Unmasking Embargo Ransomware: A Deep Dive Into the Group’s TTPs and BlackCat Links

Since emerging around April 2024, ransomware-as-a-service (RaaS) group Embargo has established itself as a significant threat in the cybercrime landscape. TRM Labs has identified approximately USD 34.2 million in incoming transaction volume likely associated with the group, with most victims located in the United States (US) in the healthcare, business services, and manufacturing sectors. Notable victims include American Associated Pharmacies, Memorial Hospital and Manor in Georgia, and Weiser Memorial Hospital in Idaho, with ransom demands reaching USD 1.3 million.
This blog post explores the background, operational tactics, and notable insights surrounding this relatively new, yet sophisticated, ransomware group.
Key takeaways
- TRM assesses that Embargo may be a rebranded or successor operation to BlackCat (ALPHV) based on multiple technical and behavioral similarities — including using the Rust programming language, a similarly designed data leak site, and on-chain overlaps via shared wallet infrastructure
- Embargo launders ransom proceeds through intermediary wallets, high-risk exchanges, and sanctioned platforms such as Cryptex.net. Approximately USD 18.8 million remains dormant in unattributed wallets — a pattern that likely reflects deliberate evasion tactics
- Embargo’s technical sophistication suggests that it may be adopting artificial intelligence (AI) and machine learning (ML) to scale attacks, craft more convincing phishing lures, adapt malware, and accelerate operations
Crypto’s role in ransomware
Cryptocurrency remains central to ransomware groups, offering them a way to demand and receive payments anonymously and execute cross-border transactions. Bitcoin is the most commonly used cryptocurrency by ransomware operators; however, some groups prefer Monero due to its privacy features. Although law enforcement efforts to trace ransomware payments have intensified, groups are continuing to adapt and evolve their methods to evade detection.
Who is Embargo?
Since emerging, Embargo has gained attention for its technical sophistication and targeted ransomware campaigns. Operating under a RaaS model, the group provides affiliates with the tools to conduct attacks in exchange for a share of the ransom proceeds. However, Embargo retains control over core operations — including infrastructure and payment negotiations. This model enables threat actors to rapidly scale their operations and target a broad range of sectors and geographies.
Technical sophistication, subdued branding
Although not as prolific as groups like LockBit, Akira, or Cl0p, TRM assesses that Embargo is likely well resourced and technically capable — potentially drawing on the expertise or codebases of previous threat actors. Embargo deploys highly advanced and aggressive ransomware. However, it avoids the overt branding and high-visibility tactics of more prominent ransomware groups, such as triple extortion and victim harassment. This operational restraint has likely helped Embargo evade law enforcement detection and reduced media attention.
Financial and ideological motivations continue to converge
While Embargo’s operations are clearly financially motivated, several incidents have featured politically charged messages and ideological references — leading some analysts to assess that the group may be state-aligned or state-linked. This potential overlap complicates attribution and reflects a broader trend of financially motivated actors engaging in politically themed campaigns. Furthermore, nation-state actors almost certainly leverage cybercriminal groups as proxies to advance strategic or financial objectives while maintaining plausible deniability.
Targeting patterns
The group primarily targets organizations in the healthcare, business services, and manufacturing sectors likely due to their high up-time requirements and sensitivity to operational disruption. Targeting healthcare organizations, in particular, reflects a broader trend of threat actors seeking to maximize leverage by disrupting critical services. In healthcare, this can directly impact patient care, with potentially life-threatening consequences.
Geographically, Embargo has targeted organizations in Europe and Asia, but disproportionately focuses on the US — likely due to the perceived ability of US-based organizations to meet higher ransom demands.
What are the group’s initial access vectors and extortion tactics?
Embargo employs a range of advanced off-chain tactics, techniques and procedures (TTPs), demonstrating a clear focus on defense evasion and maximizing impact. The group typically gains initial access by exploiting unpatched software vulnerabilities or through social engineering — including phishing emails and drive-by downloads delivered via malicious websites.
