Operation Prince: Inside the Global Effort That Led to the Largest Forfeiture in US History

The Prince Group Indictment
Last week, the US Department of Justice announced the indictment of Cambodian national Chen Zhi, also known as Vincent, 37, founder and chairman of Prince Holding Group, a multinational conglomerate based in Cambodia. Zhi was charged with wire fraud conspiracy and money laundering conspiracy for directing Prince Group’s operation of forced-labor scam compounds across the country.
In a parallel action, the DOJ filed a civil forfeiture complaint for 127,271 bitcoin—valued at more than USD 15 billion—now in the custody of the US government. The filing marks the largest forfeiture action in US history, underscoring both the scale of the criminal network and the unprecedented reach of law enforcement’s response.
Concurrently, the US Treasury Department’s Office of Foreign Assets Control (OFAC), working with the U.K. Foreign, Commonwealth & Development Office (FCDO), sanctioned 146 targets linked to the Prince Group. The Financial Crimes Enforcement Network (FinCEN) finalized its Section 311 order against the Huione Group, cutting the organization—and any intermediary bank—off from the US dollar system.
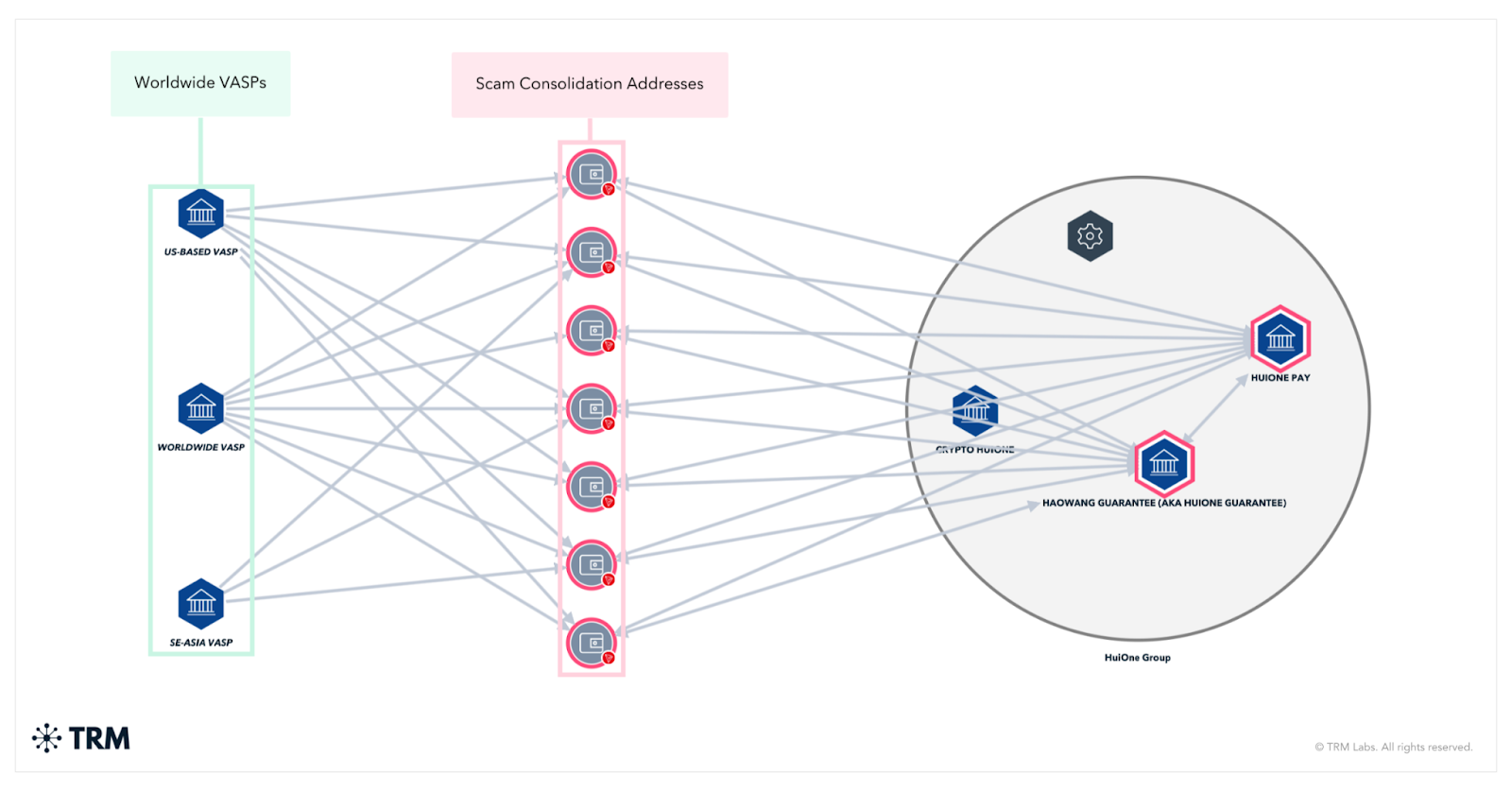
A Transnational Fraud Empire
The DOJ’s forfeiture complaint reads like an anatomy of a state-protected criminal enterprise. It outlines how Prince Group—under the guise of a real estate and investment conglomerate—evolved into what prosecutors describe as “one of the largest transnational criminal