Monero in 2025: Persistent Use and Emerging Network-Layer Insights

Key takeaways
- Monero transaction activity has remained stable and resilient, with usage holding steady above pre-2022 levels despite widespread delistings from major exchanges and growing enforcement pressure on transparent assets.
- Ransomware actors continue to express preference for Monero, yet the majority of real-world ransom payments still occur in bitcoin — highlighting the tension between privacy and usability in illicit finance.
- Monero’s share of darknet market adoption is rising, with nearly half of newly launched markets in 2025 supporting XMR exclusively — a sharp increase from prior years and a signal of shifting behaviors in high-risk environments.
- New research shows 14–15% of Monero network peers behave non-standardly, revealing persistent deviations in relay behavior, message timing, and infrastructure concentration that may influence privacy assumptions.
- Monero’s on-chain privacy remains intact, but real-world network dynamics matter, as peer-to-peer behavior can introduce structural visibility that affects theoretical anonymity models used in investigations.
{{horizontal-line}}
Monero occupies a distinct position in the illicit crypto ecosystem. As activity on public blockchains has become increasingly traceable and US dollar-backed stablecoins have grown into the dominant rails for global payments, most digital asset activity is now far more visible to investigators than it once was. Stablecoins, in particular, are increasingly subject to issuer controls and compliance measures, even when circulating widely in the open ecosystem.