Once inside a network, Embargo uses a two-part toolkit to disable security tools and remove recovery options before encrypting files. It then directs victims to communicate through Embargo-controlled infrastructure — a tactic that allows the group to retain control over negotiations and reduce exposure.
To increase leverage, Embargo maintains a data leak site where it lists victims that haven’t paid ransoms. In some cases, the group explicitly names individuals and publicly releases sensitive data to pressure victims into payment.
Embargo’s aggressive extortion tactics
Embargo also uses double extortion to pressure its victims — encrypting files while also exfiltrating sensitive data. The group then threatens to leak the data or sell it on the dark web if victims refuse to pay, compounding the financial damage with reputational and potential regulatory consequences. This tactic significantly increases the pressure on victims to settle quickly.
Is Embargo a rebranded BlackCat?
TRM assesses that Embargo may be a rebranded or evolved successor to BlackCat, which likely conducted an exit scam in 2024, based on the following off-chain similarities:
- Both groups use the Rust programming language. Rust offers threat actors several technical advantages, including cross-platform compatibility and enhanced obfuscation. This enables the development of malware capable of targeting both Windows and Linux environments.
- Embargo’s data leak site closely resembles BlackCat’s — not only in visual design but also in its underlying functionality and content structure
On-chain links to BlackCat
TRM has also identified notable on-chain overlap between Embargo and BlackCat ransomware, reinforcing the assessment that Embargo may be a rebranded version of the now-defunct group. Historical BlackCat-linked addresses have funneled funds to wallet clusters associated with Embargo victims. Furthermore, consistent with its RaaS model, Embargo