US, Australia, and UK Sanction Russian Cybercrime Infrastructure Supporting Ransomware

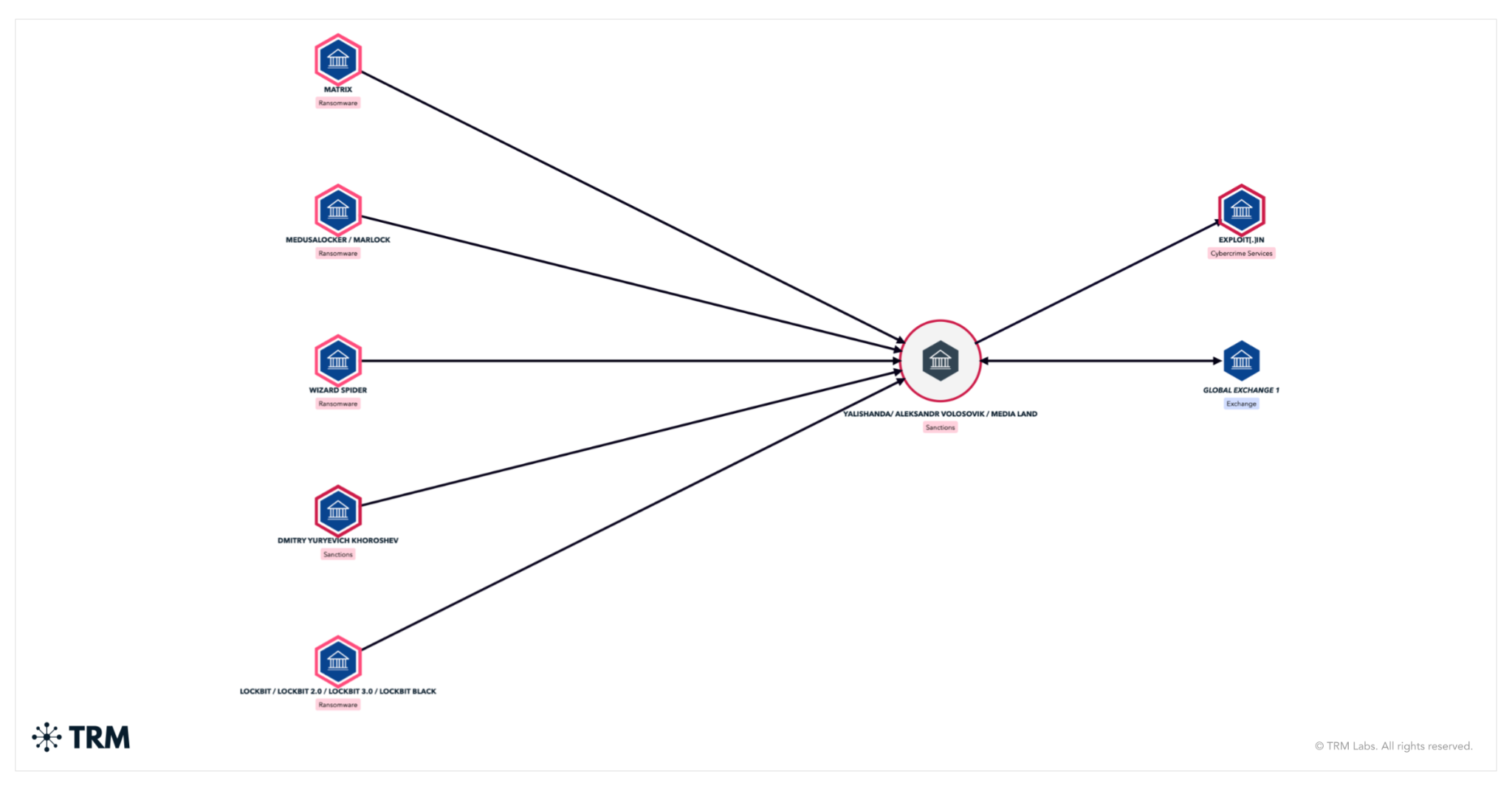
Today, the US Department of Treasury’s Office of Foreign Assets Control (OFAC), in coordination with Australia’s Department of Foreign Affairs and Trade and the United Kingdom’s Foreign, Commonwealth & Development Office, announced sanctions against Media Land, a Russia-based bulletproof hosting (BPH) service provider, for its role in supporting ransomware operations, as well as other forms of cybercrime. The designation also included multiple companies associated with, and associates of Media Land, as well as its director Aleksandr Volosovik. According to the designation, Volosovik frequently advertised Media Land’s business on cybercrime forums under the alias Yalishanda.