Against that backdrop, Monero remains a persistent challenge due to its privacy-preserving design and the way it is used in practice. Recent market observations and academic research help clarify where Monero’s privacy features remain effective and where real world usage patterns may introduce new investigative considerations.
General adaptation and growing use of Monero
While monthly activity has fluctuated, sometimes sharply in response to network events or market dynamics, the overall trend shows that Monero usage has grown materially since 2020 and remained resilient through multiple market cycles.
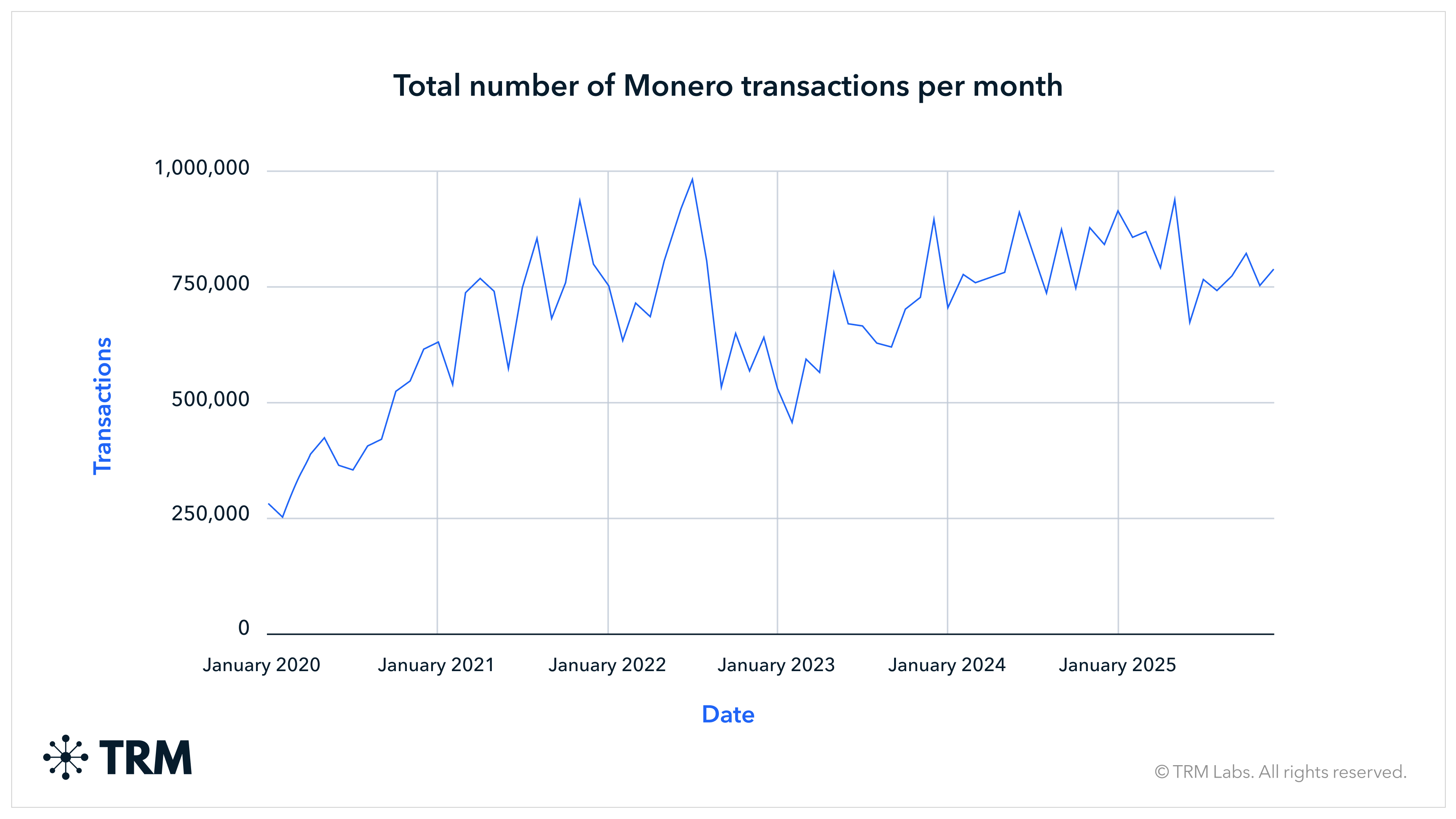
Notably, transaction volumes in 2024 and 2025 were significantly higher than in the early 2020–2021 period, reflecting Monero’s continued relevance even as enforcement capabilities against more transparent assets have improved. Monero’s transaction activity has stabilized at a higher baseline, suggesting sustained demand and regular use rather than episodic or speculative spikes.
This persistence is particularly notable given Monero’s substantial de-risking from major centralized exchanges. Over the past several years, many of the world’s largest trading platforms have delisted or restricted Monero due to traceability and regulatory concerns, including Binance, Coinbase, Kraken, OKX, Huobi, and Bitstamp. Some reports suggest there were 73 exchanges delisting Monero in 2025 alone. As a result, Monero is now supported by a far smaller set of exchanges than Bitcoin or leading US dollar-backed stablecoins, with liquidity increasingly concentrated on offshore or lower-compliance venues.
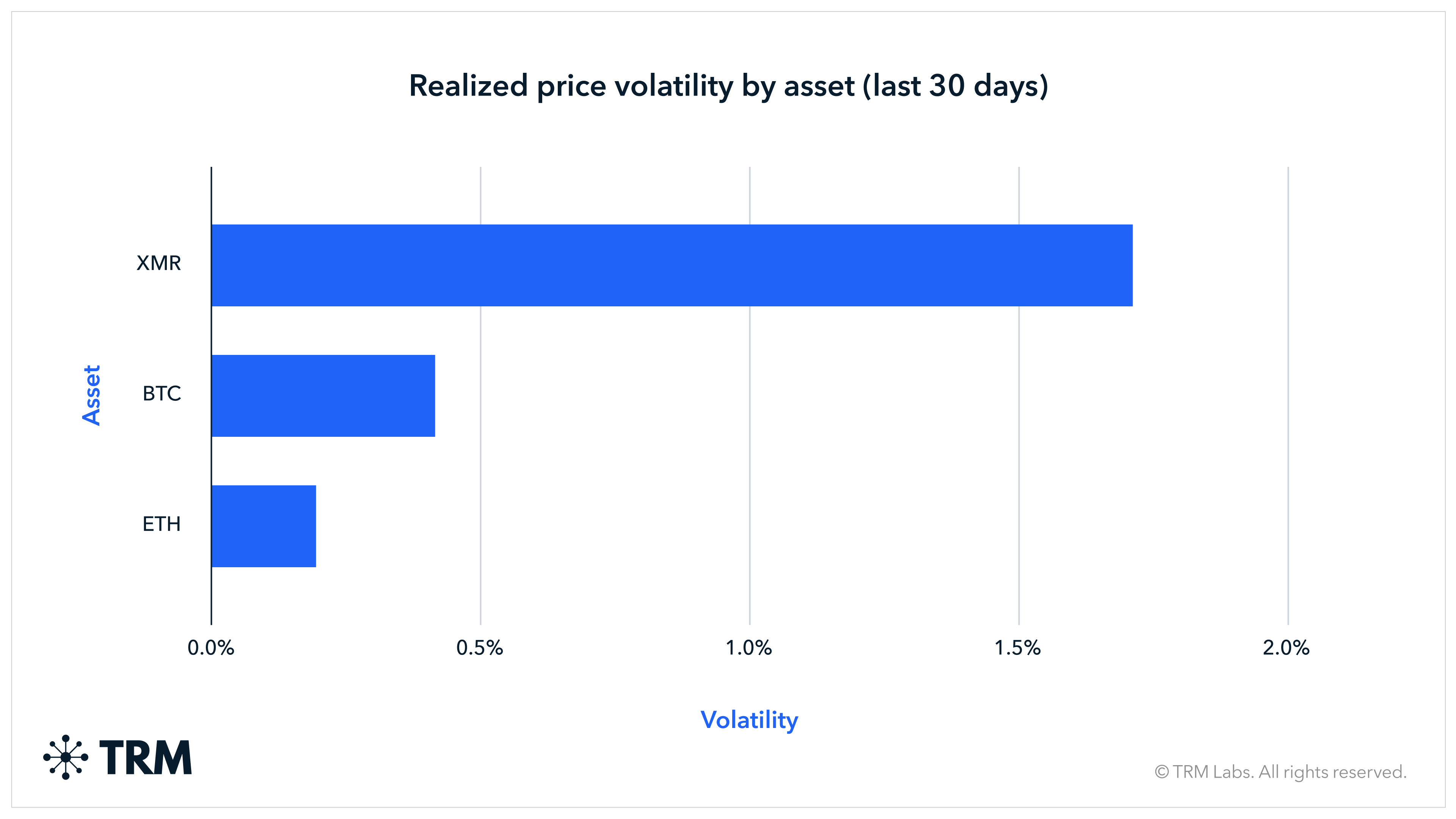