affiliates have participated in campaigns for other ransomware groups — reflecting the opportunistic and fluid nature of affiliate involvement across multiple operations.

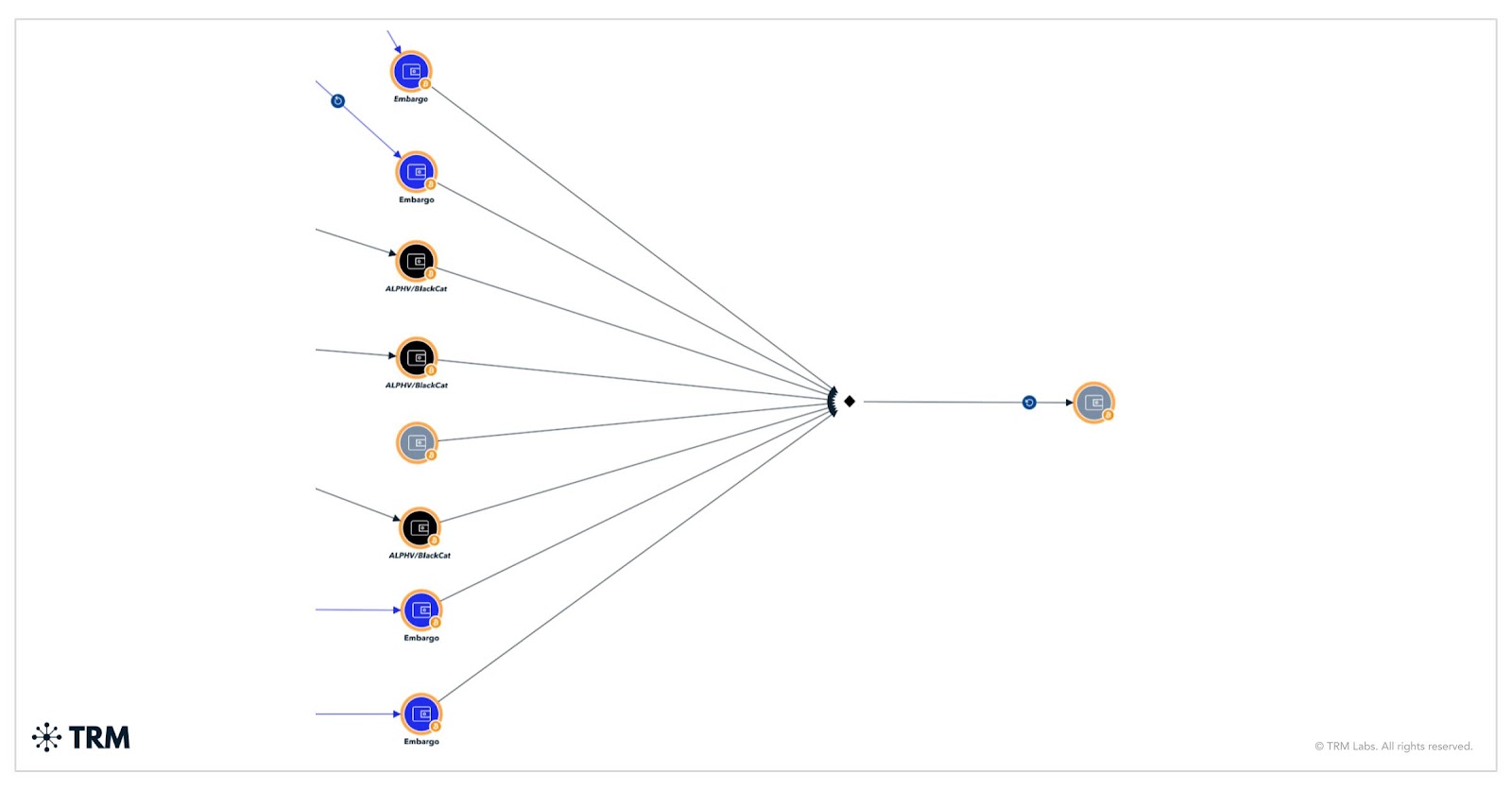
How does Embargo launder funds on-chain?
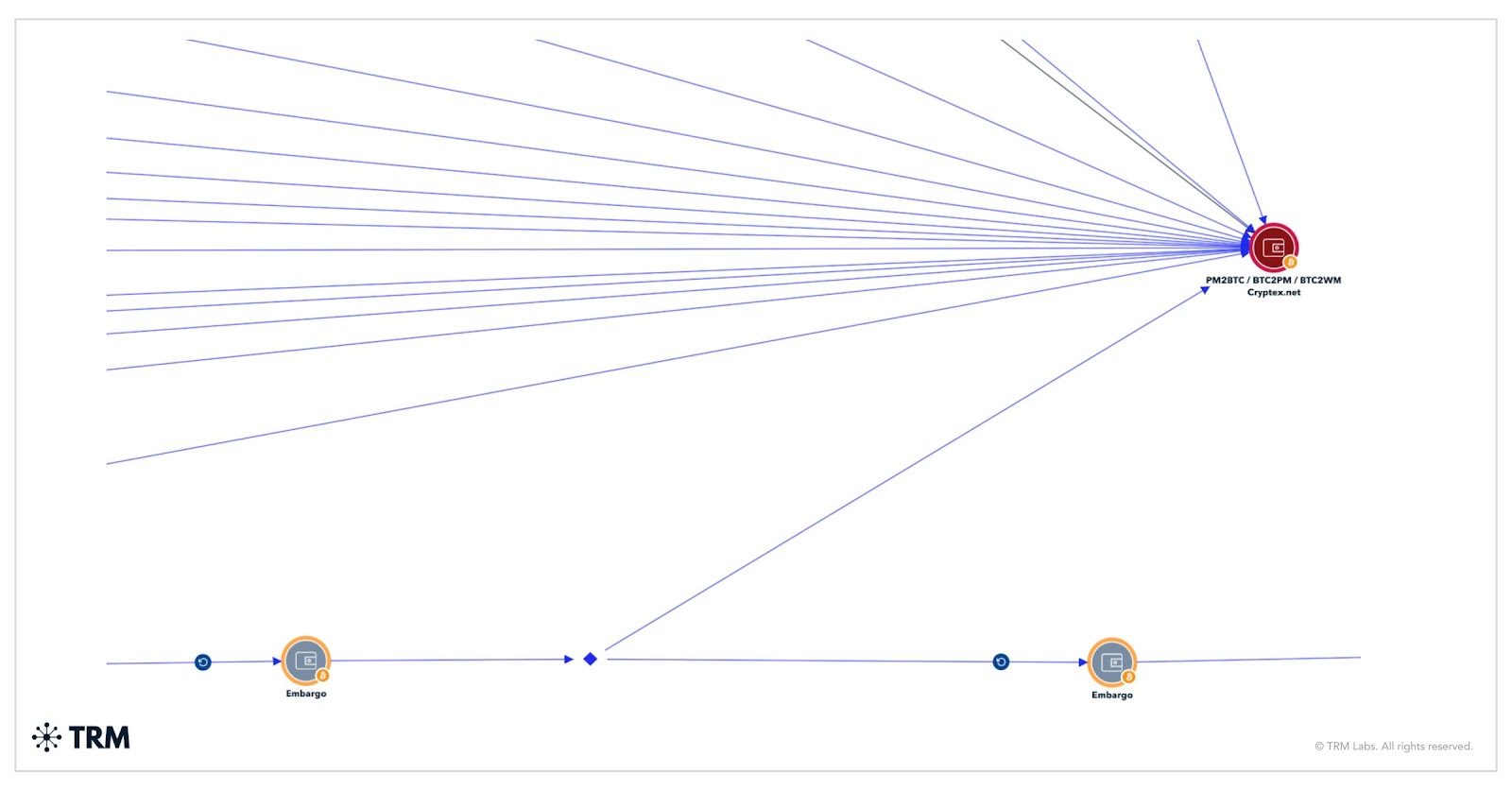
TRM has traced funds from Embargo victim payment addresses to a range of destinations, including global virtual asset service providers (VASPs), non-custodial and high-risk exchanges, mixing services, peer-to-peer marketplaces, and the now-sanctioned platform Cryptex.net.
