Nine Emerging Groups Shaping the Ransomware Landscape

Artificial intelligence (AI) has lowered the barrier to entry for cybercriminals, allowing ransomware threat actors to automate coding, generate polymorphic malware — which alters its code with each infection to evade detection — and create more convincing social engineering lures. As a result, new groups are emerging rapidly, and established groups are scaling their operations.
In this post, we take a closer look at nine emerging ransomware groups and examine how their off-chain and on-chain tactics are reshaping the ecosystem.
Key takeaways
- AI is enabling faster, more scalable ransomware operations — from generating polymorphic malware to automating social engineering
- Some groups are moving away from encryption, instead relying on reputational damage, regulatory pressure, and data leaks to extort victims
- The line between state-linked and financially motivated groups is becoming increasingly blurred, with state-sponsored groups collaborating with financially linked actors to pool resources and maximize their campaigns
- On-chain laundering is evolving, with groups adopting cross-chain swaps and high-risk exchanges — but many still follow identifiable and potentially recoverable patterns
- Ransomware campaigns are becoming more coercive and opportunistic — favoring speed, psychological pressure, and flexible affiliate models over advanced tooling
{{horizontal-line}}
Why do ransomware groups use crypto?
Ransomware groups typically leverage crypto to demand and receive cross-border payments anonymously. Bitcoin is the most common cryptocurrency requested by ransomware operators, though Monero is also used by some groups due to its privacy features. Both former and active ransomware groups — like BlackSuit, DragonForce, and Akira — convert proceeds from bitcoin into other cryptocurrencies like Ethereum, Tron, Binance Smart Chain, and Arbitrum throughout the laundering process.
Nine emerging groups and their TTPs
The following nine ransomware groups have emerged in the past 12 months, reflecting the expanding cybercrime landscape. Let’s examine their tactics, techniques, and procedures (TTPs) both off-chain and on-chain.
Groups with growing scale, operational maturity, and demonstrated victim impact
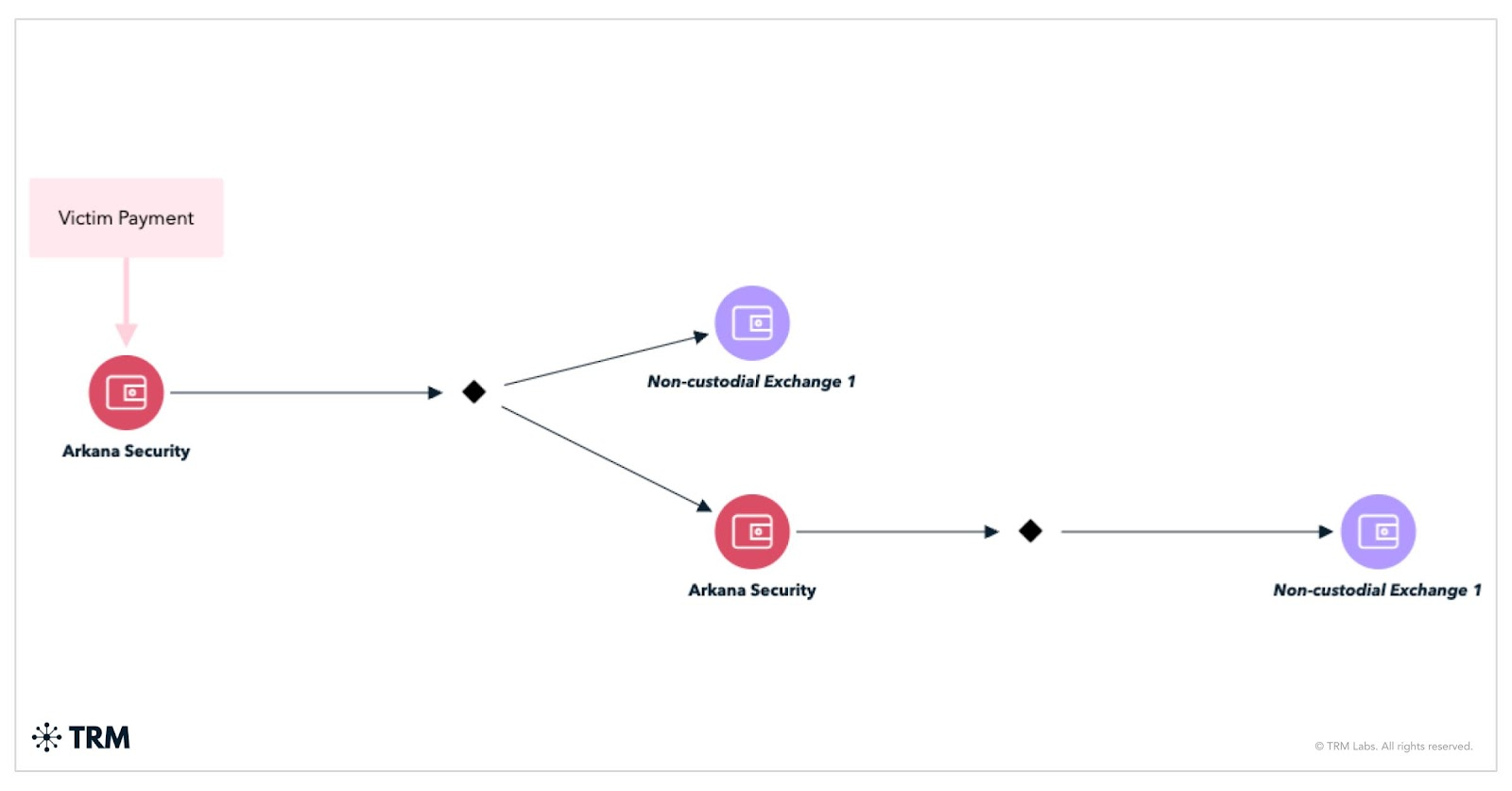
1. Arkana Security
Rose in profile after a major US ISP breach; blends encryption, doxxing, and leaks; funnels funds through a single non-custodial exchange
Arkana Security’s first reported operation — a high-profile attack on US cable provider WideOpenWest (WOW!) — quickly elevated its profile within the ransomware ecosystem. Despite only emerging in March 2025, Arkana’s operational sophistication suggests it is run by experienced actors. The tactics and language used by the group indicate its operators may be based in Russia or Eastern Europe, more broadly.
Off-chain TTPs
Arkana carries out attacks across the full ransomware lifecycle — from phishing and exploiting public-facing apps to stealing credentials, moving laterally through networks, and exfiltrating sensitive data. Its campaigns typically involve widespread encryption, data theft, and reputational damage, employing a three-phase extortion strategy: ransom, sale, and leak. This model blends traditional ransomware with reputational attacks, including doxxing — leaking executives’ personally identifiable information (PII), such as Social Security Numbers and addresses, online.
