DOJ Targets Hamas-Linked BuyCash Exchange in $2 Million Civil Forfeiture for Terrorist Financing

This week, the US Justice Department and the US Attorney’s Office for the District of Columbia announced the unsealing of a civil forfeiture action against approximately USD 2 million in digital currency connected with BuyCash, a Gaza-based money transfer business that was involved in financially supporting Hamas – a designated Foreign Terrorist Organization (FTO) – as well as its agents and collaborators.
TRM is proud to have supported law enforcement in this investigation.
This action, brought under the federal terrorism forfeiture statute, represents one of the most comprehensive public disclosures of blockchain tracing in a terrorism financing case since the Justice Department’s 2020 takedown of three global terror finance cyber-campaigns. It underscores how Hamas operatives exploited both cryptocurrency and traditional financial infrastructure—leveraging cross-border platforms to raise funds, move assets, and conceal the origin and destination of illicit proceeds.
Background: Hamas, BuyCash, and Prior Designations
On October 18, 2023, the US Treasury Department’s Office of Foreign Assets Control (OFAC) sanctioned BuyCash and its founder, Ahmed M. M. Alaqad, alongside ten Hamas operatives and facilitators based in Gaza, Türkiye, Qatar, and other countries. BuyCash, operational since at least 2014, positioned itself as a multi-purpose remittance platform and cryptocurrency exchange, with a website marketing services including money transfers and e-banking. It had previously appeared in terrorism financing investigations. In June 2021, Israel’s National Bureau for Counter Terror Financing (NBCTF) seized several virtual currency wallets linked to Hamas fundraising; some were directly tied to BuyCash. According to OFAC, the company had been used not only by Hamas but also by affiliates of al-Qa’ida and ISIS.
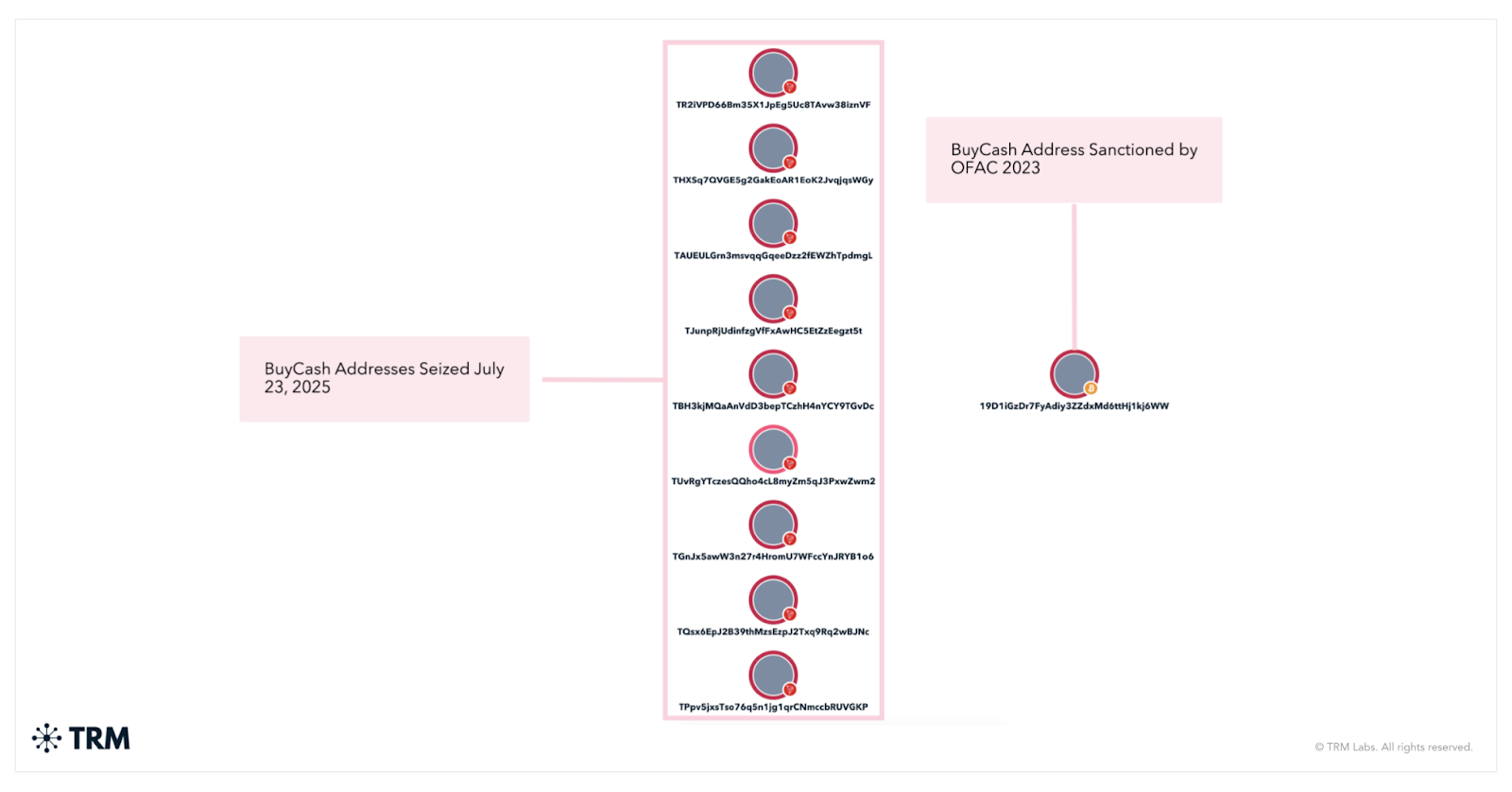
The Forfeiture Action: Tracing Terrorist Financing Through Crypto
The DOJ's civil forfeiture complaint, filed in the US District Court for the District of Columbia, traces nearly 150 digital asset wallets used to funnel funds to or through BuyCash, many of which were used in direct connection with Hamas fundraising campaigns. The complaint is grounded in 18 U.S.C. § 981(a)(1)(G)(i), which allows for the forfeiture of assets that constitute the property of foreign terrorist organizations or are intended to support such organizations.
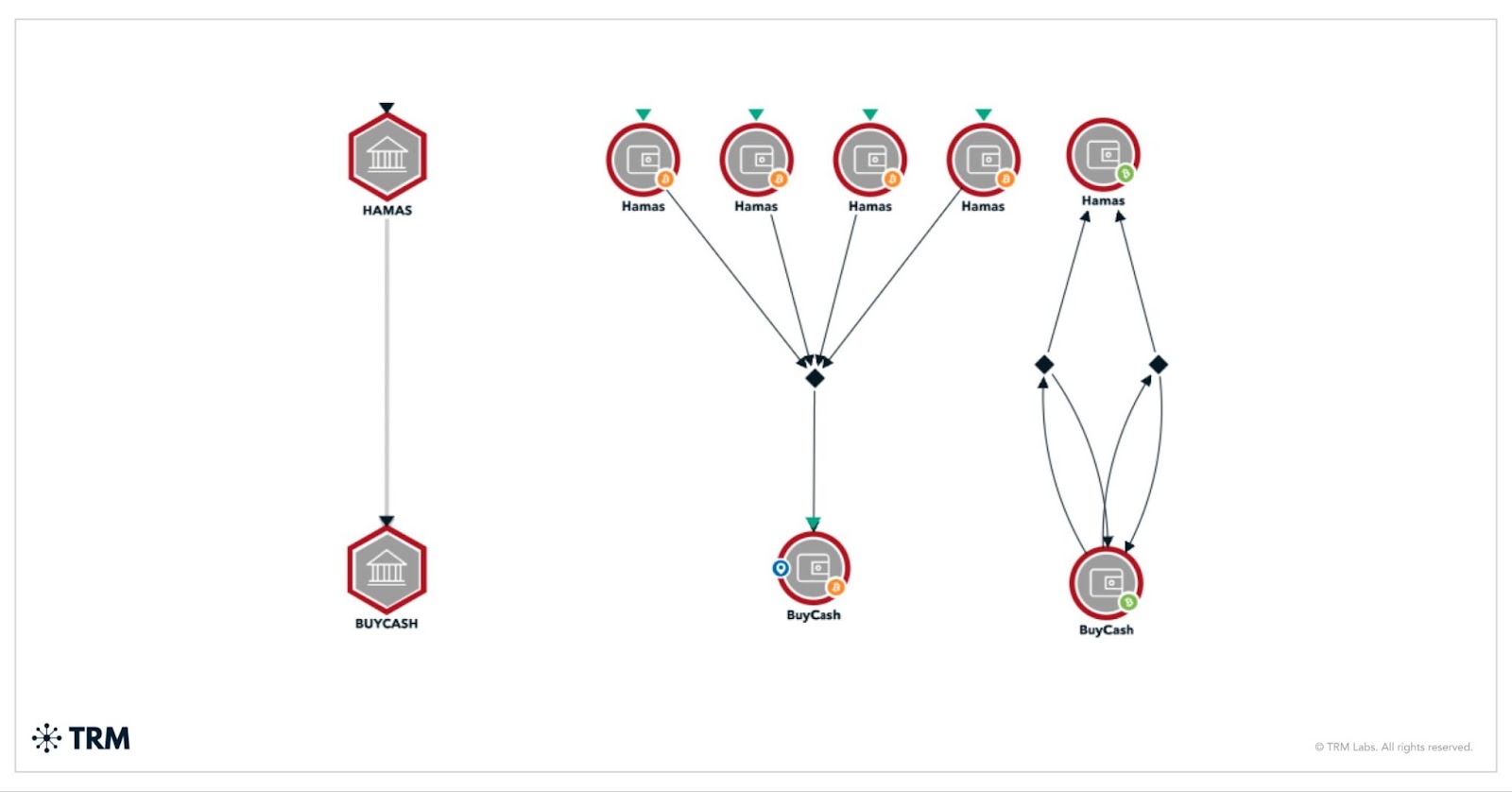
According to the complaint, Hamas operatives solicited cryptocurrency donations through Telegram and other online platforms as early as 2021, often under campaigns associated with the al-Qassam Brigades, the military wing of Hamas. Wallet addresses were promoted publicly, with instructions for donors to send funds in Bitcoin or other cryptocurrencies. These funds would then flow into intermediary wallets and ultimately reach addresses controlled by BuyCash.
Key Tracing Highlights
The DOJ’s tracing effort revealed several consistent movement patterns:
Consolidation into BuyCash-Linked Wallets
DOJ investigators used TRM to trace donations from Hamas-affiliated fundraising campaigns to wallets linked to BuyCash. One such wallet, as shown in the complaint in TRM, referred to as Address-WGy, became active on July 3, 2023, receiving approximately 110,000 USDT in its first transaction. On the same day, it received 1,295 TRX (valued at around USD 101) from Address-mgL. TRX is commonly used to pay for transaction fees on the Tron network, and such funding transactions often reveal shared control over addresses. This early linkage allowed investigators to connect associated wallets and identify potential operator-controlled infrastructure.