This liquidity constraint helps explain the gap between criminal preference and real-world payment behavior. While ransomware actors frequently request Monero and may even offer discounts to receive it, the overwhelming majority of ransom payments are still made in bitcoin. Bitcoin remains far easier to acquire, move, and convert at scale, even as it is more traceable — underscoring that usability and liquidity often outweigh privacy in practice. That tradeoff is visible in market behavior: over the past 30 days, Monero has exhibited materially higher price volatility than bitcoin and ETH — with realized volatility roughly two and a half times greater — reflecting thinner liquidity and a more fragmented market structure rather than isolated price shocks.
Despite this reduced access to mainstream exchange infrastructure, Monero’s on-chain usage has not meaningfully contracted. This suggests that demand is not primarily driven by casual retail trading, but by users who deliberately seek out Monero’s privacy features and are willing to accept higher friction, fewer on-ramps, and reduced liquidity to transact in it.
Monero’s adoption in darknet marketplaces (DNMs) has also grown. Recent data shows a continued structural shift toward XMR-only markets, particularly in environments facing sustained enforcement pressure. In 2025, nearly half (48%) of newly launched darknet markets supported only Monero — a notable increase compared to earlier years. This trend is especially pronounced in Western-facing markets, where privacy coins appear to be a direct response to improved tracing capabilities on Bitcoin and stablecoins.
