activity. Gnosis Safes have been used in several prominent attacks in recent years:
- 2025 ByBit hack — in which DPRK-affiliated actors injected malicious JavaScript into the Safe{Wallet} UI, tricking authorized signers into approving a handover of control)
- 2024 Radiant Capital exploit and 2024 WazirX incident — in which Gnosis Safes were used as part of broader attack chains to temporarily secure or route illicit funds
In this article, we’ll explore what Gnosis Safes are, how investigators can identify them on-chain, and how to extract meaningful intelligence during an investigation.
What is a Gnosis Safe?
A Gnosis Safe is a smart contract wallet that requires multiple owners to approve a transaction before it can be executed. Instead of relying on a single private key, Gnosis Safes operate using a threshold model — for example, requiring two of three or five of seven designated owners to approve any movement of funds.
This distributed control minimizes the risk of a single point of failure, enables collaborative management of shared treasuries, and creates a clear on-chain trail of approvals from known addresses. Gnosis Safes are also highly configurable. Users can add or remove owners, set or adjust the signature threshold, and enable optional modules to customize wallet behavior.
Why do Gnosis Safes matter for investigators?
From a compliance or investigative standpoint, Gnosis Safes offer both opportunities and challenges.
Illicit actors use Gnosis Safes as “secure vaults” to manage stolen funds, obfuscate control, or enforce internal guardrails within criminal groups. They can also be used to fake legitimacy. For example, a fraudulent project might create a five-of-five multisig wallet to manage investor funds but secretly control all five keys. On the surface, it looks secure. In practice, it’s a rug pull waiting to happen.
How to identify a Gnosis Safe on-chain
1. Use blockchain explorers
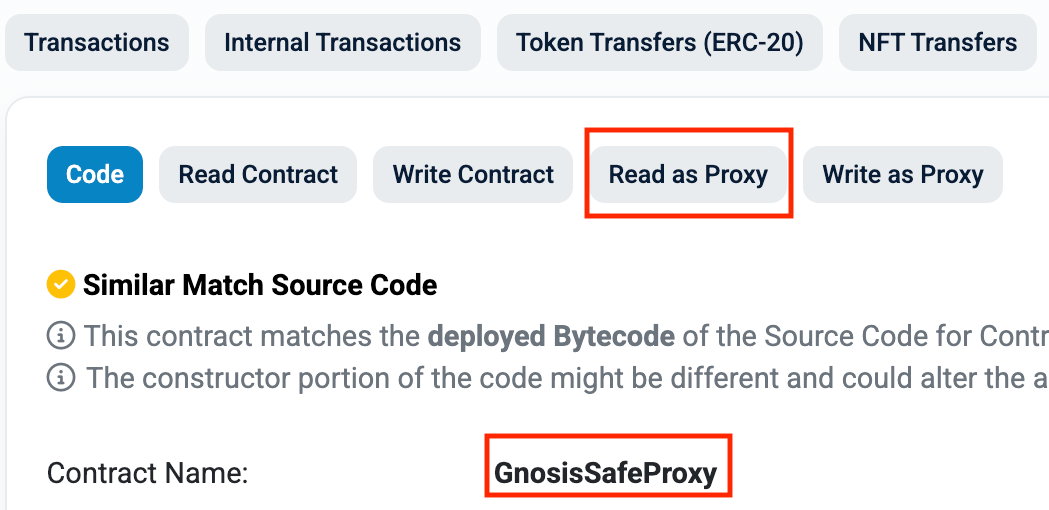
The simplest way to identify a Gnosis Safe is by viewing the contract details.
- The contract name may appear as GnosisSafeProxy
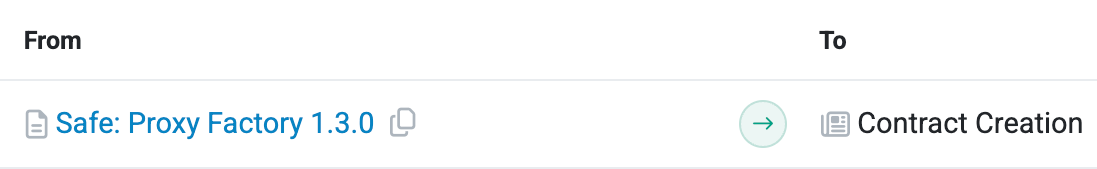
- Internal transactions often show deployment via the Safe Proxy Factory
- The contract’s source code and bytecode are usually publicly verified
2. Use visual graphing tools
Tools like TRM Forensics can highlight:
- Safe creation transactions, which typically involve zero token value and only incur gas fees — standard transaction costs for using a blockchain
- Entities interacting with the Safe, including signers and connected addresses
For example, On Avalanche, a Safe creation might show an AVAX transaction to the Safe Proxy Factory, followed by contract instantiation with no funds moved — a typical deployment pattern.