On-chain TTPs
The group employs a direct laundering approach, funneling all victim proceeds into a single non-custodial exchange. This method minimizes transaction complexity, but underscores that the group uses limited obfuscation techniques and has a potentially recoverable cash-out strategy.
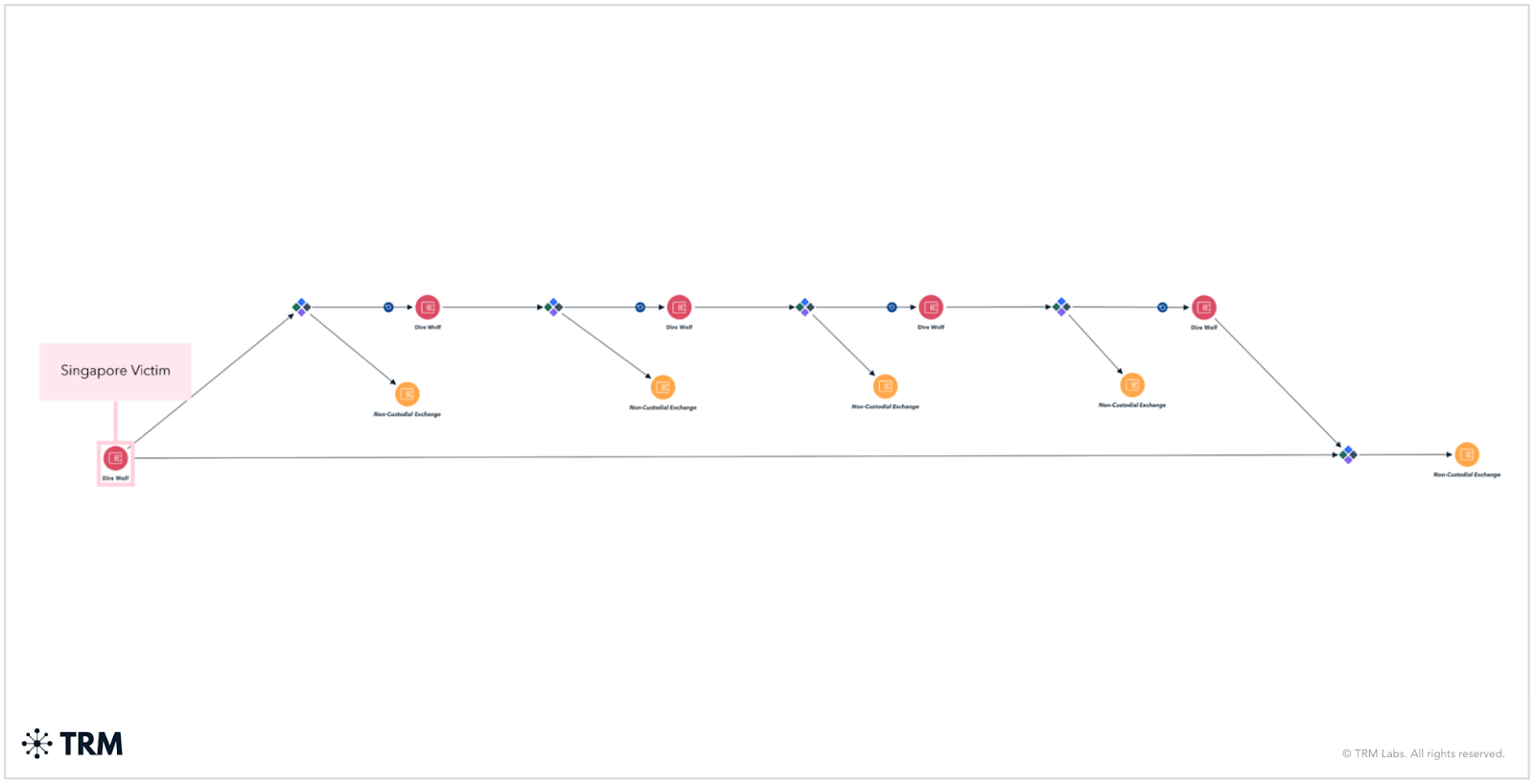
2. Dire Wolf
Known for targeted, high-impact intrusions across multiple industries; uses live dark-web negotiations; pushes proceeds through non-custodial exchanges
Dire Wolf has quickly established itself due to its highly targeted attacks and double-extortion tactics against a wide range of sectors and regions. It primarily targets the manufacturing and technology industries, but has also conducted attacks against healthcare, engineering, and construction organizations. Geographically, it has most frequently targeted the United States and Thailand, followed by Taiwan, Italy, and Australia.
Off-chain TTPs
The threat actor deploys a custom ransomware strain written in Golang — often obfuscated with UPX — that disables security tools, halts critical services, and deletes system recovery files to prevent detection and data restoration. It ensures only one instance runs at a time, uses strong encryption algorithms, and leaves a ransom note directing victims to a live dark web chatroom to negotiate payment.
On-chain TTPs
Dire Wolf typically launders victim proceeds downstream, making multiple deposits into a non-custodial exchange. This approach likely reflects a desire to quickly convert or swap assets without undergoing strict KYC procedures, allowing the group to maintain anonymity while moving funds across chains or into privacy-enhancing assets.