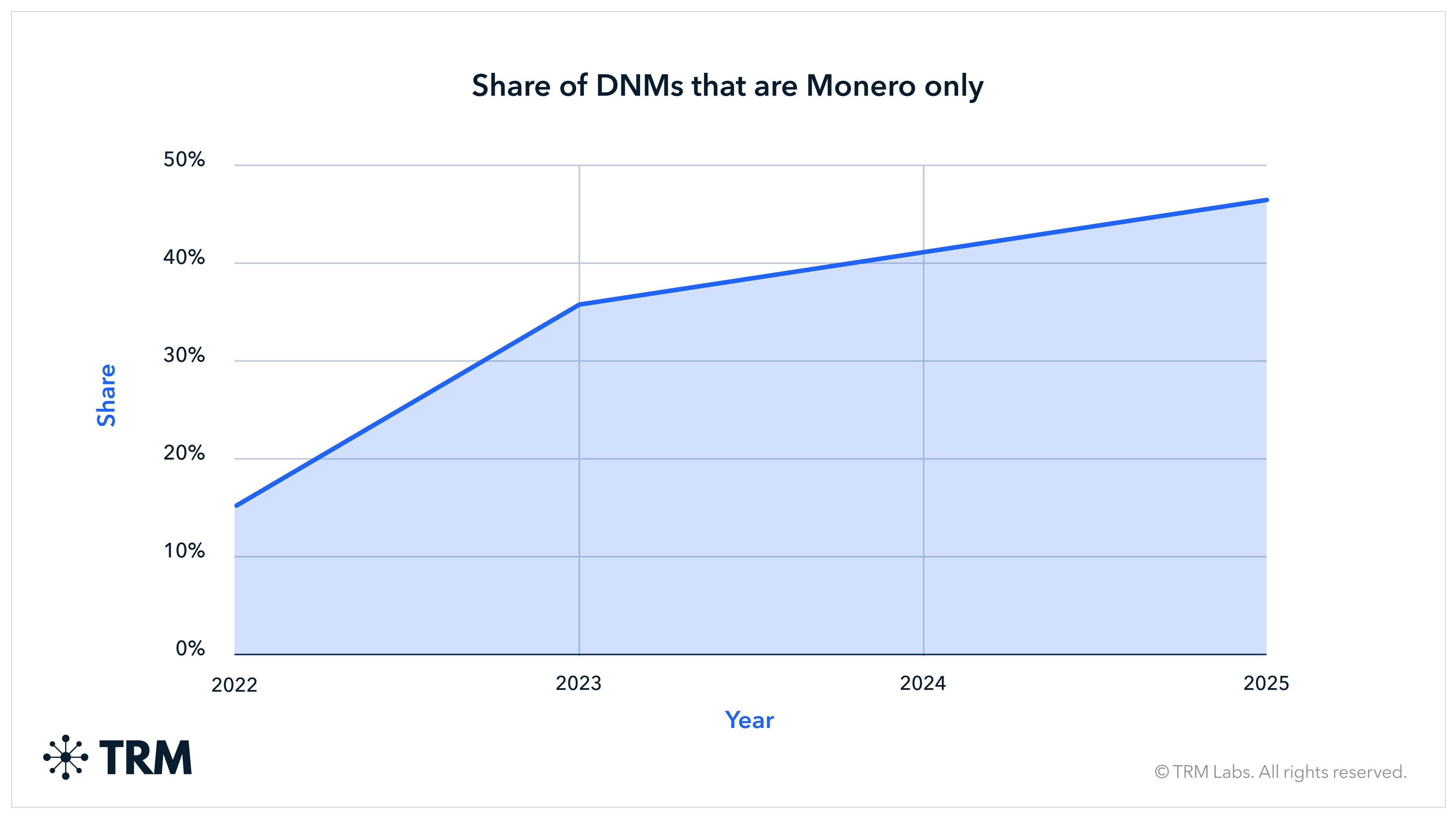
While Monero represents a smaller share of overall cryptocurrency transaction activity compared to major transparent networks, its transaction volumes remain substantial and persistent given its specialized role. The combination of steady on-chain usage and a growing share of XMR-only darknet markets suggests that Monero continues to fill a specific demand for privacy that has not diminished as traceability across other assets has improved.
New research: Non-standard behavior in monero’s P2P network
While Monero’s continued adoption underscores the enduring demand for privacy-preserving assets, it also raises a natural follow-on question: how that privacy functions in real-world conditions.
Much of the discussion around Monero’s resilience has focused on its on-chain cryptography and market role, but privacy in practice is shaped not only by protocol design, but also by how the network is operated and used day to day. As investigative pressure has pushed activity toward assets like Monero, understanding the behavior of the network layer itself becomes increasingly relevant.
Recent empirical research into Monero’s peer-to-peer network offers new insight into how real-world network dynamics may influence assumptions about privacy, complementing rather than contradicting the asset’s well-established on-chain protections. TRM Labs supports monitoring and analysis across a large number of blockchains to help law enforcement and government partners understand and investigate real-world misuse. In the course of network traffic analysis, we observed unexpected behavior in the Monero peer-to-peer (P2P) network that didn’t align with standard client implementations or protocol expectations.