organizations in Asia.” Operating from more than ten forced-labor compounds across Cambodia, the network trafficked and imprisoned workers who were forced to run “pig-butchering” investment scams targeting victims across the world, including in the United States.

By 2018, Prince Group was earning more than USD 30 million per day from fraudulent crypto-investment schemes and related criminal activities. Each call center, often disguised as a tech company or financial firm, generated hundreds of millions to billions annually. The complaint describes compounds surrounded by walls, guards, and barbed wire—where workers who failed to meet daily targets were beaten or electroshocked.
The organization’s infrastructure extended far beyond Cambodia’s borders. The forfeiture complaint details how Prince Group integrated its operations into real estate projects and shell companies across Singapore, Hong Kong, Palau, the Cayman Islands, the British Virgin Islands, and even the United States, creating a network of laundering pipelines designed to disguise the origin of the fraud proceeds.
The USD 15 Billion Forfeiture
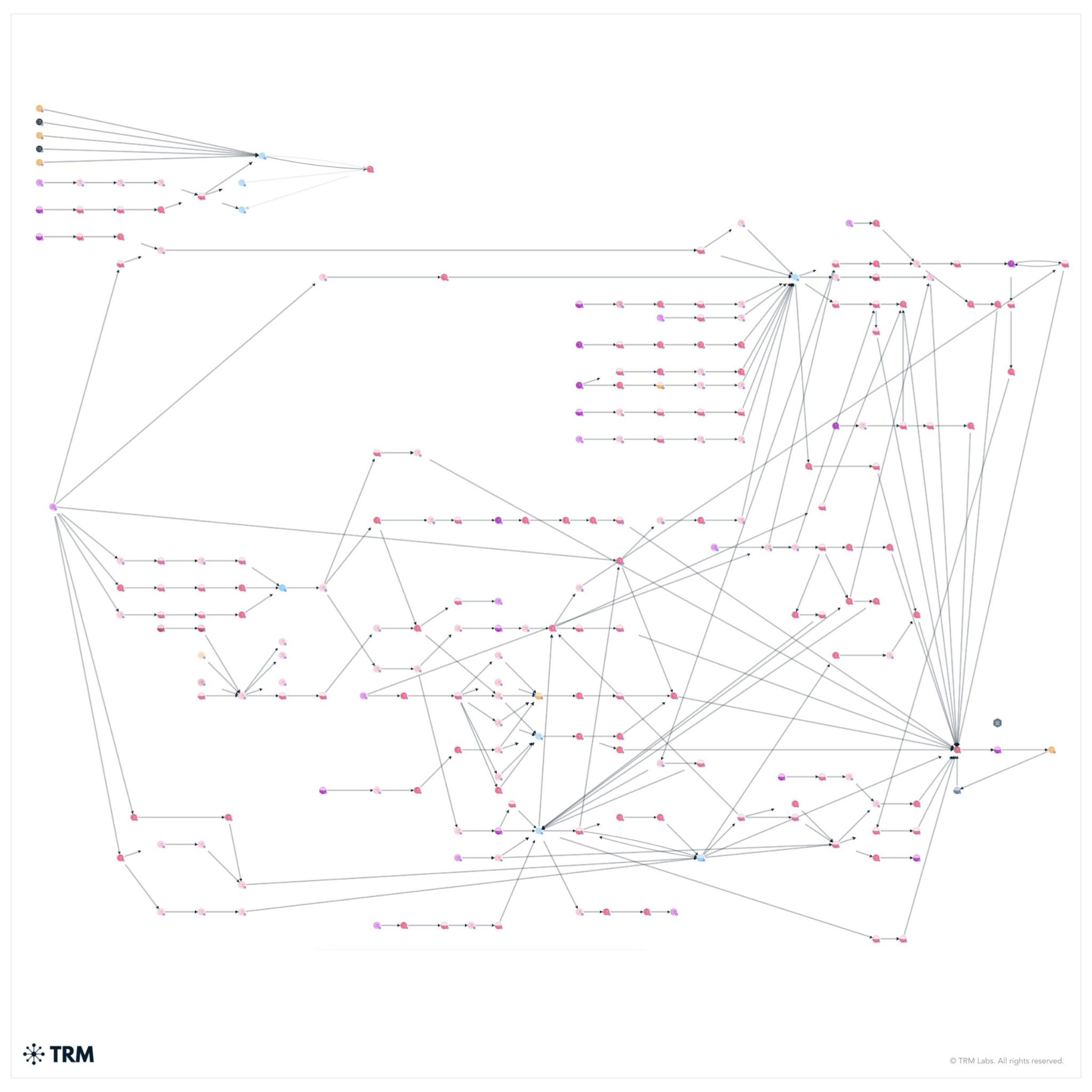
The forfeited bitcoin—127,271 BTC—was stored in 25 unhosted wallets controlled by Chen and his top lieutenants. According to the complaint, Chen personally held the seed phrases for several wallets, which investigators later recovered. According to TRM analysis, the funds can be traced through on-chain analysis to a December 2020 movement long referred to as the Lubian Hack, though the complaint suggests that it may not have been an external breach at all but rather an insider theft within the Prince Group’s own laundering network.
After years of dormancy, the same wallets showed renewed activity in June and July 2024, correlating with the DOJ’s seizure operations. The complaint confirms that these funds are now in US government custody, representing the single largest crypto asset recovery in history. According to TRM, the majority of funds from the blockchain addresses listed in the indictment against Chen Zhi consolidate into a single cluster holding approximately USD 14.13 billion in Bitcoin, with remaining funds routed through intermediary hops to other unhosted wallets and global exchanges before reconnecting to the same cluster. The Bitcoin—127,271 coins worth roughly USD 15 billion—has remained largely dormant since December 2020.
The financial section of the complaint provides remarkable detail about how the enterprise laundered billions through crypto and shell structures. Between 2021 and 2022, the so-called Brooklyn Network moved more than USD 18 million from US victims back to Prince Group accounts in Cambodia. Chen oversaw professional “money houses” that collected scam proceeds in bitcoin and stablecoins (USDT, USDC), converted them into fiat, and then repurchased clean crypto to recycle through front companies and gambling or mining ventures. He personally discussed “BTC washing” operations and coordinated with underground exchanges. The DOJ traced much of the group’s illicit profits to these 25 unhosted wallets—the core of the record-breaking forfeiture.