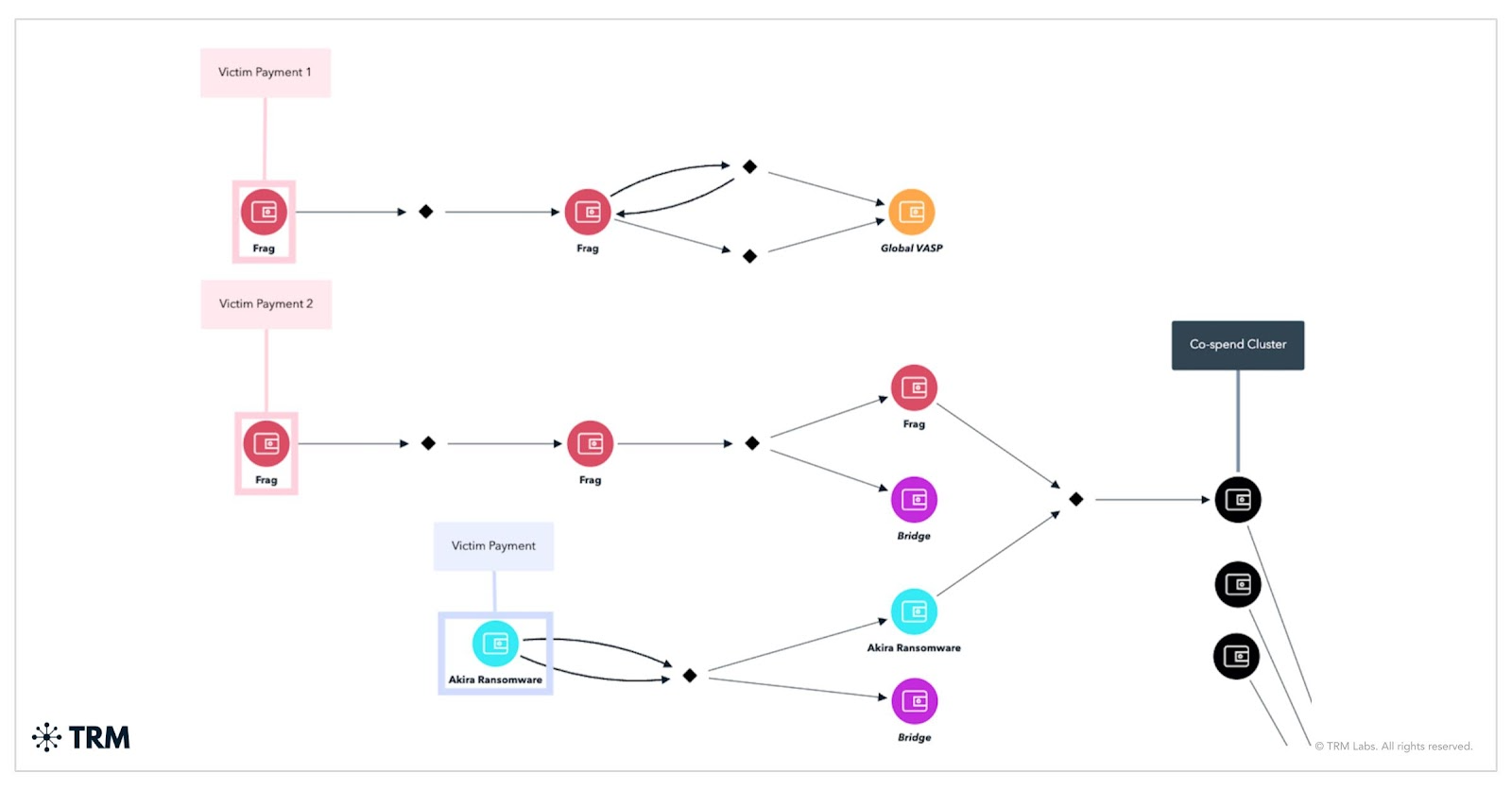
3. Frag
Rapid expansion tied to Akira and Fog; exploits high-value vulnerabilities; shares wallets and laundering services with Akira
TRM’s recent blog post on Embargo Ransomware highlighted that ransomware groups often have on-chain links to other threat actors, underscoring the interconnected nature of the ecosystem. One such group is Frag, which we assess may be linked to threat actors Akira and Fog.
Following Frag’s first reported victim in February 2025, AmeriKen Die Supply — a manufacturer of die cutting tools and materials — the group has quickly scaled operations. By March, it had claimed 27 organizations — 25 of which were in the US — across the manufacturing, transport, and aviation sectors.
Off-chain TTPs
Frag exploits the Veeam vulnerability (CVSS 9.8), often using compromised virtual private network (VPN) credentials without multi-factor authentication. Frag uses these credentials to gain access, create rogue administrator accounts, and deploy ransomware with a .frag extension, leveraging Living off the Land Binaries (LOLBins) for stealth and double extortion. LOLBins are legitimate system tools that threat actors repurpose for malicious activity, enabling them to evade detection by blending in with normal system processes.
On-chain TTPs
TRM has previously identified Frag routing funds through an intermediary address before depositing the full victim payment directly to a global VASP. As of the time of publication of this piece, TRM assesses that Frag may represent an extension of the Akira ransomware group. Both actors utilize a shared two-address wallet cluster and the same bridge and payment service previously employed exclusively by Akira to launder victim proceeds between late 2024 and June 2025. Frag also has on-chain overlaps with the threat actor Fog, which suggests it collaborates or shares tools with the group.
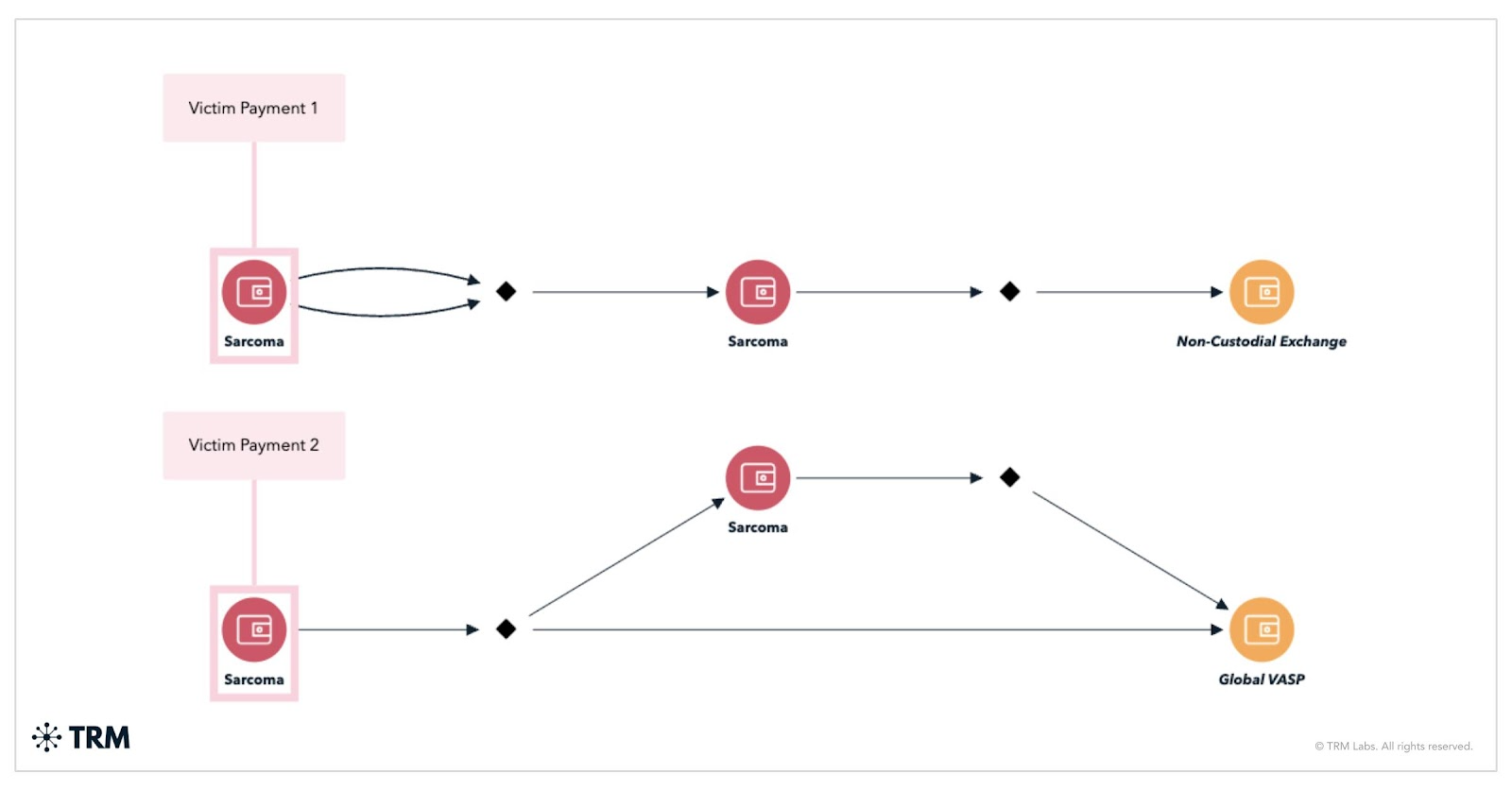
4. Sarcoma
Targets mid-market firms across North America and Europe; avoids certain regions, suggesting Eastern European base; cashes out via minimal laundering steps
Instead of conducting “Big Game Hunting” — targeting high-profile or high-revenue organizations to gain notoriety and potentially get media coverage — Sarcoma typically focuses on mid-market companies with revenues between USD 1 million and USD 10 million. Since it was first detected in October 2024, Sarcoma has quickly established itself as a major threat due to its aggressive tactics and high success rate across multiple sectors. It primarily targets organizations in the US as well as Italy, Canada, and Australia.