Behavioral Patterns and Cross-Wallet Flow
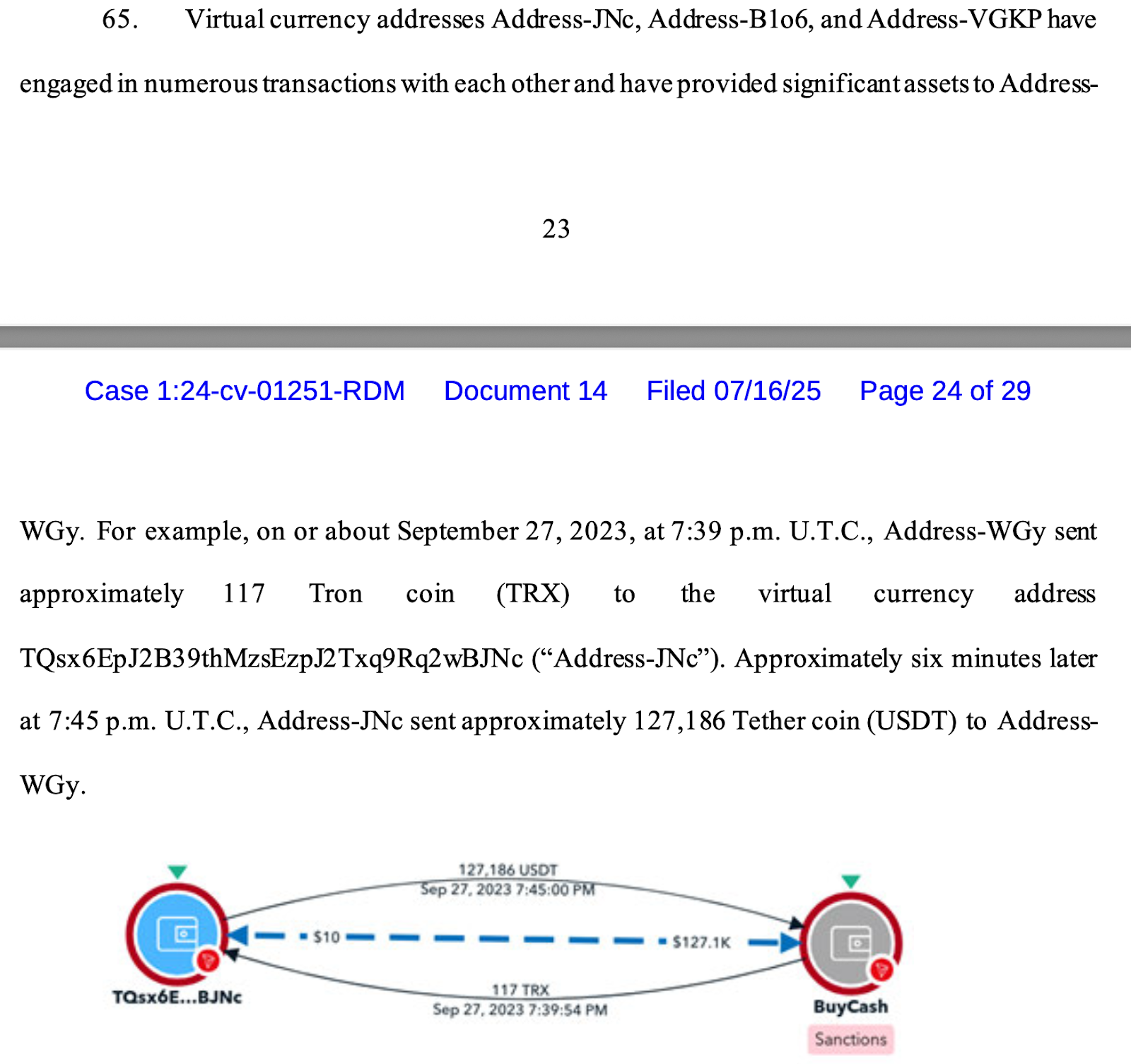
Shortly after receiving TRX, Address-WGy sent back 3,000 USDT to Address-mgL, creating a transactional loop that further established a behavioral link. This back-and-forth movement—a hallmark of controlled wallets—helped trace further downstream activity. Investigators later determined that Address-JNc, Address-B1o6, and Address-VGKP engaged in frequent inter-wallet transactions and collectively sent significant funds to Address-WGy, reinforcing the understanding that these were operated by a coordinated entity.