Today’s action also targeted Hypercore Ltd., identified by OFAC as a front company for Aeza Group — a bulletproof hosting (BPH) provider sanctioned by both the U.S. in July 2025 and the UK today. According to OFAC, following its July designation, Aeza Group attempted to evade sanctions through a rebranding effort designed to obscure its ownership and technical infrastructure. In connection with this effort, OFAC also designated two additional successor companies, along with Maksim Makarov, Aeza’s new director, and Ilya Zakirov, an associate linked to the group’s ongoing operations.
What is Bulletproof Hosting?
Bulletproof hosting (BPH) refers to a category of web hosting services that deliberately provide infrastructure designed to evade law enforcement detection and takedown efforts. Unlike legitimate hosting providers that respond to abuse reports or government requests, BPH operators advertise themselves as “tolerant” of illegal or unethical activity, shielding their clients from domain seizures, legal complaints, and cybersecurity monitoring.
These services thrive on resistance and resilience. When investigators flag malicious activity, bulletproof hosts often ignore takedown notices, quickly reassign IP addresses, or migrate their servers across borders to stay operational. Many operate from jurisdictions with weak or inconsistent cybercrime enforcement, making them difficult for international authorities to dismantle.
Anonymity is central to their business model. Most BPH providers accept cryptocurrency payments and require minimal — or no — customer verification, ensuring clients can remain hidden. This anonymity, coupled with rapid infrastructure relocation, enables cybercriminals to conduct illicit operations with near impunity.
The role of BPH in cybercrime ecosystems is significant. These services provide the digital foundation for ransomware command-and-control servers, phishing campaigns, malware distribution, and large-scale botnets. Ransomware groups depend on BPH to manage infections and extort victims. Fraud operators use it to host fake banking or identity-theft websites. Even darknet marketplaces — where illicit goods such as stolen data, weapons, and narcotics are traded — rely on bulletproof hosts to remain online and out of reach of law enforcement.