How to investigate ownership and activity
Each Gnosis Safe has a set of owners, or “signers,” which are explicitly stored in the smart contract state. Investigators can view these owners directly in block explorers or tools like TRM Forensics, track which owner initiated, signed, or confirmed each transaction, and monitor changes to Safe settings (e.g. if a signer was removed after a suspicious transfer).
Owners can propose and approve transactions, modify Safe configuration (e.g. thresholds, signer list), and interact with other smart contracts on behalf of the Safe.
Understanding which signers were active in key moments and how they relate to other infrastructure is critical for attribution.
Case study: Tracing the signer
In one observed transaction, a Gnosis Safe on the Avalanche blockchain network sent 249,999,980 Lighter tokens to an external wallet. Further investigation revealed that the initiating signer had received funds from a centralized exchange. This could provide very interesting insights for law enforcement — particularly in terms of Know Your Customer (KYC) records.
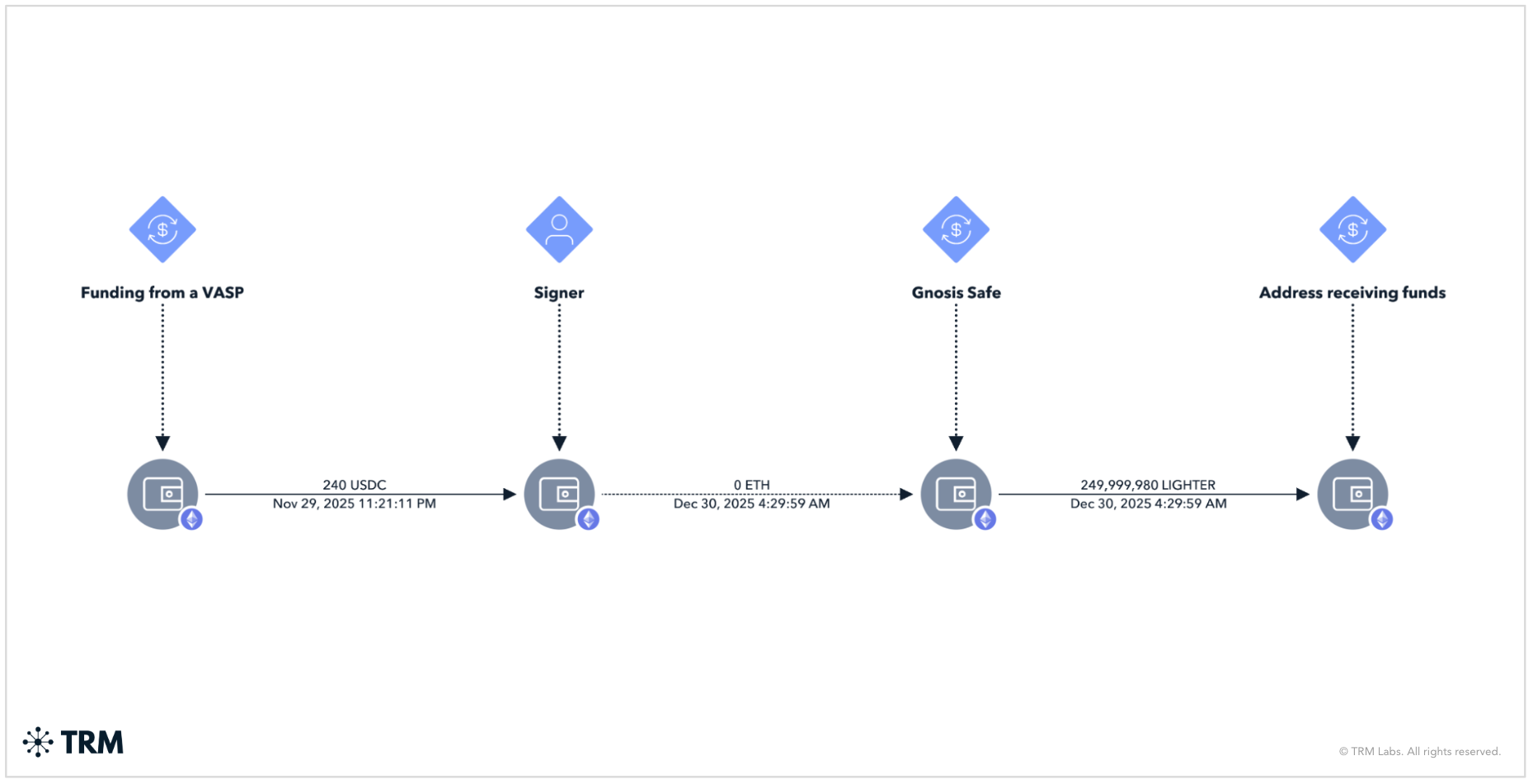
This pattern — where Safe signers double as operational wallets — allows investigators to connect infrastructure, even when assets don’t move directly between known entities.