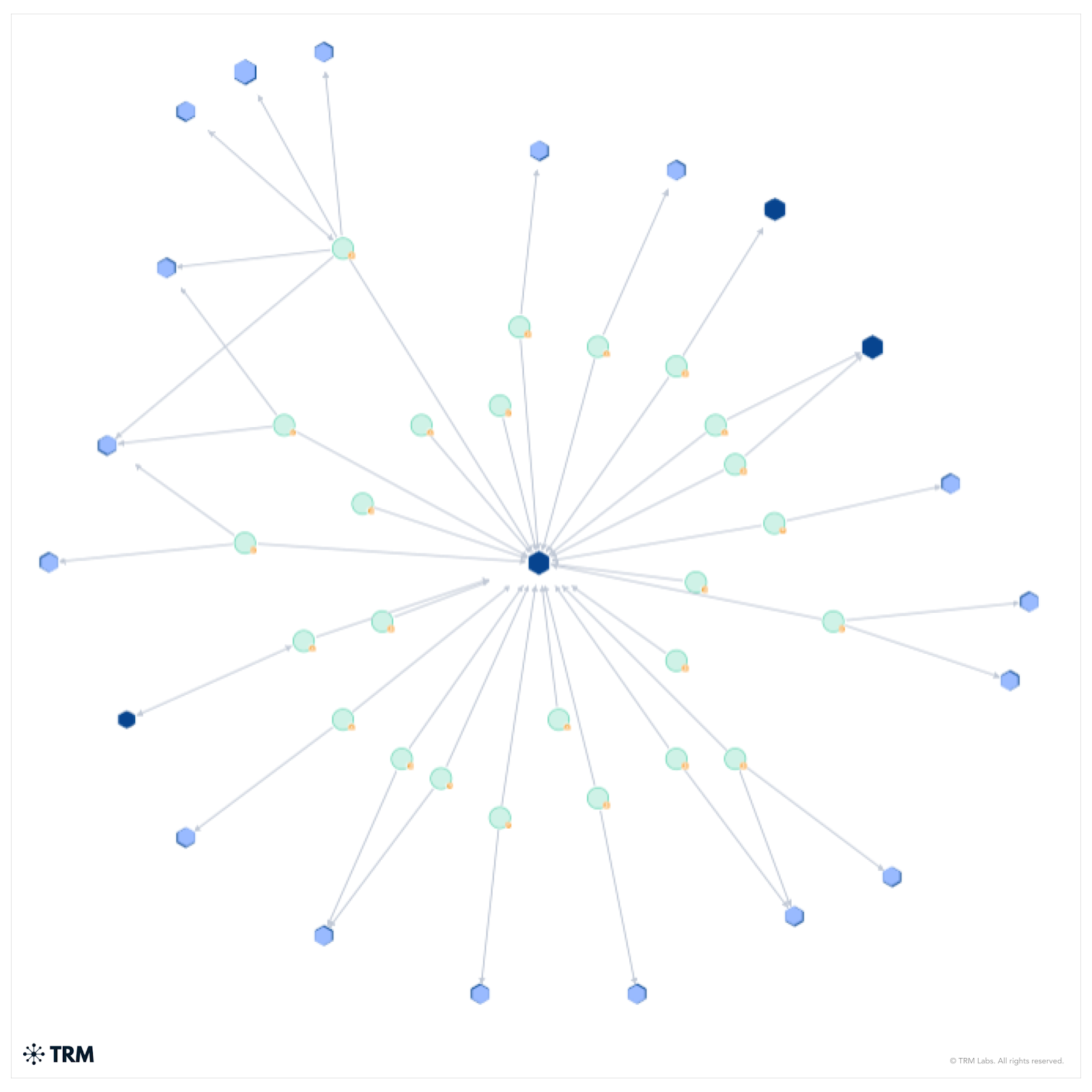
Corruption as Business Model
The unsealed government documents expose a system of organized corruption that allowed Prince Group to operate openly under the protection of senior Chinese officials. According to the complaint, Chen Zhi and his co-conspirators used political influence to shield their scam compounds from law enforcement scrutiny, including direct coordination with officials from China’s Ministry of Public Security (MPS) and Ministry of State Security (MSS). Investigators allege that these officials provided warnings of impending raids and offered “protection” in exchange for money and favors. The complaint recounts communications in which Prince executives bragged about having government contacts who could “get associates off the hook,” underscoring how state power was weaponized to safeguard a criminal enterprise that trafficked and exploited thousands of workers.