Throughout the laundering process, TRM identified hundreds of deposits, totaling approximately USD 13.5 million, distributed across multiple VASPs. Furthermore, between May and August 2024, TRM observed approximately 17 deposits totaling more than USD 1 million routed through Cryptex.net.
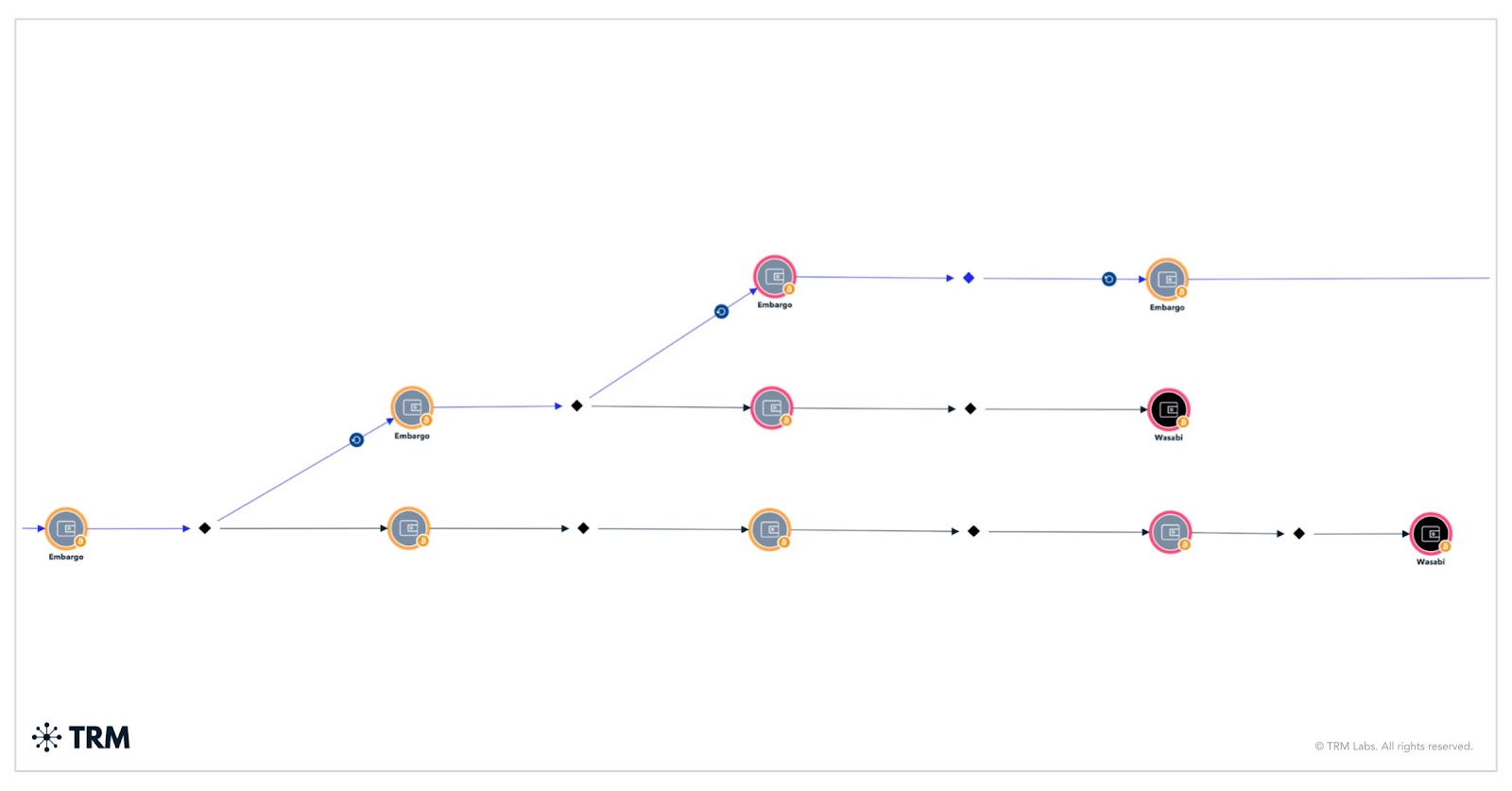
Intermediary wallets
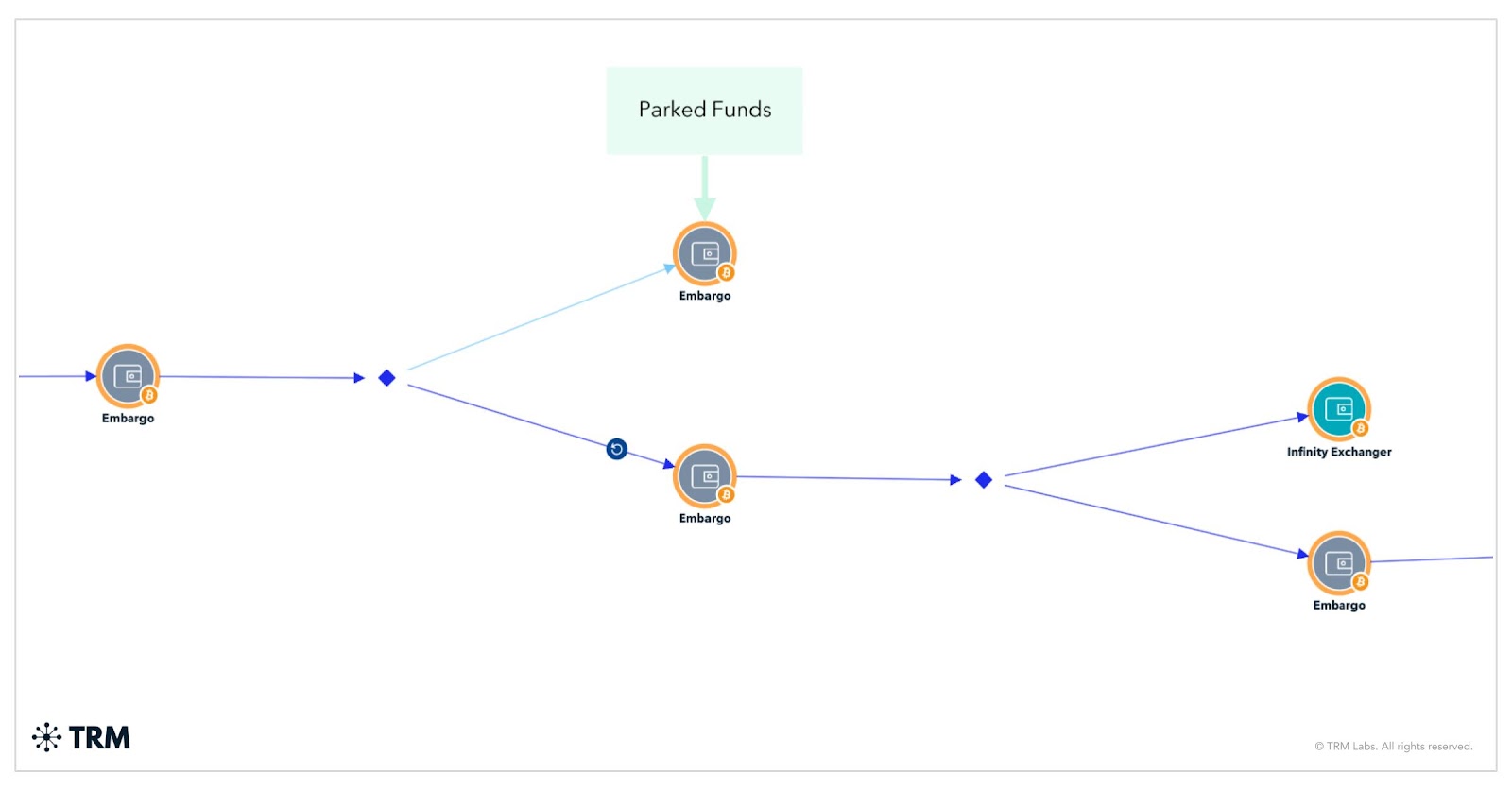
Although TRM identified two deposits into the Wasabi mixer, Embargo doesn’t rely heavily on mixers or cross-chain bridges to obfuscate its activity. Instead, the group typically launders funds through intermediary wallets — often layering transactions across several addresses — before ultimately depositing them directly into VASPs.