Off-chain TTPs
Sarcoma gains access using custom exploits and remote monitoring tools, then moves across networks by scanning devices and spreading through shared folders. It evades detection by erasing its tracks and encrypting files while leaving behind ransom notes in each affected folder, and uses double extortion. The group also deliberately avoids infecting systems in Uzbekistan, which indicates the group is potentially based in the country or in Russian-speaking regions of Eastern Europe and Central Asia more broadly.
On-chain TTPs
Sarcoma employs a straightforward laundering methodology, routing victim funds through a single intermediary address before depositing the full amount to a global VASP or non-custodial exchange. For investigators, the group’s minimal layering approach indicates limited obfuscation, increasing the likelihood that funds could be traced, intercepted, or recovered.
Groups with suspected ties to state actors
5. AiLock
Markets itself as AI-driven; pressures victims by threatening regulators and competitors; moves ransom through Wasabi mixer and Monero
First identified in April 2025, AiLock is suspected of being AI-assisted and deliberately markets itself as such. Groups publicly embracing AI will likely lead to other threat actors doing so at scale, underscoring the need for behavior-based detection, AI-driven intelligence, and zero-trust defenses.
Off-chain TTPs
The group’s TTPs include employing polymorphic malware for defense evasion. AiLock’s aggressive extortion tactics extend beyond data encryption; it explicitly threatens to report breaches to regulators and victims’ competitors. The group also gives victims tight deadlines — 72 hours to respond and five days to pay — threatening to leak or destroy the recovery tool while paradoxically offering promises of confidentiality and even IT advice.
On-chain TTPs
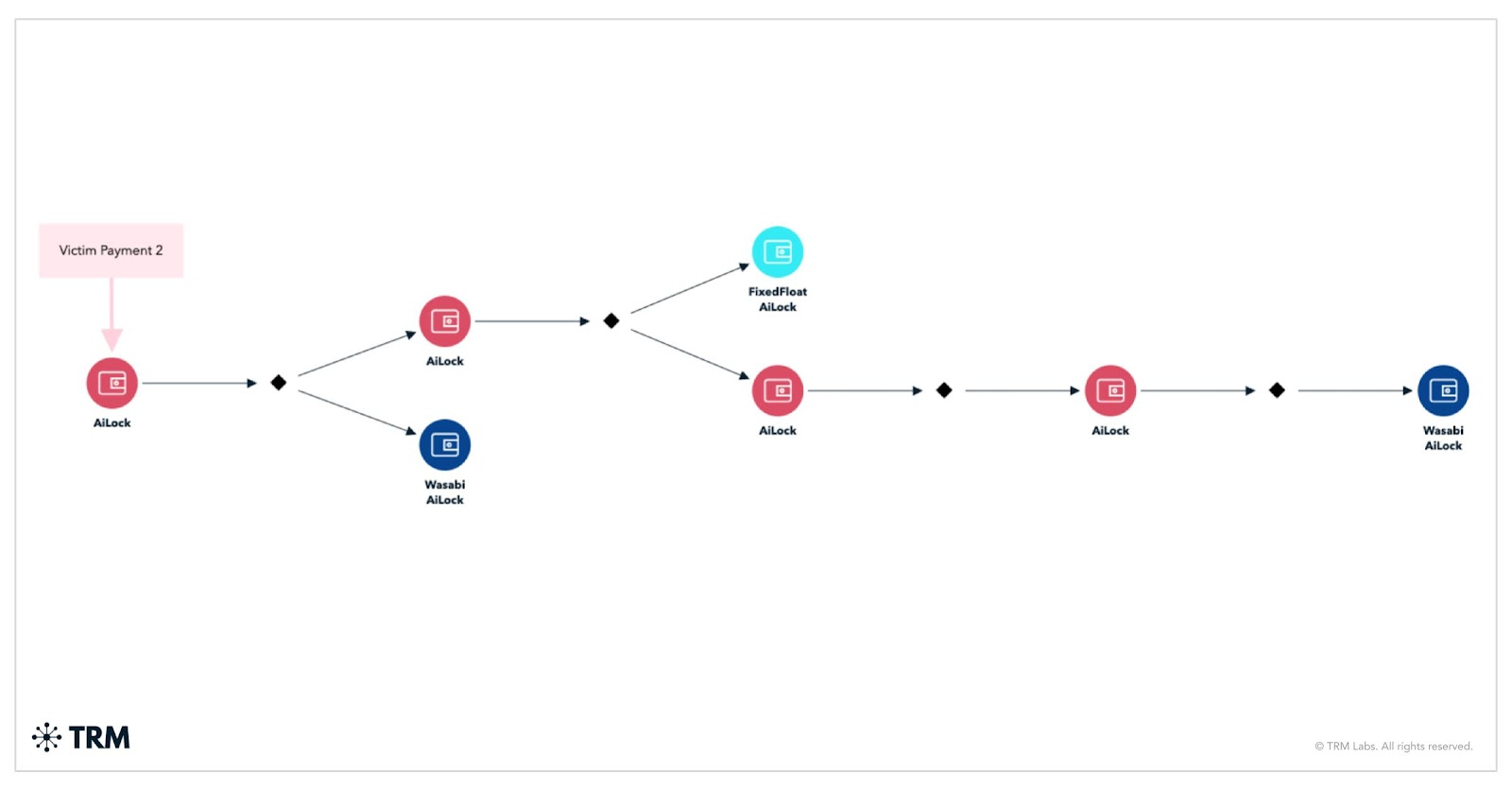
AiLock launders victim funds through a standard peel chain pattern, with the majority directed to the Wasabi mixer and a smaller portion routed to high-risk, non-custodial exchange FixedFloat. The threat actor frequently converts the funds deposited to FixedFloat into Monero before cashing out or further laundering them through subsequent conversions.