On September 27, 2023, for instance, Address-WGy sent 117 TRX to Address-JNc, and just six minutes later, Address-JNc sent 127,186 USDT back to Address-WGy, revealing a rapid, two-way flow of funds and reinforcing a likely link in operational control.
Conversion and Obfuscation Attempts
As part of the movement strategy, wallets controlled by this network would route funds through intermediaries like Address-pAK, which was used to quickly move assets across multiple wallets to conceal the source. On November 14, 2023, Address-WGy sent 100 TRX to Address-pAK, which had a known role in transferring funds between wallets in a rapid, layered fashion—indicative of deliberate obfuscation to evade detection or sanctions.

Movement to Fiat-Offramps and Aggregated Transfers
Funds were eventually funneled to accounts at third-party platforms—likely exchanges—where fiat offramps were available. For example, between October 3 and October 21, 2023, a wallet referred to as Address-GvDc sent approximately USD 1.64 million to Account-7294, an identified fiat off-ramp. These transfers followed a prior set of movements from Address-WGy to Address-GvDc, creating a clear pipeline from donation to liquidation.
Another notable transaction shows that USD 93,230 was sent to Account-744, reinforcing the fact that the traced crypto ultimately exited the blockchain ecosystem through identifiable accounts, likely held at centralized exchanges.

Together, this evidence forms the backbone of the DOJ’s civil forfeiture strategy under the terrorism forfeiture statute. It shows how a Hamas-linked fundraising network—including designated actors and BuyCash—used a complex set of wallets and transactions to receive, move, and off-ramp illicit crypto, all of which was visible through the blockchain and traceable by law enforcement.
A Whole-of-Government Approach to Disrupting Terrorist Finance
The DOJ’s civil forfeiture complaint underscores how blockchain intelligence, paired with interagency coordination, can provide unprecedented visibility into terror finance networks. In this case, US officials used advanced blockchain tracing tools to follow the digital fingerprints of Hamas-linked funds as they moved across borders, protocols, and intermediary platforms.
Filed under the federal terrorism forfeiture statute, the complaint allows the US government to seize assets directly tied to designated foreign terrorist organizations—without requiring a criminal conviction. It’s a critical tool for disrupting foreign-based money service businesses that operate in support of groups like Hamas. Here, the assets at issue—currently frozen by cooperating exchanges—were traced back to Gaza-based BuyCash and linked wallets, which served as conduits for illicit fundraising and laundering.
This case reflects a whole-of-government response. Law enforcement partnered with national security, regulatory, and private sector actors to identify, trace, and freeze assets, cutting off a key financial channel for a US-designated terror group. It also reflects a paradox of digital assets in terror finance: while crypto enables faster, borderless movement of funds, it also leaves behind a permanent, traceable ledger. In the case of BuyCash, that transparency enabled investigators to uncover and disrupt a complex, multi-hop laundering network used to mask the flow of funds tied to Hamas and other US-designated organizations.
The US government’s ability to pursue and seize illicit digital assets—regardless of jurisdiction—sets a precedent for future efforts targeting terror-linked financial infrastructure. And it shows how blockchain intelligence, combined with public-private collaboration, can translate visibility into disruption in real time.
According to DOJ, the FBI’s Washington Field Office is leading the investigation. Assistant US Attorneys Rajbir S. Datta and Thomas Saunders for the District of Columbia are prosecuting the case, with support from Trial Attorney Allison Ickovic of the Criminal Division’s Money Laundering and Asset Recovery Section (MLARS) and Deputy Chief Alicia Cook of the National Security Division. Critical support was provided by Paralegal Specialists Brian Rickers and Gina Torres, the Department of Justice’s Office of International Affairs, and Tether, which assisted in the transfer of the seized assets.
FAQs for DOJ Targets Hamas-Linked BuyCash Exchange in USD 2 Million Civil Forfeiture for Terrorist Financing
What is BuyCash, and why was it targeted?