To better understand these anomalies, we collaborated with external academic researchers to systematically analyze the behavior of peers on the Monero network. The findings (available as a pre-print on arXiv) provide an empirical look at deviations from expected P2P behavior and what those deviations may imply.
Key takeaways
- Anomalous peers are measurable: Around 14–15% of reachable peers in the observed Monero network exhibited non-standard behavior relative to protocol expectations.
- Non-standard doesn’t necessarily mean malicious: Deviations included protocol irregularities and unusual timing or handshake patterns — behavioral departures, not automatically confirmed attacks.
- Concentrated infrastructure patterns: Analysis suggests some operators control a disproportionate share of observed peers, potentially aiming to extract information.
- Implications for privacy assumptions: Although Monero’s on-chain cryptography remains unchanged, network behavior can impact theoretical anonymity properties if observers can see message propagation.
Interpretation of the findings
The observed non-standard behavior spans several dimensions of the Monero P2P protocol, including handshake behavior, message timing, peer list composition, and infrastructure distribution. Individually, some of these deviations could plausibly arise from misconfiguration, outdated clients, or alternative implementations.
What makes the observations notable is their persistence, scale, and concentration. A non-trivial fraction of reachable peers repeatedly deviated from baseline behavior across multiple observation points and time periods, suggesting systematic rather than incidental causes.
Importantly, these findings describe how peers behave, not why they behave that way. The analysis does not attempt to assign intent, identify operators, or attribute activity to specific entities.
Concentration and network effects
One recurring pattern in the data is infrastructure concentration. A relatively small number of network locations and hosting environments accounted for a disproportionately large share of non-standard peers.
In peer-to-peer systems, such concentration can matter even when cryptographic protections remain intact. Nodes that are more frequently connected to, or more widely advertised through peer lists, can gain structural visibility into message propagation and network topology. Over time, this visibility may reduce uncertainty about transaction origination or relay paths.
These effects arise from network dynamics rather than protocol violations, making them harder to detect or mitigate through traditional rule-based defenses.
Implications for privacy assumptions
Monero’s privacy guarantees are often evaluated at the on-chain layer. Those guarantees generally assume that the network layer behaves in a statistically uniform way, with peers operating independently and following standard relay patterns.
The presence of sustained non-standard behavior challenges that assumption. Deviations in timing, connection lifetimes, or peer list composition can introduce observable structure into transaction propagation, which may be relevant for inference under certain threat models.
This does not imply a failure of Monero’s cryptography. Rather, it highlights how real-world network behavior can diverge from idealized models used in privacy analysis.
{{horizontal-line}}
Frequently asked questions
1. What makes Monero different from other cryptocurrencies?
Monero is a privacy-preserving cryptocurrency that uses stealth addresses, ring signatures, and confidential transactions to obscure sender, recipient, and amount details on-chain. Unlike bitcoin or Ethereum, which offer publicly visible transaction data, Monero is designed to make tracing significantly more difficult.
2. Why is Monero still used in illicit activity?
Monero’s default privacy features appeal to actors seeking greater anonymity, particularly in environments where enforcement has made bitcoin and stablecoin flows more traceable. Despite friction, limited exchange access, and higher volatility, some users are willing to accept those tradeoffs for perceived privacy benefits.
3. Is Monero completely untraceable?
Not necessarily. While Monero’s on-chain cryptography is strong, recent research highlights how non-standard peer-to-peer network behavior — such as irregular timing, handshake patterns, or centralized node infrastructure — can introduce new vectors for inference, especially under certain investigative models.
4. Why do most ransomware payments still happen in Bitcoin?
Bitcoin remains easier to acquire, move, and convert — especially at scale — due to higher liquidity and broader exchange support. Even though Monero is often requested in ransom notes, bitcoin’s accessibility and operational ease continue to drive its dominance in actual payment behavior.
5. How is TRM able to support investigations involving Monero?
TRM helps law enforcement and compliance teams assess risk related to Monero by monitoring on-chain activity, off-chain behavior, and network-layer dynamics. While Monero is designed to resist tracing, behavioral and structural patterns — including exchange interactions and wallet clustering — can still support actionable insights.






