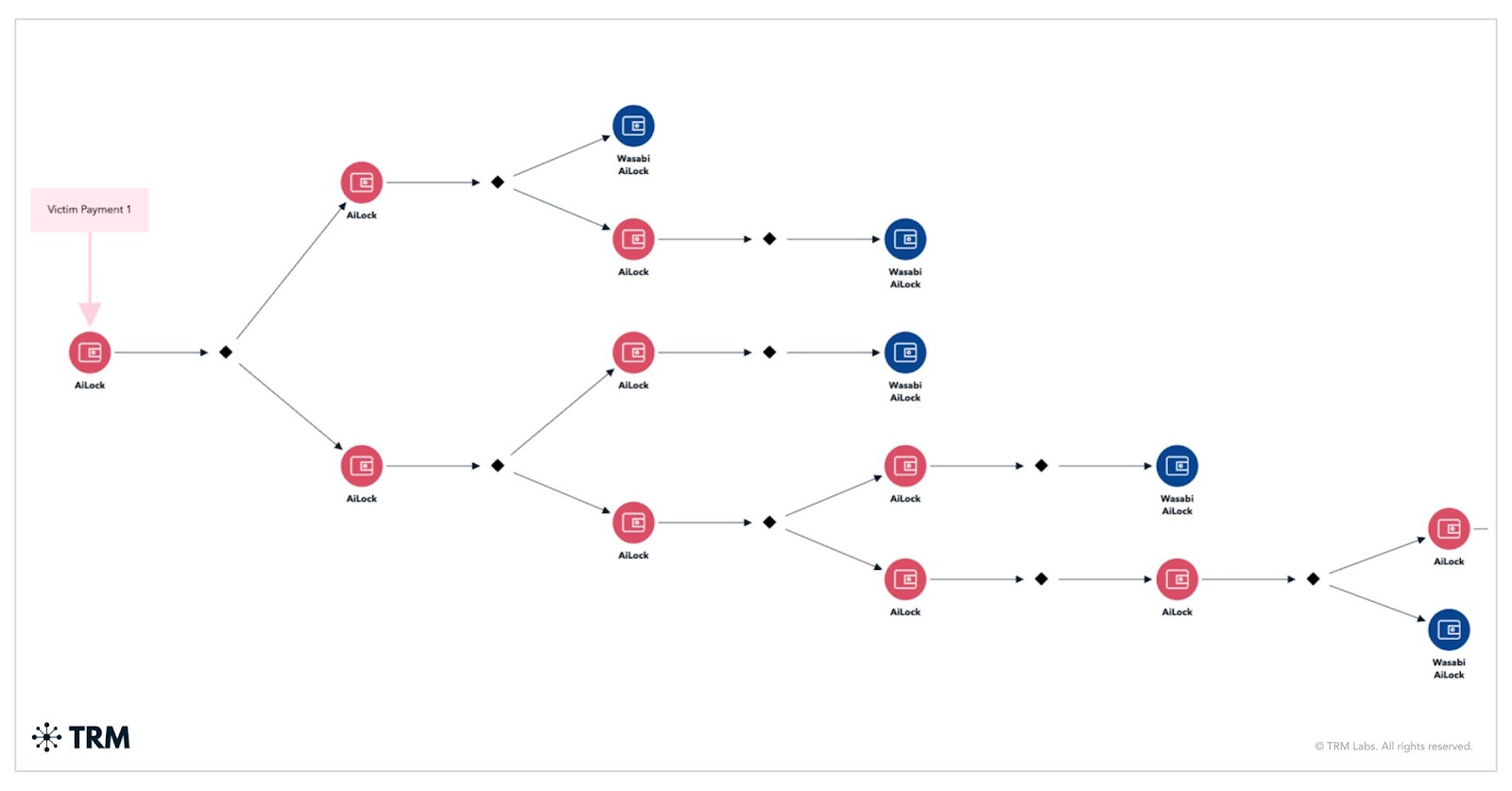
6. APTLock
Believed to be linked to Russian state group Fancy Bear; destructive attacks suggest strategic aims; launders payments into Monero
Ransomware is an increasingly attractive attack vector for state actors, as it serves as both a revenue source and disruptive tool. This dynamic is contributing to an increasing convergence between financially motivated cybercrime and nation-state activity. State-sponsored groups likely collaborate with financially motivated cybercriminals to maximize the potential of campaigns as well as pooling resources.
One group that is reportedly linked to Russian state-sponsored group UAC-0063 (also known as Fancy Bear) is APTLock. First identified in February 2025, researchers assess that APTLock is expanding its operations across sectors and regions, with a particular focus on high-revenue organizations that it perceives as more likely to pay large ransoms.
Off-chain TTPs
The group typically gains initial access through phishing campaigns and employs advanced detection evasion techniques such as rootkits, bootkits, and security tool disabling before stealing credentials and gathering system information. It both encrypts and deletes data, causing service disruption and defacing systems. The destructive element suggests the group may have strategic rather than purely financial motivations.
On-chain TTPs
APTLock launders victim proceeds through long peel chains, characterized by dozens of uniform-value deposits into Fixed Float, likely to facilitate conversion into Monero. This approach indicates the group likely intends to leverage anonymity-enhancing assets while maintaining standardized laundering patterns. The large transfer to a non-custodial exchange introduces potential seizure or recovery opportunities.