BuyCash is a Gaza-based money transfer and cryptocurrency exchange that marketed itself as a multi-service remittance and e-banking platform. The U.S. Treasury’s Office of Foreign Assets Control (OFAC) sanctioned BuyCash and its founder, Ahmed M. M. Alaqad, in October 2023 for providing material support to Hamas. BuyCash had previously been implicated in Hamas fundraising operations, and also in financial activity involving affiliates of al-Qa’ida and ISIS. The US Justice Department’s recent civil forfeiture complaint targets roughly $2 million in digital assets associated with BuyCash, citing its role in facilitating terrorism financing.
What legal authority did the U.S. use to file this action?
The forfeiture action was filed under 18 U.S.C. § 981(a)(1)(G)(i), a federal terrorism forfeiture statute that allows the U.S. government to seize assets tied to foreign terrorist organizations or used in support of their operations. The statute does not require a criminal conviction, making it a powerful tool for disrupting overseas networks that fund terrorism but operate beyond traditional criminal jurisdiction.
How did law enforcement trace the funds?
Investigators used blockchain intelligence tools—including TRM Labs—to trace donations made to Hamas-affiliated fundraising campaigns. These campaigns often promoted wallet addresses via Telegram and other platforms. From there, investigators followed the funds across nearly 150 wallets, many of which converged on addresses linked to BuyCash. Wallet behaviors—like inter-wallet transfers, transactional loops, and timing patterns—helped establish links between accounts. Funds ultimately exited through identifiable fiat offramps.
What kinds of transactions stood out in the tracing effort?
One wallet, Address-WGy, received over 110,000 USDT in a single transaction and also received 1,295 TRX—used for transaction fees—from another wallet (Address-mgL), suggesting shared control. Subsequent transfers between Address-WGy and Address-JNc, Address-B1o6, and others revealed rapid, repeated movements, common in laundering patterns. In some cases, funds were routed through intermediary wallets like Address-pAK in an apparent attempt to obscure origins. Finally, large sums—over $1.6 million—were sent to fiat-offramps like Account-7294.
Why is this case important for counterterrorism financing efforts?
This action marks one of the most detailed public uses of blockchain tracing in a terrorism financing case since DOJ’s 2020 disruption of al-Qa’ida and ISIS crypto campaigns. It shows how digital assets—while fast and borderless—leave a transparent ledger that enables law enforcement to trace even complex laundering efforts. It also signals that U.S. agencies will aggressively pursue illicit crypto activity tied to terrorist organizations, even when those actors operate overseas.
What makes this a “whole-of-government” response?
The investigation and forfeiture action reflect cooperation between law enforcement, national security, regulatory agencies, and the private sector. The FBI’s Washington Field Office led the case. DOJ attorneys from multiple divisions—including the National Security Division and the Money Laundering and Asset Recovery Section—contributed. Private sector actors like TRM Labs provided tracing support, and Tether assisted in seizing and transferring the assets. It’s a model of public-private collaboration.
Were the assets seized or just frozen?
According to DOJ, the assets are currently frozen by cooperating exchanges and may now be seized through the civil forfeiture process. Unlike criminal forfeiture, which follows a conviction, civil forfeiture can occur based on the property’s ties to terrorism financing—critical when dealing with non-U.S.-based actors or platforms.
Does this case set a precedent?
Yes. It reinforces the US government’s willingness and ability to trace and seize crypto assets linked to foreign terror finance networks, using civil legal tools. It also signals to crypto exchanges and wallet providers that they may be expected to cooperate in future enforcement actions and must be able to identify and freeze suspect assets when requested.
What role did TRM Labs play?
TRM Labs provided blockchain intelligence support to law enforcement, helping trace illicit funds and uncover wallet behaviors consistent with laundering and obfuscation. Tools like TRM enabled DOJ to piece together the movement of funds across wallets, protocols, and offramps—key to building the complaint and securing the forfeiture.
Access our coverage of TRON, Solana and 23 other blockchains
Fill out the form to speak with our team about investigative professional services.






