Advanced techniques: Thresholds, modules, and nested Safes
Threshold analysis
Understanding the Gnosis Safe’s threshold is key. If three of five owners are required to move funds, investigators may need to identify only those three most active wallets to map control. Thresholds are stored in the Safe’s on-chain infrastructure and are visible via tools like Etherscan or app.safe.global.
Modules and custom behaviors
Gnosis Safes can support optional modules, which allow additional logic to govern transactions. For example: auto-splitting funds to multiple wallets or automatically triggering transfers when balances hit a certain threshold.
Illicit actors may use these modules to pre-program exits, bypassing the normal multisig protections without raising alarms.
Nested Safes
In some setups, one Safe is used as an owner of another — adding a layer of indirection and making attribution harder. Tracing the nested structure can reveal larger operational setups or laundering paths.
Using Safe App for additional intelligence
Investigators can also use app.safe.global to input a Safe address and view signer addresses and thresholds, review detailed transaction metadata (including who proposed and who confirmed each transaction), and identify discrepancies between signer activity and expected behavior. This interface supplements blockchain explorer data and offers a human-readable view of wallet configuration and operations.
Questions investigators should ask when dealing with a Gnosis Safe
Gnosis Safes are powerful security tools. And investigators are likely to increasingly encounter them more often — as both legitimate protocols and obfuscation tools for sophisticated threat actors.
Some key questions to ask when you see a Gnosis Safe:
- Who are the real operators?
- What configuration does the Safe use — and has it changed?
- Are there signs of obfuscation (e.g. nested wallets, modules, signer overlap)?
- Can I map signer activity to prior incidents or infrastructure?
By analyzing not just the Safe itself, but the people and permissions behind it, investigators can better trace illicit flows, strengthen attribution, and anticipate how actors adapt.
{{horizontal-line}}
Frequently asked questions (FAQs)
1. What is a Gnosis Safe?
A Gnosis Safe (also known as a Safe Smart Account) is a multi-signature smart contract wallet that requires a set number of approvals to authorize a transaction. It offers enhanced security, transparency, and control compared to single-signature wallets.
2. Why are Gnosis Safes relevant in blockchain investigations?
They are increasingly used by threat actors to manage stolen funds, simulate legitimacy, or obscure ownership. Their multisig structure can make it harder to trace asset control, but also provides investigators with a clear trail of signer activity.
3. How can I identify a Gnosis Safe on-chain?
Look for contract names like GnosisSafeProxy, creation via the Safe Proxy Factory, and zero-value contract deployments. Tools like TRM Forensics and block explorers like Etherscan can highlight these patterns and expose signer interactions.
4. Where can I find the list of Safe signers?
Signer addresses are stored in the Safe’s smart contract and can be viewed on platforms like Etherscan, app.safe.global, or TRM Forensics. These tools also reveal signer activity, threshold settings, and configuration changes.
5. What are the risks of nested Gnosis Safes?
Nested Safes occur when one Safe controls another. This setup can mask true ownership and delay attribution. Investigators need to trace the full ownership chain to uncover operational intent and control.
6. Can actors use modules to bypass Safe security?
Yes. Modules can automate transactions or trigger activity outside standard signer approval. Illicit users may leverage them for stealth exits or rapid fund distribution, avoiding detection by relying on custom logic.
7. How do Safe thresholds impact attribution?
Thresholds define how many signers are needed for a transaction. Knowing the threshold helps narrow the focus to the most active or relevant signers — which can inform control mapping and investigative leads.
8. How are Gnosis Safes used to simulate legitimacy?
Fraudulent actors may configure a Safe to appear secure — for example, setting up a five-of-five multisig — while secretly controlling all keys. This tactic is often used in rug pulls and deceptive fundraising.
Access our coverage of TRON, Solana and 23 other blockchains
Fill out the form to speak with our team about investigative professional services.






