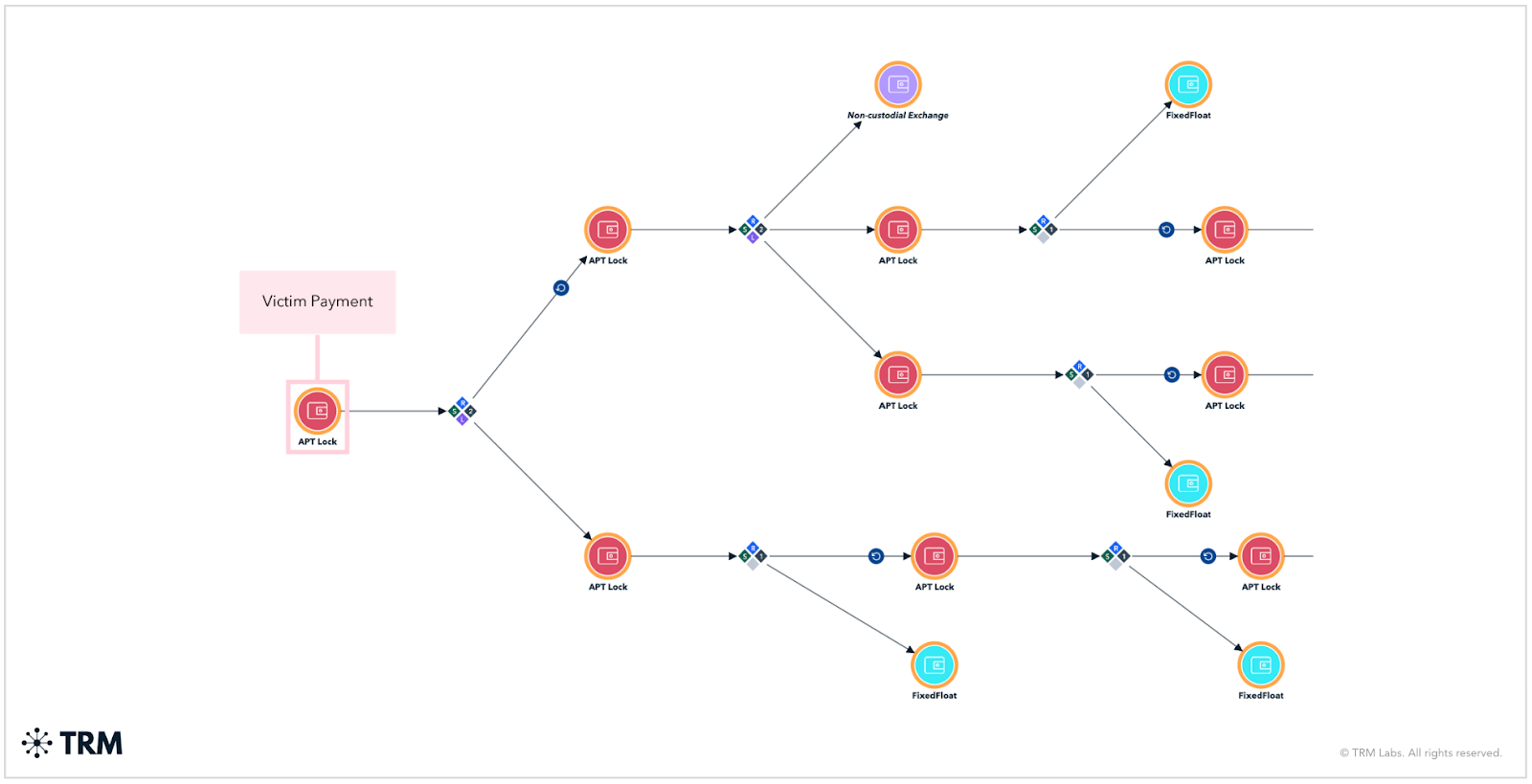
Groups that are quickly gaining traction
7. Kairos / Kairos V2
Focuses only on data theft and extortion; buys network access from brokers; laundering overlaps with Qilin, Lynx, and SafePay
Another group that TRM has identified with on-chain links to other threat actors is Kairos. The group has been active since late 2024, and as of August 2025 has claimed around 13 victims under the Kairos name and 50 under Kairos V2, predominantly in the US. It typically targets the healthcare, manufacturing, and business services sectors.
Off-chain TTPs
Unlike traditional ransomware groups, Kairos doesn’t encrypt data, but focuses solely on exfiltration and extortion, threatening to publish stolen files if victims don’t pay ransoms. This reflects a broader trend: according to research from Sophos, a cybersecurity firm, only half of ransomware attacks now involve encryption, the lowest level in six years. Kairos streamlines its operations by purchasing access from initial access brokers (IABs), threat actors that specialize in gaining unauthorized access to victims and selling this access.
On-chain TTPs
We have observed Kairos using various laundering patterns, depending on the payment. The following three use cases illustrate the group’s varying approaches:
- In one case, funds were funneled through long peel chains, with dozens of small offshoot deposits sent to multiple VASPs and payment services, and to high-risk exchange Aifory Pro.
- Another payment involved co-spend cluster transactions before large deposits were made to two global VASPs.