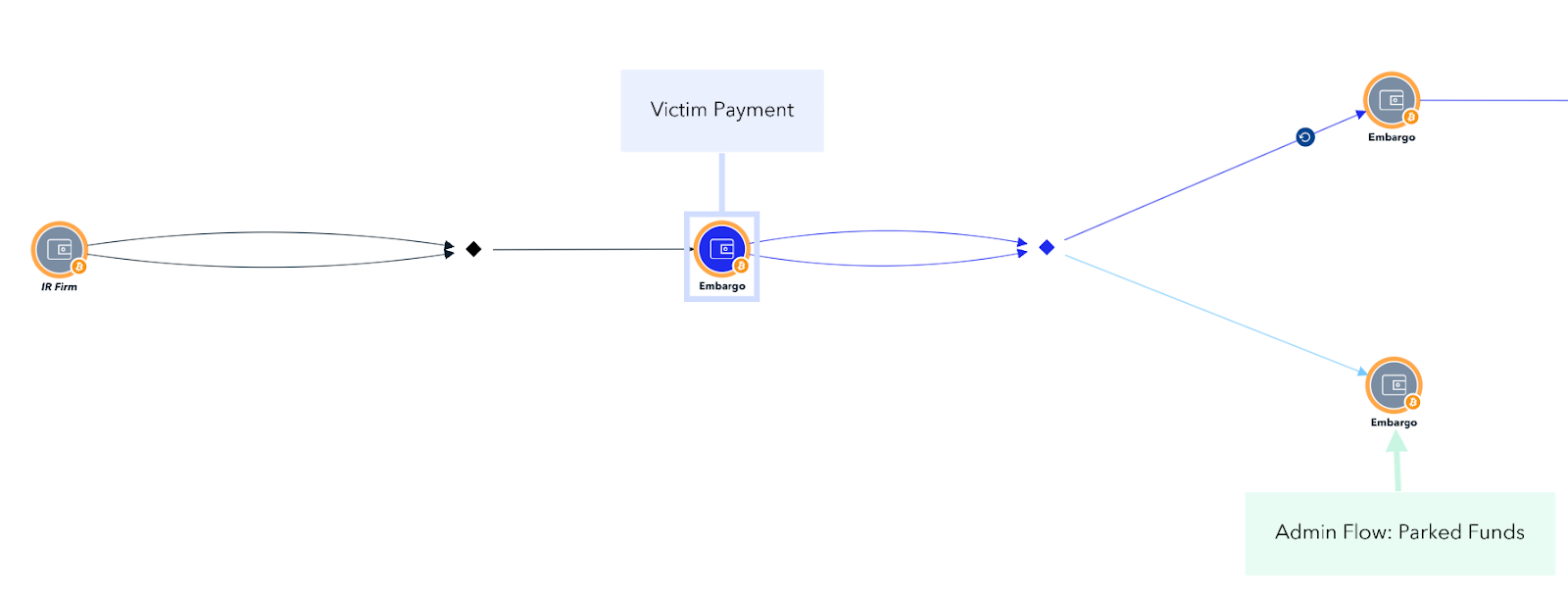
Parking funds
TRM also observed instances where funds remained idle following the initial split — including one flow likely associated with administrative infrastructure and another linked to an affiliate. Additional assets were parked at various stages of the laundering process. In total, approximately USD 18.8 million in victim funds remain in unattributed addresses.
This is likely a deliberate tactic to evade detection, by disrupting behavioral tracing patterns, or delaying movement until external conditions are more favorable, such as media attention, network fees, or liquidity. Delays may also reflect operational factors, including the need for downstream laundering support, internal disputes among actors, or potential loss of access to wallets.
AI lowering the barrier to entry for RaaS groups
Due to Embargo’s technical sophistication — combined with the broader trend of RaaS groups incorporating AI into their TTPs — the group may be experimenting with or adopting AI-enabled tooling to enhance its operations.
As detailed in TRM’s recent blog post, in the past year, threat actors have increasingly adopted AI tools across the scam ecosystem. There has been a similar shift in the ransomware threat landscape, with RaaS groups increasingly leveraging AI and ML. Ransomware operators are using these tools to:
- Scale operations, automating key stages of an attack, from initial reconnaissance and vulnerability scanning to deploying malware that mutates its code to evade detection
- Enhance social engineering lures, enabling groups to craft more convincing phishing emails, and generate realistic deepfakes impersonating executives
- Generate and customize malware, automating script writing and payload creation
AI’s role in combatting ransomware threats
While AI is accelerating the scale and sophistication of ransomware attacks, it’s also becoming a critical tool in stopping them. Companies are using AI to detect signs of compromise — such as unusual access behavior and file encryption patterns.
Effectively countering ransomware threats also requires collaboration between the public and private sectors. Blockchain intelligence companies like TRM Labs support investigations by tracing ransom payments on-chain and identifying infrastructure used by ransomware groups.