Ledgers recovered by investigators reveal the depth and precision of this bribery network. In 2019, one of Chen’s lieutenants purchased a yacht worth more than USD 3 million for a senior government official, while Chen himself later bought luxury watches valued in the millions for another official who used his influence to secure Chen a diplomatic passport. That passport—issued in 2020—enabled Chen to travel freely, including a trip to the United States in April 2023, even as US agencies were investigating the forced-labor and fraud operations he directed. These transactions were not incidental gestures but deliberate investments in political protection—operational expenses that ensured Prince Group’s scam compounds could continue functioning “in the light of day,” as the DOJ complaint describes.
The complaint also highlights internal communications describing “risk control” teams dedicated to managing relations with corrupt officials. In one exchange, an MPS contact offered to free detained Prince employees in exchange for a favor involving his son; in another, a Prince executive instructed Chinese police to “rob places first and then protect them,” turning state law enforcement into an extension of the enterprise’s protection racket.
This scheme illustrates how high-level corruption, fortified by geopolitical barriers, allows figures like Chen to remain at large despite years of criminal activity. By embedding their operations in jurisdictions unwilling or unable to cooperate with US authorities, the Prince Group leveraged state complicity to build a criminal empire that blurred the line between business and government. The coordinated US response—combining indictments, sanctions, and a record-setting USD 15 billion forfeiture—marks a significant evolution in confronting such networks. It demonstrates how whole-of-government and multilateral action can bypass compromised systems and strike at the financial architecture that sustains transnational crime and state-enabled exploitation.
Violence, Control, and the Machinery of Fear
Where bribes failed, according to court documents, violence filled the gap. Internal communications, laid out in the government pleadings, describe Chen approving physical punishments of subordinates suspected of disloyalty or theft, cautioning only that they should not be “beaten to death.” In one episode, after a Prince financial officer fled with company funds, senior leaders declared that “both the mafia and government are ready to be mobilized,” highlighting the organization’s symbiotic relationship with state-linked enforcers.
The complaint paints a picture of an enterprise where fraud, corruption, and coercion were inseparable. It thrived in the gray zone between government and organized crime—protected by influence, financed by crypto, and powered by human suffering.
Breaking the Protection
The significance of this case lies not only in the numbers but in the precedent it sets. By combining indictments, sanctions, and the largest crypto forfeiture in US history, the US, UK, and global partners, effectively bypassed the compromised systems that had allowed Prince Group to operate with impunity for nearly a decade. The assets once protected by corrupt officials and laundered on-chain are now in federal custody.
The Prince investigation lays bare how corruption at the highest levels of government, particularly within Chinese state security organs, enables transnational fraud networks to thrive. It also shows how strategic financial enforcement—targeting the money, not just the actors—can dismantle criminal ecosystems that have long operated beyond the reach of traditional law enforcement. This is more than a record-breaking forfeiture. It is a case study in how digital assets, state corruption, and forced labor intersect to form a new class of transnational threat—and how, when traced and understood, those same digital trails can bring even the most protected networks to justice.
TRM Labs
At TRM Labs, we work alongside global law enforcement agencies, regulators, and private-sector partners to track, trace, and disrupt precisely these kinds of transnational criminal networks. Through platforms like the Beacon Network—which enables real-time intelligence sharing across agencies—and community initiatives such as Chainabuse, TRM provides the data and analytics that help investigators connect digital evidence to real-world actors. Our teams collaborate with groups like Operation Shamrock and multi-agency task forces across the world, equipping investigators with tools to uncover illicit flows, dismantle organized crime infrastructure, and protect victims. The Prince case underscores why this kind of cross-border cooperation is essential—and how the right partnerships and technology can make it possible to follow the money anywhere it moves.






