- A third example routed nearly the entire payment directly to a single global VASP address — an address also used by SafePay, INC, and Qilin to cash out victim funds. Additional shared cash-out points connect Kairos with SafePay, INC, Lynx, and Qilin — the first three being interlinked ransomware groups — pointing to the likelihood of a shared affiliate active among them.
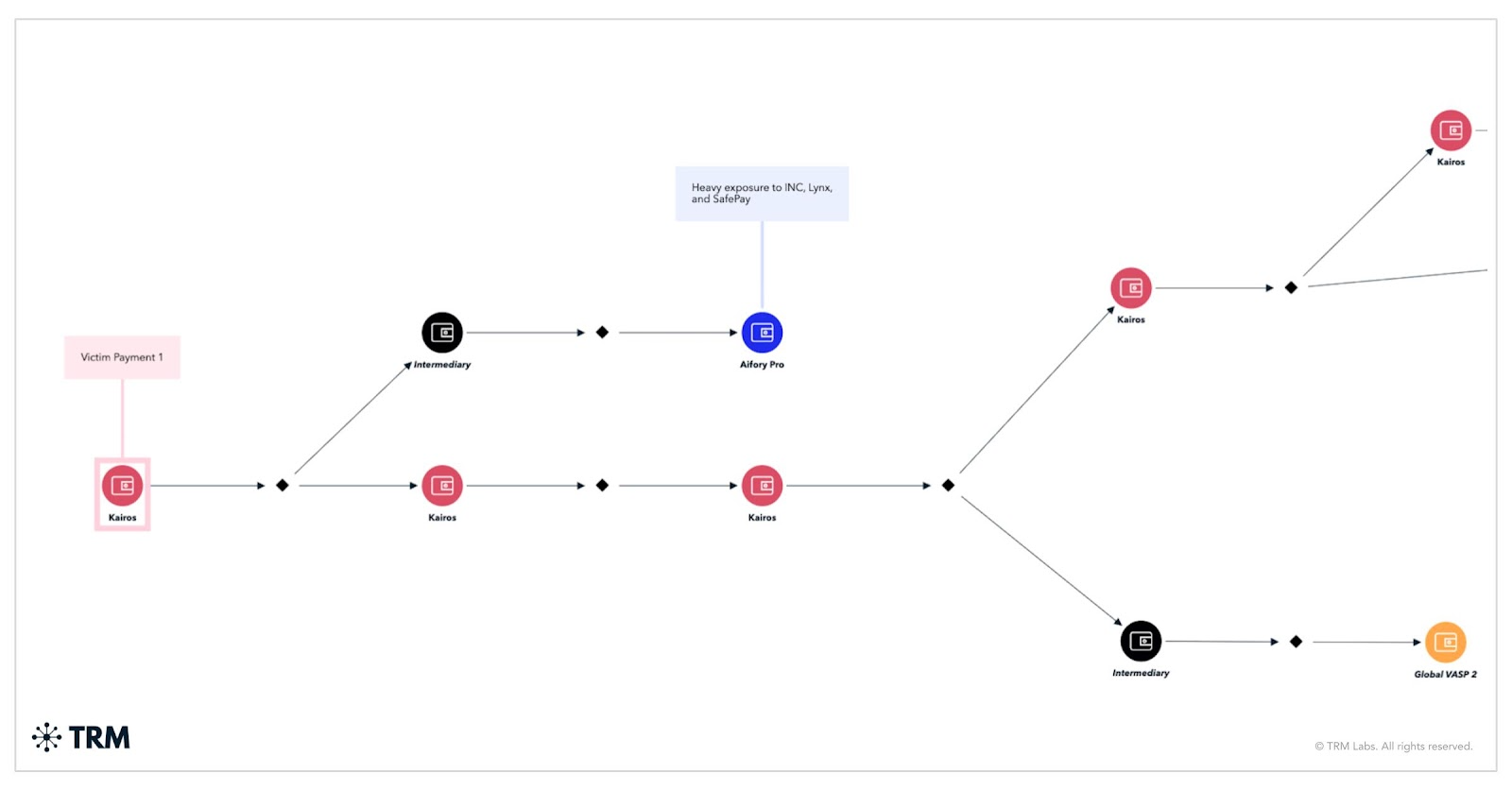
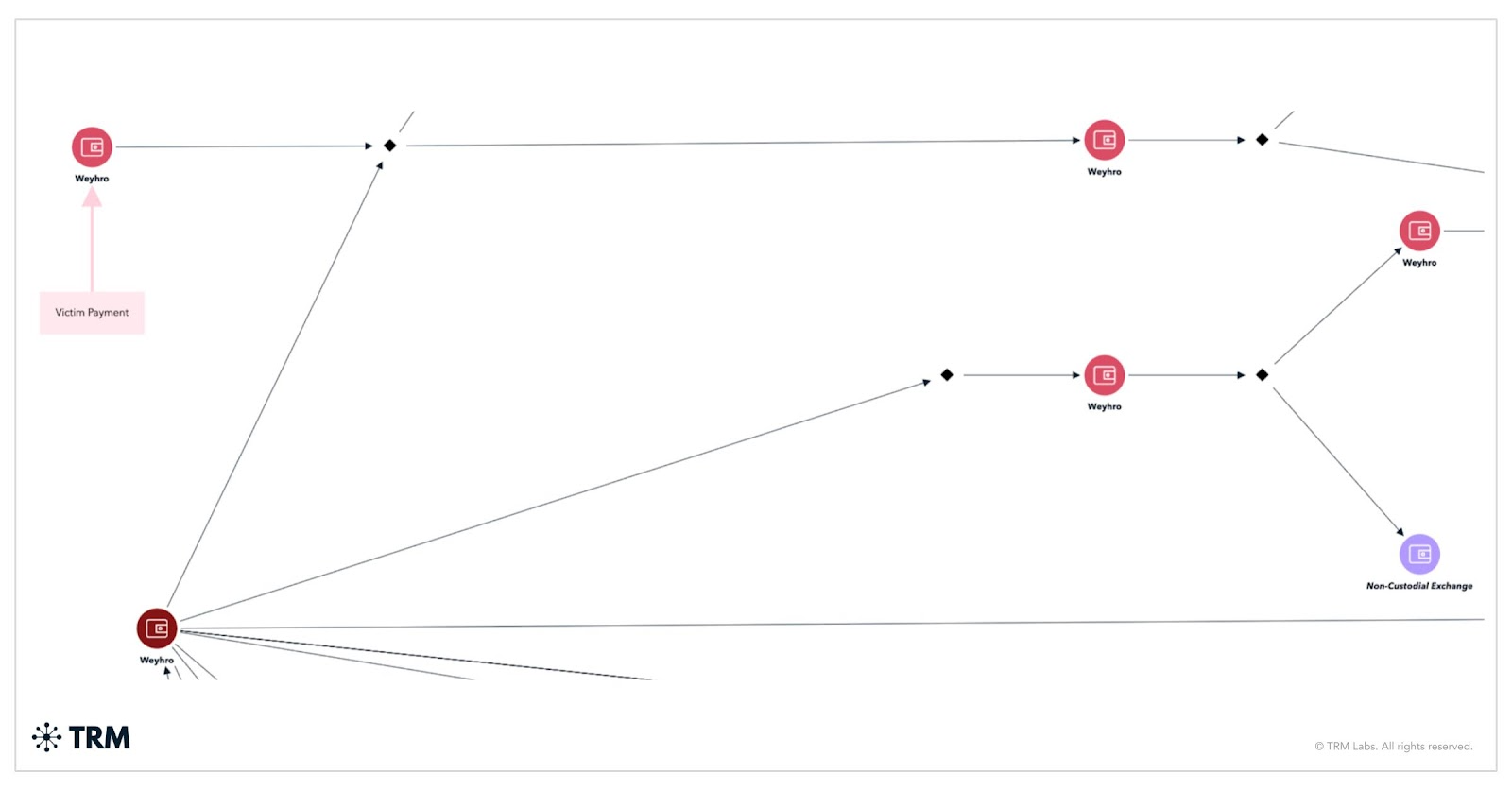
8. Weyhro
Carefully planned intrusions followed by leak-site pressure; international victim set; employs distinctive interconnected laundering patterns
Focusing on deliberate, high-impact attacks rather than opportunistic ones, Wehryo has rapidly emerged since late 2024 on underground forums like XSS and Exploit. Before encryption, Wehyro conducts extensive reconnaissance — identifying critical data and recovery options. In March 2025, the group launched a leak site with victims in the US, Italy, and Canada.
Off-chain TTPs
Weyhro gains initial access through phishing or exploiting outdated systems. Once inside a network, Weyhro encrypts critical files and systems to block access and searches for backups to disable, making recovery more difficult. It also uses the victim’s own computer resources to carry out its attack, which can slow down performance and leave behavioral clues for defenders or investigators monitoring for unusual activity. The group uses double extortion to pressure victims to pay.
On-chain TTPs
Wehyro’s laundering process leverages numerous intermediary and consolidation addresses before moving funds or cashing out through a mix of global VASPs, non-custodial exchanges, and payment services.
In one instance, TRM’s on-chain analysis identified a Weyhro victim payment linked to a small wallet cluster that exhibited a distinctive interconnected laundering pattern, resulting in the appearance of multiple outgoing transactions following the initial deposit.