Organizations, particularly those in commonly targeted sectors such as healthcare and financial services, can mitigate the ransomware threat in various ways, including regular patching, robust endpoint detection and response, and phishing detection training for employees. As threat actors’ tactics continue to evolve, these defensive measures — alongside regulatory developments and international collaboration — remain essential to preventing and disrupting their operations.
Conclusion
Embargo remains a dangerous and evolving threat in the ransomware ecosystem — outlined by its adoption of Rust, advanced defense evasion techniques, and use of double extortion. The group potentially being a rebrand or successor to BlackCat reinforces how ransomware groups are constantly evolving to avoid attribution, maintain continuity, and retain affiliate networks.
Understanding Embargo's TTPs is critical for organizations looking to strengthen their defenses and improve response readiness. As the threat landscape continues to shift — shaped by law enforcement actions, geopolitical dynamics, and technological developments — groups like Embargo highlight the ongoing need for timely threat intelligence, resilient cybersecurity controls, and proactive incident response planning.
{{horizontal-line}}
Frequently asked questions (FAQs)
What is Embargo ransomware, and how does it impact organizations in the US?
Embargo is a ransomware-as-a-service (RaaS) group that first appeared in 2024 and has since emerged as a sophisticated threat to organizations across the United States. The group primarily targets the healthcare, business services, and manufacturing sectors — all industries with critical up-time requirements and limited tolerance for operational disruption. Notable US-based victims include hospitals and pharmaceutical networks, with ransom demands reaching as high as USD 1.3 million. TRM Labs has traced USD 34.2 million in crypto transactions likely tied to Embargo activity, underscoring the group’s growing financial footprint in the ransomware ecosystem.
Is Embargo ransomware connected to the BlackCat (ALPHV) group?
TRM assesses that Embargo may be a rebrand or successor to BlackCat (also known as ALPHV), based on both on-chain and off-chain similarities. Technical overlaps include the use of the Rust programming language, similar encryption toolkits, and the design of their data leak sites. Additionally, on-chain analysis has revealed shared wallet infrastructure between Embargo and historical BlackCat-linked addresses — suggesting continuity in operational tactics and affiliate participation. These patterns reflect how ransomware groups evolve to preserve affiliate networks and avoid attribution, especially in the face of law enforcement pressure.
How does Embargo ransomware move and launder ransom payments?
Embargo doesn’t rely heavily on mixers or cross-chain bridges to obscure transactions. Instead, the group typically launders ransom payments using a layered, multi-stage strategy that routes funds through intermediary wallets, high-risk exchanges, and, in some cases, sanctioned platforms such as Cryptex.net. TRM identified more than USD 13 million in deposits funneled to global virtual asset service providers (VASPs), while an additional USD 18.8 million remains idle in unattributed wallets — likely to disrupt detection efforts or delay movement until conditions are more favorable.
Why is Embargo ransomware focusing on healthcare and US-based targets
Embargo disproportionately targets organizations in the US likely due to the perception that US-based organizations are more likely to meet higher ransom demands. The group targets sectors with urgent recovery timelines — particularly healthcare — where service disruptions can lead to life-threatening consequences and increase pressure to pay. This strategy mirrors broader trends in the ransomware ecosystem, where threat actors seek maximum leverage by attacking critical infrastructure. The inclusion of politically charged messaging in some campaigns further complicates attribution, raising questions about possible state-linked motivations.
How is artificial intelligence (AI) shaping the tactics of ransomware groups like Embargo?
Technologies like AI and machine learning (ML) allow ransomware operators to automate key phases of an attack, including reconnaissance, phishing, malware generation, and negotiation processes. Embargo may be using AI to craft more convincing phishing lures or generate polymorphic code that adapts in real time to bypass security tools. As ransomware actors continue to scale their capabilities with AI, it is becoming increasingly important for organizations — particularly those in high-risk sectors — to invest in strong detection and response mechanisms.






