Media Land/Yalishanda/Volosovik
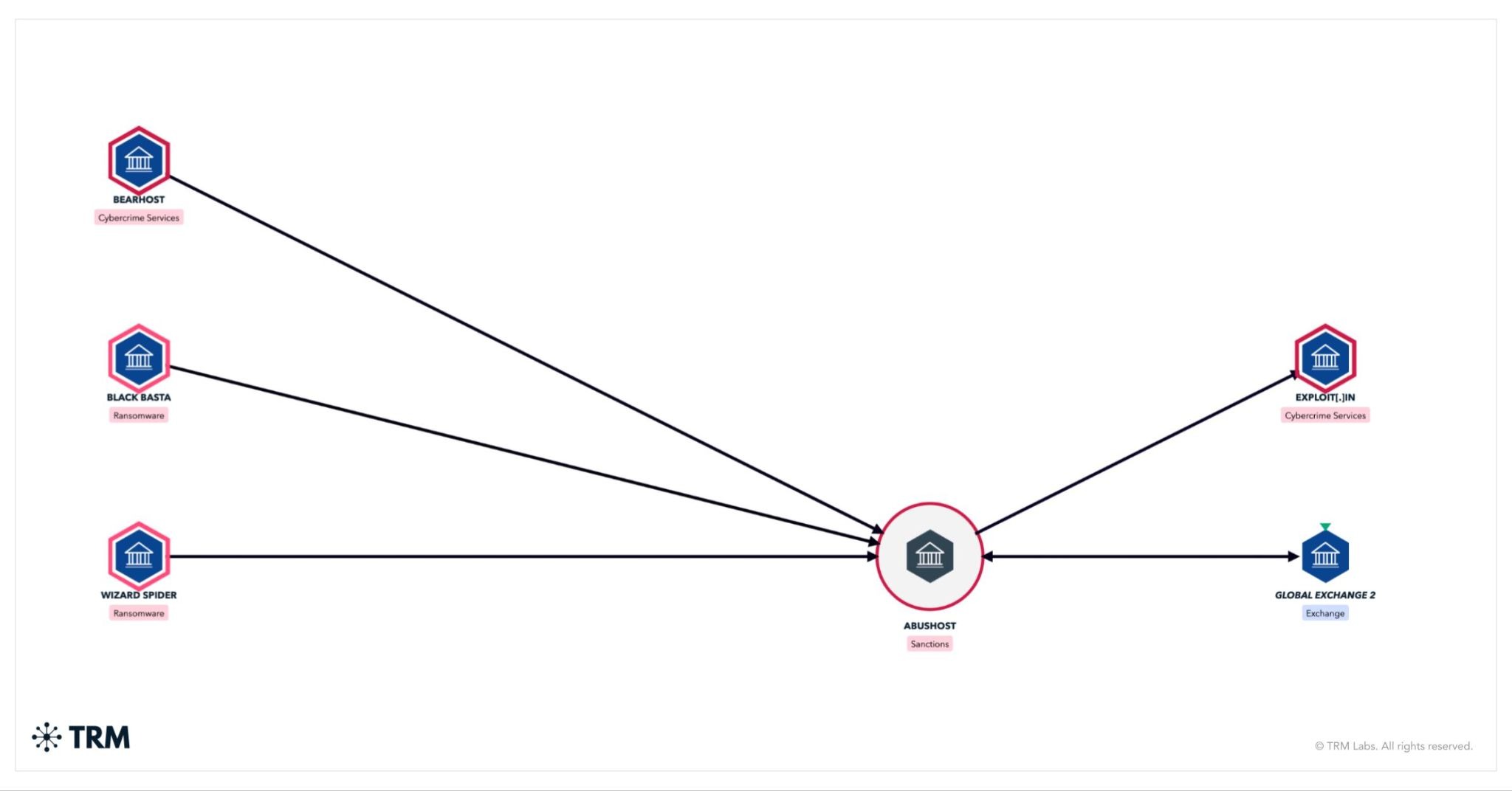
According to TRM, since at least 2015, Aleksandr Volosovik and his associates — most notably the actor known as “podzemniy1” — have openly marketed bulletproof hosting (BPH) services under the name Abushost across prominent cybercrime forums including Exploit[.]in and XSS[.]pro. Abushost provides cybercriminals with resilient infrastructure — IP addresses, servers, and network tools — designed to support ransomware deployment, data theft, and other forms of cyber-enabled crime.
TRM analysis of addresses linked to Yalishanda and Abushost shows more than USD 2 million in received volume, with direct and indirect interactions across some of the most prolific ransomware operations, including BlackSuit, Black Basta, LockBit, and MedusaLocker. The same networks reveal repeated fund flows to and from intermediary wallets and major global exchanges, illustrating how these infrastructure providers integrate into broader ransomware and cybercrime ecosystems.
Ongoing Coordinated international crackdown on cybercrime
Today’s designations highlight a growing trend in global enforcement: targeting not just the cybercriminals themselves, but the infrastructure that enables their operations. As threat actors continue to exploit resilient hosting services and opaque payment channels to expand their reach, actions like this seek to disrupt the ecosystem at its foundation, reducing the digital terrain available for abuse.
The cases of Yalishanda and Media Land demonstrate how infrastructure providers act as critical enablers of global cybercrime, supplying the backbone for ransomware, malware distribution, and data theft at scale. By focusing on these technical facilitators, regulators and law enforcement are shifting from reaction to prevention—using sanctions to make it harder, riskier, and more expensive for cybercriminals to operate.
Access our coverage of TRON, Solana and 23 other blockchains
Fill out the form to speak with our team about investigative professional services.






