9. Termite
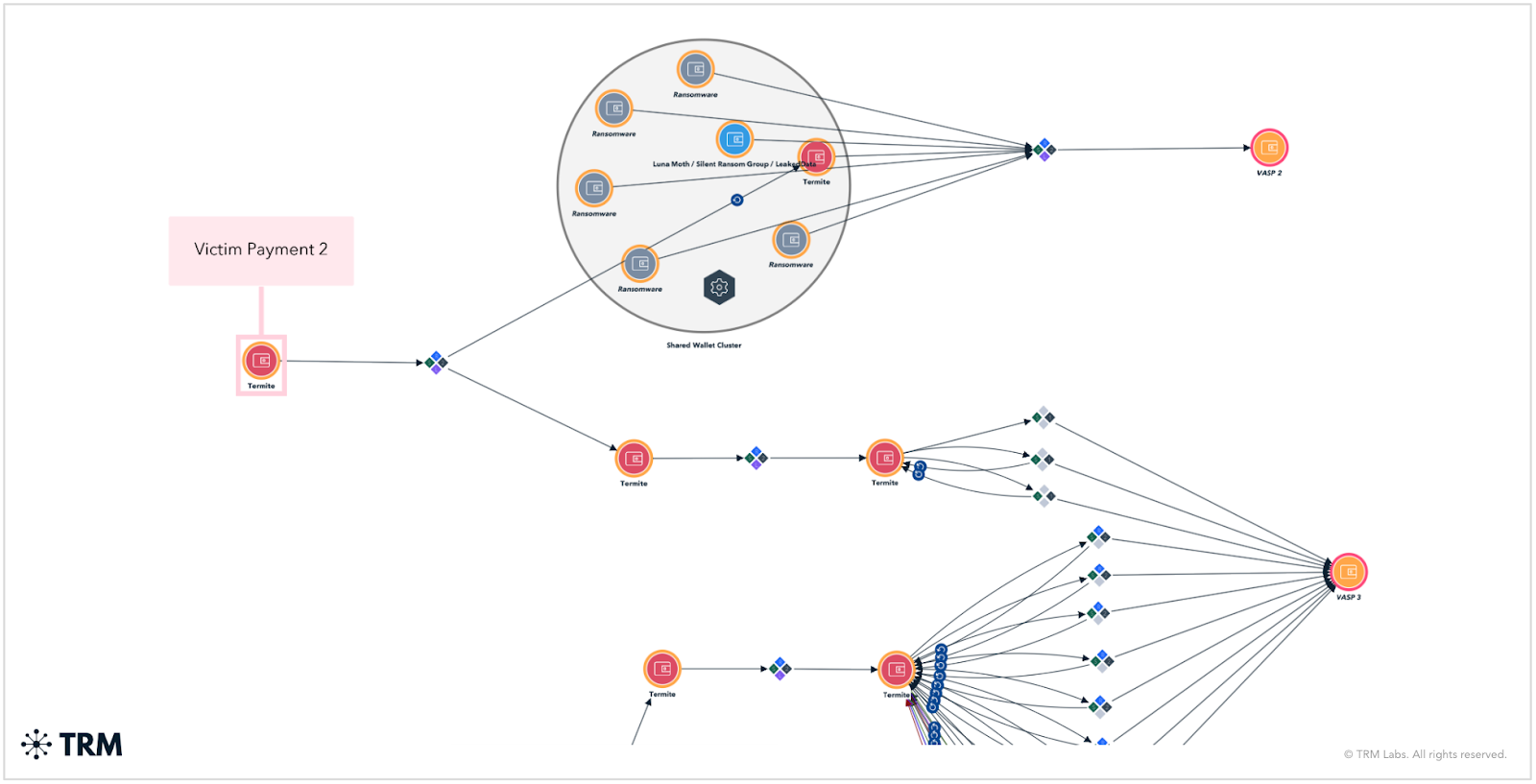
Widely assessed as a Babuk rebrand; high-profile victims include supply-chain and healthcare; reuses addresses across high-risk exchanges
Widely assessed to be a rebranding of Babuk ransomware, Termite operates as a closed group rather than a ransomware-as-a-service (RaaS) operation, in which groups provide affiliates with the tools to conduct attacks in exchange for a share of the ransom proceeds. Notable victims include supply chain vendor Blue Yonder and Australian fertility clinic Genea, whereby Termite exfiltrated 940 gigabytes of sensitive patient data.
Off-chain TTPs
Termite typically gains access through phishing or by exploiting vulnerabilities and spreads by enumerating network shares and mapped drives. To maximize impact and prevent recovery, it encrypts remote files, drops widespread ransom notes, deletes shadow copies, and disables backup, security, and database services while using anti-analysis tools to evade detection. The group has demonstrated capabilities in exploiting internet-facing systems and edge devices — hardware that connects a private network to the internet, such as routers, firewalls, or Internet of Things (IoT) devices.
On-chain TTPs
Termite uses a straightforward process to launder funds — making direct deposits to multiple VASPS and re-using shared cash-out addresses across payments. TRM has identified additional activity, including making deposits to high-risk exchanges such as bixter[.]org, Heleket, and @luckyvlg, as well as CSS — converting bitcoin into Ethereum and TRON before cashing out.
Looking ahead
As machine learning-enabled ransomware that better evades detection and RaaS models continues to democratize the cybercrime landscape, the ransomware ecosystem is becoming more fragmented — but no less dangerous. Opportunistic actors now operate alongside experienced threat groups, adapting quickly to law enforcement disruptions and shifting laundering tactics through cross-chain swaps and high-risk exchanges.
TRM assesses that ransomware will increasingly move beyond file encryption, pivoting to extortion campaigns that target reputational, regulatory, and operational pressure points — tactics that offer higher leverage with less technical overhead. The increasingly blurred distinction between financially motivated attackers, nation-state proxies, and hacktivists will further complicate attribution and responses.
Blockchain intelligence firms like TRM play a critical role in helping to combat such threat actors. By tracing ransomware payments on-chain, identifying laundering patterns, and supporting law enforcement and investigative teams with actionable intelligence, TRM helps disrupt illicit financial flows and accelerate response.
{{horizontal-line}}
About TRM Labs
TRM Labs provides blockchain analytics solutions to help law enforcement and national security agencies, financial institutions, and cryptocurrency businesses detect, investigate, and disrupt crypto-related fraud and financial crime. TRM’s blockchain intelligence platform includes solutions to trace the source and destination of funds, identify illicit activity, build cases, and construct an operating picture of threats. TRM is trusted by leading agencies and businesses worldwide who rely on TRM to enable a safer, more secure crypto ecosystem. TRM is based in San Francisco, CA, and is hiring across engineering, product, sales, and data science. To learn more, visit www.trmlabs.com.
Access our coverage of TRON, Solana and 23 other blockchains
Fill out the form to speak with our team about investigative professional services.






















